How to use this plugin with OpenID Connect?
Can anyone help me in understanding how can we use this plugin in combination with kong-oidc? https://github.com/nokia/kong-oidc
If it works, then it would be full end-end in my guess. Getting accesstokens using oidc plugin and validation will be done for every request using kong-plugin-jwt-keycloak plugin.
Am I Correct? If not, please guide me.
This is not something that I have tried. It seems that the kong-oidc plugin is suppose to help kong facilitate the Authorization Code flow to eventually set a cookie in Kong that allows access. This is just my understanding from briefly reading the README of that repo. I could be wrong.
That being said, if you have a access token issued by keycloak at the end of the flow the kong-oidc does, you can use the kong-plugin-jwt-keycloak plugin to validate it. In general, the kong-plugin-jwt-keycloak plugin does not care what flow was used to obtain the access token.
But usually, kong is executing all plugins in parallel. This makes me trouble in making your plugin work with kong-oidc.
Did you get any chance to use both? If so, can you help me.
As per the code, your plugin priority is 1005 and kong-oidc is 1000 i.e., kong-plugin-jwt-keycloak will be executed before kong-oidc. Am I correct?
That is correct. This plugin has the same execution priority as the vanilla JWT plugin from kong. So kong-plugin-jwt-keycloak will run before kong-oidc. I can see how would pose a problem. Feel free to fork and change the execution priority to fit your needs.
im trying to do this as well. Im a bit confused how to chain them together though.
After kong delegate the authentication via oidc to keycloak 1 -> user types in username and password 2 -> keycloak calls back kong and adds the roles and realms 3 -> at this point, kong proxies to the upstream
it seems we need to intercept at between steps 2 and 3, and check the roles before kong proxies to the upstream. Am i getting something wrong here? how does just changing the execution priority help? because kong is going to proxy to the upstream immediately ?
This plugin is to validate tokens issued by Keycloak. How users obtain those tokens is not within the scope of this project. The Nokia plugin, by the looks of it, uses cookies to keep track of the sessions.
If there an access token issued by keycloak send to kong on the request to the upstream, my plugin should work. If that is so I would think you have to change the execution priority of my plugin. Did that work @mssaisandeep ?
I have not used the kong-oidc plugin and do not know the details of that implementation. I wont be trying it out now, simply because I do not have the time to do it. If somebody has managed to make this work, please post instructions :)
I didn't try it yet. This week I am going to do it and will update you the status
@gbbirkisson I can confirm that without changing the priority as you mentioned, it did not work, however once I used a much lower number as priority(in my case 10) it did work perfectly and I could then verify the roles and other claims. Is it possible to make this configurable somehow? For now I just have to fork the project.
@dpasdar Hey could you please share in detail about how you make it verify roles and claims from keycloak?
@dpasdar Hey could you please share in detail about how you make it verify roles and claims from keycloak?
As mentioned, all I have done is changing the priority to 10 and setting up the plugin in my route after the OIDC plugin. If the OIDC introspection URL is correct and the token is validated and enriched with extra information (e.g real_roles, scopes etc), it can then be verified using this plugin. In our case we have an extra layer of authorization using the realm_roles to block users from accessing certain backend_api's. If you want to test it quickly with my configuration; for instance in your docker-file; you can use the forked version of this repo with my username (https://github.com/dpasdar/kong-plugin-jwt-keycloak) . The rockspec file there is modified to point to the correct commit version.
@gbbirkisson I just have one question: If I invalidate session in keycloak, will the token be invalidated and considered session logout by this plugin? if not, how can we acheive this?
@dpasdar Hey did you tried to make this plugin work with Nokia's kong-oidc plugin? I am getting BAD Token Error as shown below. If you could able to make it work, please let me know. BTW I understand the problem, As Nokia OIDC plugin is converting this to the opaque token and this plugin can understand only JWT token. Because of this, I am getting this issue. Am I correct?
