Service Execution ATT&CK technique fails
Describe the bug
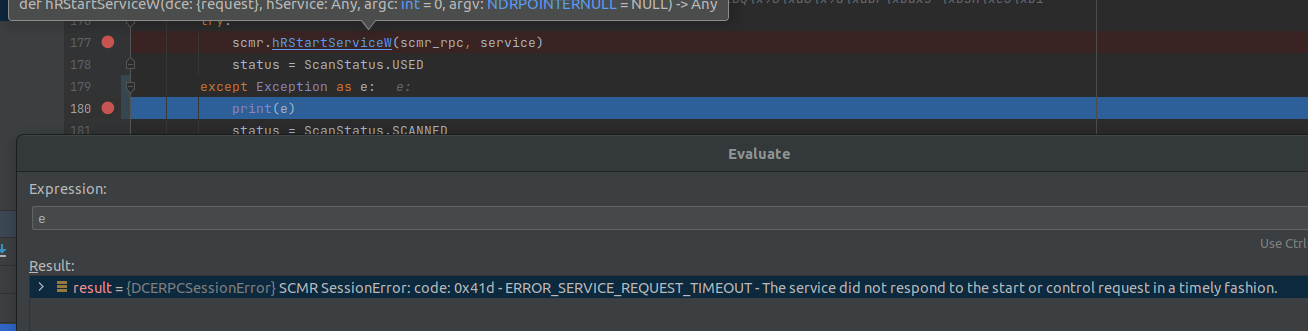
As Service Execution is mapped to SMB Exploiter, any machine that is going to be exploited with SMB needs to send telemetry that the Service Execution technique was successful, but it is not. MS-SCMR service from SMB exploiter throws exception SCMR SessionError: code: 0x41d - ERROR_SERVICE_REQUEST_TIMEOUT - The service did not respond to the start or control request in a timely fashion. is causing the telemetry to show fail but actually it is exploiting the victim. On top of this Service Execution is showing the Island machine as the machine that the SMB was tried on.
To Reproduce
Steps to reproduce the behavior:
- Configure Monkey to use SMB exploiter.
- Run the monkey to exploit Windows machine
- See ATT&CK report that the technique failed
In order to see the exception message in the description:
- Breakpoint on smb exploiter
- Run Monkey Agent from source.
- Check the Exception
Expected behavior
The Service Execution should pass when we run SMB exploiter and should show correct machine name.
Screenshots
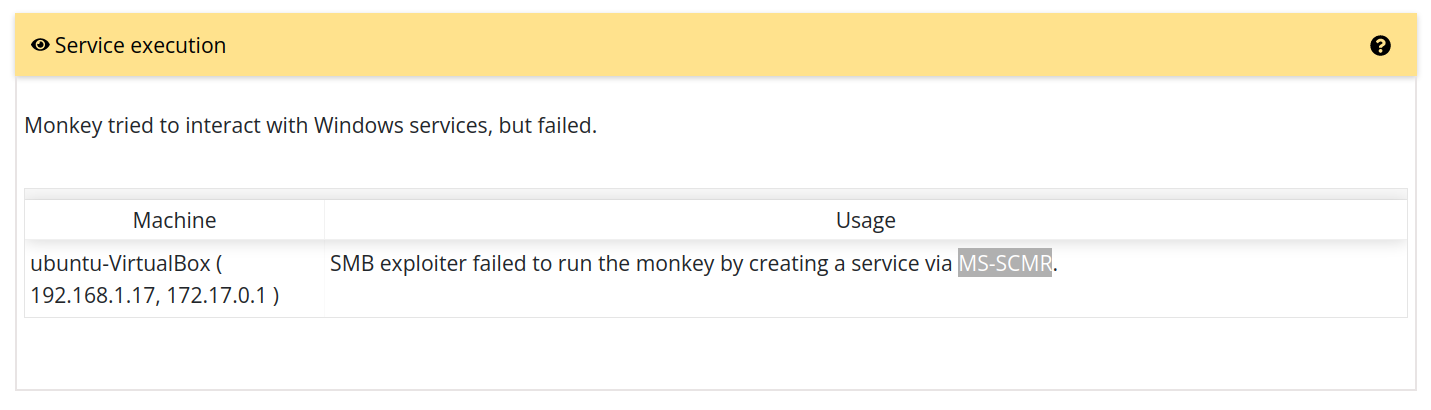
Machine version (please complete the following information):
- OS: Windows or Linux
@ilija-lazoroski Didn't we just test this 2 weeks ago?
@ilija-lazoroski Didn't we just test this 2 weeks ago?
I am not sure but I couldn't make it pass when I was doing the guide. Noticed that the telemetry is wrong as only Windows systems are relevant but it showed the Island machine name always and I couldn't make it pass.
ATT&CK report is getting removed in https://github.com/guardicore/monkey/issues/2440