Cannot make any queries in GraphiQL without x-hasura-admin-secret
Version Information
Server Version: 2.9.0 (however in the console the label displays as v2.0.8) CLI Version (for CLI related issue):
Environment
Local development, in Hasura Console running in Docker. Using Chrome 104.0.5112.79 to access Hasura Console
What is the current behaviour?
When removing the x-hasura-admin-secret request header key I no longer have access to any items in the Explorer, and queries fail. The x-hasura-user-id & x-hasura-role are valid. Several tables have select permissions for this role without any checks so I'd expect something to be available in the explorer.
This was working for me previously, though I do not recall an exact timeframe. I use the feature when I need to test permission settings against queries.
What is the expected behaviour?
I should be able to make queries in GraphiQL without the admin-secret in order to simulate the requests from different roles and users.
How to reproduce the issue?
hasura console- Navigate to the Hasura Console in browser
- Expand
Request Headers - Uncheck
x-hasura-admin-secret - Add headers for
x-hasura-user-id&x-hasura-rolewith valid entries according to user table and roles - Observe an empty GraphiQL Explorer and failed queries.
Screenshots or Screencast
Note: the successful query response data on the right is from before removing the admin-secret in the header.

Example table (organization) does exist, with no checks on the select action for practitioner role:
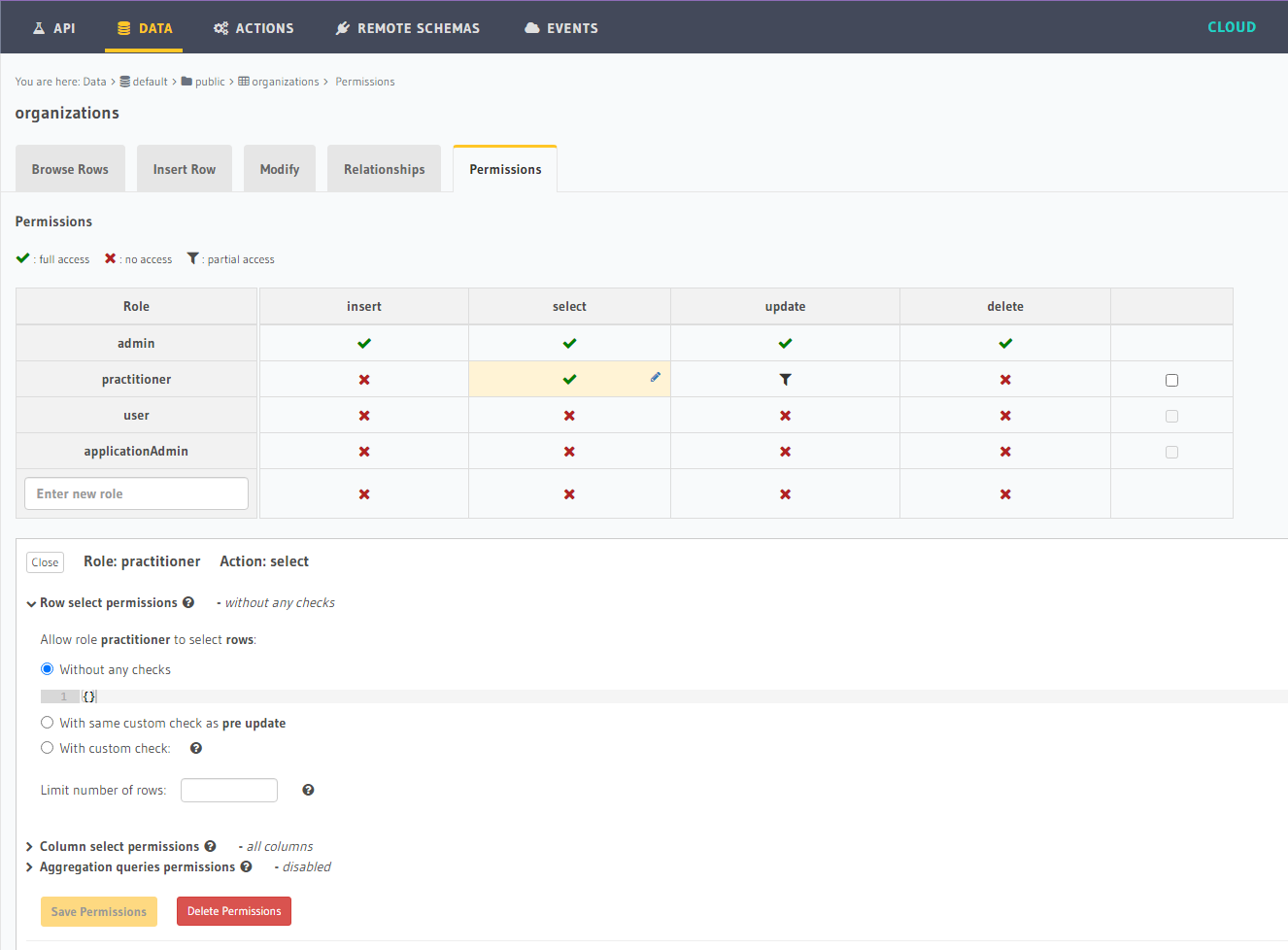
Please provide any traces or logs that could help here.
Error Message:
{
"errors": [
{
"extensions": {
"path": "$.selectionSet.organizations",
"code": "validation-failed"
},
"message": "field \"organizations\" not found in type: 'query_root'"
}
]
}
Any possible solutions?
Unknown.
Can you identify the location in the source code where the problem exists?
Unknown.
If the bug is confirmed, would you be willing to submit a PR?
Maybe
Keywords
GraphiQL, Explorer, Console, API, Request Headers, x-hasura-admin-secret, query_root
When removing the
x-hasura-admin-secretrequest header key I no longer have access to any items in the Explorer
This is expected behaviour. You can use the x-hasura-user-id & x-hasura-role headers to "pretend" to be that user-id and role only if you are an admin (which is determined by the admin-secret header).
Without the admin secret the only way to get access with a particular user-id and role is by providing a valid Authorization token. If not any user can send requests with headers as any role and user-id and get access to data they shouldn't have permissions to.
Please let me know if I misunderstood your request.
This is expected behaviour. You can use the
x-hasura-user-id&x-hasura-roleheaders to "pretend" to be that user-id and role only if you are an admin (which is determined by the admin-secret header).
When I have all three headers (role, user-id, and admin-secret) the explorer does not "pretend" I am that user, but rather gives me complete admin access to select all items from the database even if permissions disallow it for that user.
Additionally, examples given in the docs do not appear to use the admin-secret in the header: Link
When I have all three headers (role, user-id, and admin-secret) the explorer does not "pretend" I am that user, but rather gives me complete admin access to select all items from the database even if permissions disallow it for that user.
this is quite surprising and I am unable to reproduce this. could you confirm if you are still observing this. i am wondering if the explorer did not end up running the introspection query once the role info is updated.
Additionally, examples given in the docs do not appear to use the admin-secret in the header: Link
Thanks for pointing that out. thats definitely a miss.
Closing this for now. Feel free to reopen if there are further queries or if the unexpected behaviour is still observed