terraform-provider-azuread
 terraform-provider-azuread copied to clipboard
terraform-provider-azuread copied to clipboard
GroupType must be set to Unified for cloud groups assignable to roles
Community Note
- Please vote on this issue by adding a 👍 reaction to the original issue to help the community and maintainers prioritise this request
- Please do not leave "+1" or "me too" comments, they generate extra noise for issue followers and do not help prioritise the request
- If you are interested in working on this issue or have submitted a pull request, please leave a comment
Terraform (and AzureAD Provider) Version
Terraform version: 1.3.6 Azure AD provider version: 2.31.0
Affected Resource(s)
- azuread_group
Terraform Configuration Files
main.tf
# Terraform
terraform {
required_version = ">= 1.3.6"
required_providers {
azuread = {
version = ">= 2.31.0"
}
github = {
source = "integrations/github"
version = ">= 5.12.0"
}
}
}
# AzureAD Provider
provider "azuread" {
tenant_id = var.tenant_id
client_id = var.client_id
client_secret = var.client_secret
}
# GitHub Provider
provider "github" {
token = var.github_token
owner = var.github_organization
}
repository.tf
data "github_repository" "cmdb" {
full_name = "ITSTUD-IO/cmdb"
}
data "github_repository_file" "groups" {
repository = data.github_repository.cmdb.name
branch = "master"
file = "groups.yml"
}
groups.tf
resource "azuread_group" "group" {
for_each = {for group in yamldecode(data.github_repository_file.groups.content).group: group.name => group}
display_name = each.key
description = each.value.description
theme = each.value.theme
owners = [data.azuread_user.au_admin.object_id, data.azurerm_client_config.current.object_id]
types = ["Unified", "DynamicMembership"]
provisioning_options = ["Team"]
visibility = "Private"
mail_nickname = replace(each.value.name, " ", "")
mail_enabled = true
security_enabled = true
assignable_to_role = true
prevent_duplicate_names = true
dynamic_membership {
enabled = true
rule = each.value.membership_rule
}
}
groups.yml
group:
- 'Information Technology':
name: 'Information Technology'
description: 'Information Technology'
theme: Red
membership_rule: 'user.department -eq "Information Technology"'
Debug Output
Terraform v1.3.6 on linux_amd64 azuread_group.group["Information Technology"]: Creating...
Error: Creating group "Information Technology" with azuread_group.group["Information Technology"], on groups.tf line 1, in resource "azuread_group" "group": 1: resource "azuread_group" "group"
GroupsClient.BaseClient.Post(): unexpected status 400 with OData error: Request_BadRequest: GroupType must be set to Unified for cloud groups assignable to roles.
Operation failed: failed running terraform apply (exit 1)
Panic Output
Expected Behavior
Azure AD group - M365 group with dynamic membership - gets created as group type set actually contains "Unified".
Actual Behavior
Azure AD group creation errors.
Steps to Reproduce
terraform apply
Important Factoids
- using terraform cloud for deployment
- storing group configuraton in separate yaml file in a github repository (create an access token)
- define tenant access values in variables.tf file
References
After some investigation, following findings:
- when commenting out assignable_to_role and prevent_duplicate_names at least group creation works
- issue still exists, when updating the group later
- must be related to the known issues of Microsoft Graph group API, which is handled here: https://github.com/microsoftgraph/microsoft-graph-docs-contrib/issues/720
Hi @it-stud-io, thanks for reporting this and for the additional information. I am not sure why this is failing for you, when attempting to reproduce I do not encounter this error.
I have tried with both these test configs:
(security group)
resource "azuread_group" "test" {
assignable_to_role = true
display_name = "acctestGroup-assignableToRole-230118214956997811"
security_enabled = true
}
(M365 group)
resource "azuread_group" "test" {
assignable_to_role = true
display_name = "acctestGroup-assignableToRole-230118215427718310"
mail_enabled = true
mail_nickname = "acctestGroup-assignableToRole-230118215427718310"
security_enabled = true
types = ["Unified"]
}
and the permissions I am using (as far as I can tell, no directory roles have been assigned to my service principal):
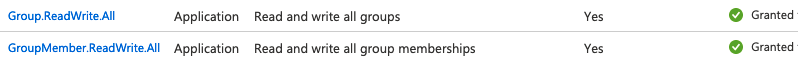
(marking as an API bug for now until we can get to the bottom of it)