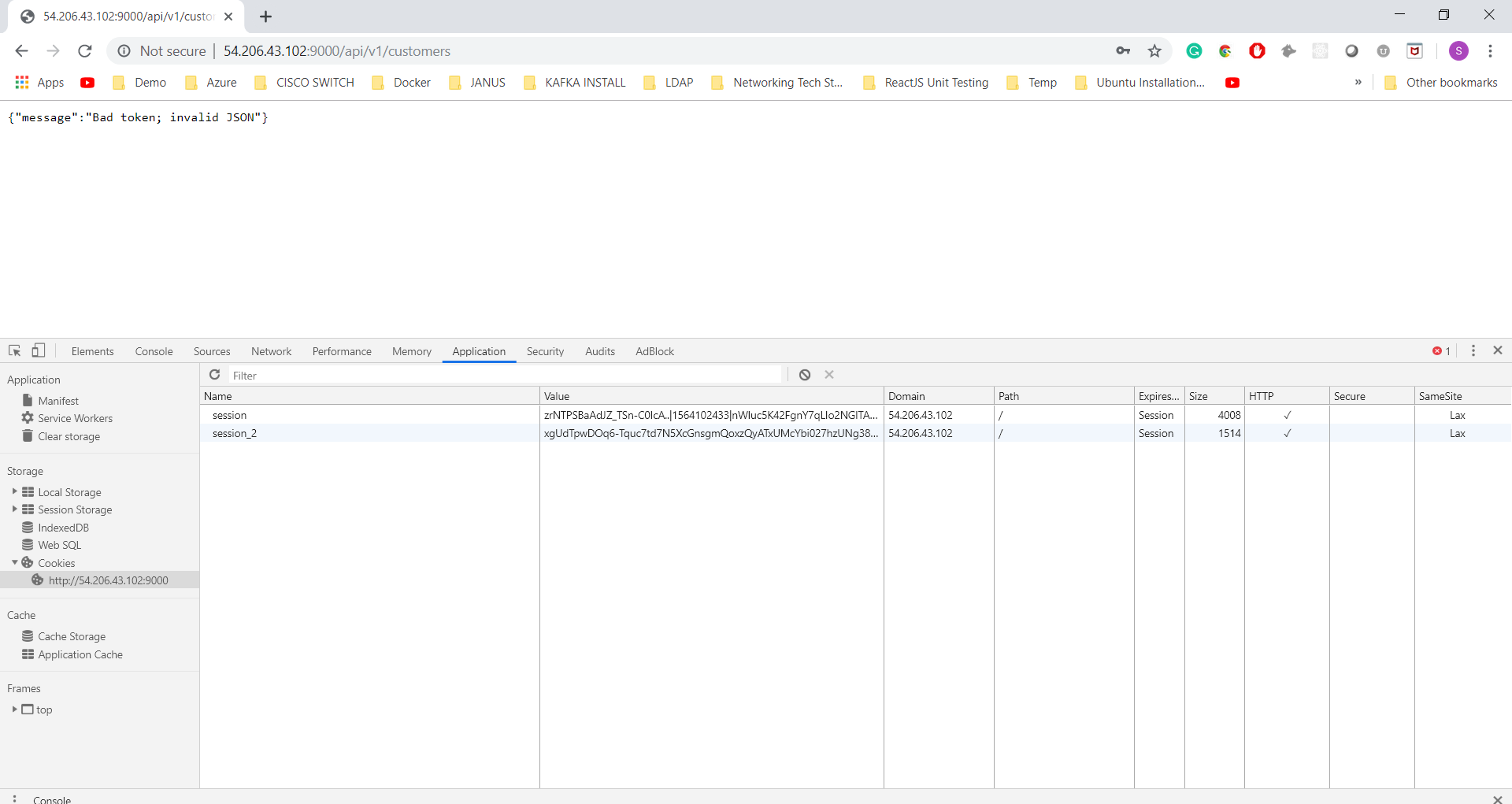
Thanks
@mssaisandeep I think you have probably misconfigured a part of your Keycloak + Kong workflow, as I mentioned it works amazingly for us, and it consumes and validates proper JWT tokens. I don't know your exact workflow, but generally you need a pair of public clients and confidential clients in keycloak side with proper configuration to connect kong and the REST backend API and Keycloak together. A quite helpful 2-Part tutorial (including debugging instructions) which is very similar to our approach can be found here : https://www.jerney.io/secure-apis-kong-keycloak-1/
I am successfully able to build, pack and use this plugin along with nokia-oidc plugin. I am facing one issue, could anyone please have a quick look and let me know what will be the issue:
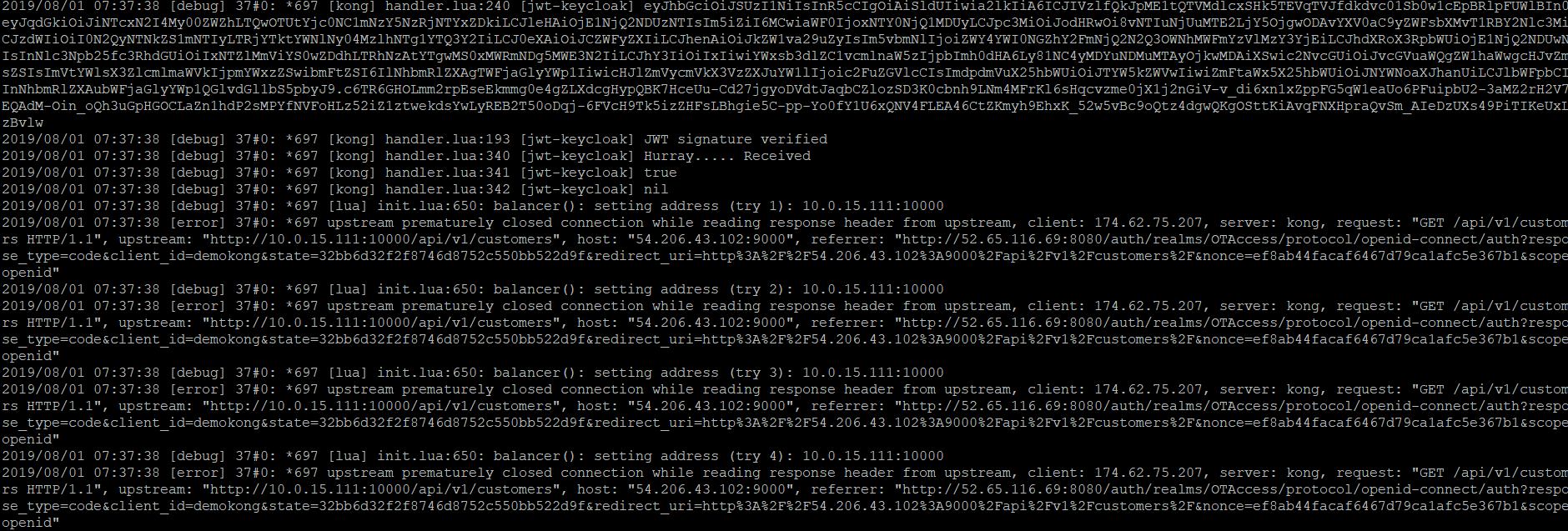
If you check the 2nd image which has kong debug logs. I received the access token from OIDC plugin and get successfully verified after that, I am getting the issue. What may be the problem?
Please help me. Thanks...
BTW FYI, I already checked the API (Upstream). It is not even receiving the request.
@gbbirkisson I just have one question: If I invalidate session in keycloak, will the token be invalidated and considered session logout by this plugin? if not, how can we acheive this?
No it does not take that into account. The plugin only validates tokens with public keys and roles. Only way to achieve this is to have access token expiration short.
Hey guys, I have finally added a env variable to be able to change the plugin priority. My next step was to create a demo on how to use this plugin with the oidc one.
I have started a branch with the demo: https://github.com/gbbirkisson/kong-plugin-jwt-keycloak/tree/oidc/demo/nokia-oidc
@dpasdar I was wondering if you are willing to help me with the demo seeing you have done this already. I would greatly appreciate it.
Cheers
Hey guys, I have finally added a env variable to be able to change the plugin priority. My next step was to create a demo on how to use this plugin with the oidc one.
I have started a branch with the demo: https://github.com/gbbirkisson/kong-plugin-jwt-keycloak/tree/oidc/demo/nokia-oidc
@dpasdar I was wondering if you are willing to help me with the demo seeing you have done this already. I would greatly appreciate it.
Cheers
@gbbirkisson sure, just let me know how I can help you in that regard.
Hello, did any progress happen in this regard? I'm dealing with the same problems with kong-oidc and would like to somehow jerryrig a token validation into it.
Hi, I have a problem with kong-plugin-jwt-keycloak and kong-oidc pair.
In case when I get JWT access_token as result POST (https://keycloak/auth/realms/xxxx/protocol/openid-connect/token) and then do request for my resource with Authorization: Bearer $token all works perfect
But, in case request for my resource is in the browser I get success with oidc flow
openidc.lua:1155: authenticate(): OIDC Authorization Code Flow completed -> Redirecting to original URL
and fail ("Unauthorized") in
[jwt-keycloak] do_authentication() -> retrieve_token() step.
Kong-oidc plugin stores the tokens in an encrypted cookies.
In kong-plugin-jwt-keycloak we can set conf.cookie_names which will be checked In retrieve_token() method.
Unfortunately I have failed with decode data
local cookie_session = var["cookie_session"]
local decoded_cookie_session = ngx.decode_base64(cookie_session)
local json_decoded_cookie_session = cjson.decode(decoded_cookie_session)
the decoded_cookie_session var is nill
I found a way how to use data from kong-oidc plugin in kong-plugin-jwt-keycloak plugin
In oidc code
function handle(oidcConfig)
...
if (response.user) then
utils.injectUser(response.user)
end
if (response.access_token) then
utils.injectAccessToken(response.access_token)
end
if (response.id_token) then
utils.injectIDToken(response.id_token)
end
...
end
It means they (id and access tokens) can be used in jwt-keycloak.
They are available for requests as
kong.request.get_header
and we can get pure payload from JWT.
Obviously it’s required some code improvements
Hi @Agihi I've added some improvements here https://github.com/PSheshenya/kong-plugin-jwt-keycloak
@Agihi
The token introspection feature of nokia/kong-oidc validates tokens, it would help you ?
I can confirm that @PSheshenya solution works absolutely fine (OIDC + JWT Token). I added a minor fix for X-Access-Token header processing.
Dockerfile:
FROM kong:2.0.3-alpine
LABEL description="Alpine + Kong 2.0.3 + kong-oidc plugin"
ENV OIDC_PLUGIN_VERSION=1.1.0-0
ENV JWT_PLUGIN_VERSION=1.1.0-1
USER root
RUN apk update && apk add git unzip luarocks
RUN luarocks install kong-oidc
RUN git clone https://github.com/PSheshenya/kong-oidc.git \
&& cd kong-oidc \
&& luarocks make
RUN luarocks pack kong-oidc ${OIDC_PLUGIN_VERSION} \
&& luarocks install kong-oidc-${OIDC_PLUGIN_VERSION}.all.rock
RUN git clone --branch 20200505-access-token-processing https://github.com/BGaunitz/kong-plugin-jwt-keycloak.git \
&& cd kong-plugin-jwt-keycloak \
&& luarocks make
RUN luarocks pack kong-plugin-jwt-keycloak ${JWT_PLUGIN_VERSION} \
&& luarocks install kong-plugin-jwt-keycloak-${JWT_PLUGIN_VERSION}.all.rock
USER kong
@BGaunitz Thanks for sharing the docker working like charm sorry i am late in party but if you can please share more configuration details of plugin also of OIDC and Keycloak-JWT.
Geting : {"message":"Bad token; invalid JSON"}
Looks like plugin is able to access both endpoints mentions in ReadMe https://github.com/gbbirkisson/kong-plugin-jwt-keycloak/issues/7#issuecomment-616071079 but still getting unauth
I can confirm that @PSheshenya solution works absolutely fine (OIDC + JWT Token). I added a minor fix for X-Access-Token header processing.
Dockerfile:
FROM kong:2.0.3-alpine LABEL description="Alpine + Kong 2.0.3 + kong-oidc plugin" ENV OIDC_PLUGIN_VERSION=1.1.0-0 ENV JWT_PLUGIN_VERSION=1.1.0-1 USER root RUN apk update && apk add git unzip luarocks RUN luarocks install kong-oidc RUN git clone https://github.com/PSheshenya/kong-oidc.git \ && cd kong-oidc \ && luarocks make RUN luarocks pack kong-oidc ${OIDC_PLUGIN_VERSION} \ && luarocks install kong-oidc-${OIDC_PLUGIN_VERSION}.all.rock RUN git clone --branch 20200505-access-token-processing https://github.com/BGaunitz/kong-plugin-jwt-keycloak.git \ && cd kong-plugin-jwt-keycloak \ && luarocks make RUN luarocks pack kong-plugin-jwt-keycloak ${JWT_PLUGIN_VERSION} \ && luarocks install kong-plugin-jwt-keycloak-${JWT_PLUGIN_VERSION}.all.rock USER kong
@BGaunitz getting this error any idea if you cna please help
Run with --v (verbose) or --vv (debug) for more details
waiting for db
Error: /usr/local/share/lua/5.1/kong/cmd/start.lua:64: nginx: [error] init_by_lua error: /usr/local/share/lua/5.1/kong/tools/utils.lua:620: error loading module 'kong.plugins.acme.handler':
/usr/local/share/lua/5.1/resty/acme/openssl.lua:5: attempt to index field 'version' (a nil value)
stack traceback:
/usr/local/share/lua/5.1/resty/acme/openssl.lua:5: in main chunk
[C]: in function 'require'
/usr/local/share/lua/5.1/resty/acme/util.lua:1: in main chunk
[C]: in function 'require'
/usr/local/share/lua/5.1/resty/acme/client.lua:3: in main chunk
[C]: in function 'require'
/usr/local/share/lua/5.1/kong/plugins/acme/client.lua:1: in main chunk
[C]: in function 'require'
/usr/local/share/lua/5.1/kong/plugins/acme/handler.lua:2: in main chunk
[C]: at 0x7f927db5b0d0
[C]: in function 'xpcall'
/usr/local/share/lua/5.1/kong/tools/utils.lua:611: in function 'load_module_if_exists'
/usr/local/share/lua/5.1/kong/db/dao/plugins.lua:149: in function 'load_plugin_handler'
/usr/local/share/lua/5.1/kong/db/dao/plugins.lua:227: in function 'load_plugin'
/usr/local/share/lua/5.1/kong/db/dao/plugins.lua:275: in function 'load_plugin_schemas'
/usr/local/share/lua/5.1/kong/init.lua:427: in function 'init'
init_by_lua:3: in main chunk
stack traceback:
[C]: in function 'error'
/usr/local/share/lua/5.1/kong/tools/utils.lua:620: in function 'load_module_if_exists'
/usr/local/share/lua/5.1/kong/db/dao/plugins.lua:149: in function 'load_plugin_handler'
/usr/local/share/lua/5.1/kong/db/dao/plugins.lua:227: in function 'load_plugin'
/usr/local/share/lua/5.1/kong/db/dao/plugins.lua:275: in function 'load_plugin_schemas'
/usr/local/share/lua/5.1/kong/init.lua:427: in function 'init'
init_by_lua:3: in main chunk
ua:3: in main chunk
Run with --v (verbose) or --vv (debug) for more details
waiting for db
I am about to archive this repository. Please move your issues/PRs the successor of this repo: https://github.com/telekom-digioss/kong-plugin-jwt-keycloak