fortios_router_accesslist does not properly put exact_match properly
It creates, but exact_match is set to disable whether you set enable or not.
Tested on FortiOS 6.4
resource "fortios_router_accesslist" "static_ospf_redistribution_networks" {
name = "static-redistribution"
comments = "Used to specify networks which get redistributed into OSPF"
rule {
id = 10
action = "permit"
prefix = "10.0.0.0 255.0.0.0"
exact_match = "enable"
}
}
Hi @CHRISMSM, thanks for the feedback. May I ask if your FortiOS version is 6.4.0? After testing, we found that this is a bug caused by FortiAPI on FortiOS 6.4.0, a bug ticket has been created internally to track this issue, will get back to you once it's resolved. There are currently two ways to quickly solve this problem:
Option I: Update to FortiOS 6.4.2, the FortiAPI bug has been fixed on FortiOS 6.4.2.
Option II: The following resource can be used as an alternative to configure route access-list:
resource "fortios_system_autoscript" "trname1" {
interval = 1
name = "1"
output_size = 10
repeat = 1
script = <<EOF
config router access-list
edit "static-redistribution"
config rule
edit 10
set prefix 10.0.0.0 255.255.255.0
set action permit
set exact-match enable
end
end
EOF
start = "auto"
}
Validation:
# terraform apply
2020/10/20 21:31:04 [WARN] Log levels other than TRACE are currently unreliable, and are supported only for backwa
Use TF_LOG=TRACE to see Terraform's internal logs.
----
An execution plan has been generated and is shown below.
Resource actions are indicated with the following symbols:
+ create
Terraform will perform the following actions:
# fortios_system_autoscript.trname1 will be created
+ resource "fortios_system_autoscript" "trname1" {
+ id = (known after apply)
+ interval = 1
+ name = "1"
+ output_size = 10
+ repeat = 1
+ script = <<~EOT
cconfig router access-list
edit "static-redistribution"
config rule
edit 10
set prefix 10.0.0.0 255.255.255.0
set action permit
set exact-match enable
end
end
EOT
+ start = "auto"
}
Plan: 1 to add, 0 to change, 0 to destroy.
Do you want to perform these actions?
Terraform will perform the actions described above.
Only 'yes' will be accepted to approve.
Enter a value: yes
fortios_system_autoscript.trname1: Creating...
fortios_system_autoscript.trname1: Creation complete after 0s [id=1]
Apply complete! Resources: 1 added, 0 changed, 0 destroyed.
myFGT # config router access-list
myFGT (access-list) # show
config router access-list
edit "static-redistribution"
config rule
edit 10
set prefix 10.0.0.0 255.255.255.0
set exact-match enable
next
end
next
end
Thanks!
Hi,
I'm running 6.4.5 and I have also the issue.
Hi,
I'm running 6.4.5 and I have also the issue.
Hi @pacrutchet, we are trying to reproduce the issue and investigate. Thanks!
@pacrutchet Thanks for the feedback, I can confirm your feedback is valid. This is an API bug. We are discussing the issue with API team. After we get a solution from them, we'll update the status here. Before that, can you please use the above work-around : https://github.com/fortinetdev/terraform-provider-fortios/issues/99#issuecomment-712997264 Let me know if you need anything else. Thank you!
@pacrutchet Status update: The API bug has been fixed on FOS 7.0.0. Validation:
Step1: create fortios_router_accesslist resource with exact_match = disable
labfirewall # get system status
Version: FortiGate-VM64 v7.0.0,build0066,210330 (GA)
provider "fortios" {
hostname = "192.168.52.177"
insecure = "true"
token = "GNH7r40H65GNb46kd4rG8rtrmn0fr1"
}
resource "fortios_router_accesslist" "static_ospf_redistribution_networks" {
name = "static-redistribution"
comments = "Used to specify networks which get redistributed into OSPF"
rule {
id = 10
action = "permit"
prefix = "10.0.0.0 255.0.0.0"
exact_match = "disable"
}
}
# terraform apply
An execution plan has been generated and is shown below.
Resource actions are indicated with the following symbols:
+ create
Terraform will perform the following actions:
# fortios_router_accesslist.static_ospf_redistribution_networks will be created
+ resource "fortios_router_accesslist" "static_ospf_redistribution_networks" {
+ comments = "Used to specify networks which get redistributed into OSPF"
+ dynamic_sort_subtable = "false"
+ id = (known after apply)
+ name = "static-redistribution"
+ rule {
+ action = "permit"
+ exact_match = "disable"
+ flags = (known after apply)
+ id = 10
+ prefix = "10.0.0.0 255.0.0.0"
+ wildcard = (known after apply)
}
}
Plan: 1 to add, 0 to change, 0 to destroy.
Do you want to perform these actions?
Terraform will perform the actions described above.
Only 'yes' will be accepted to approve.
Enter a value: yes
fortios_router_accesslist.static_ospf_redistribution_networks: Creating...
fortios_router_accesslist.static_ospf_redistribution_networks: Creation complete after 0s [id=static-redistribution]
Apply complete! Resources: 1 added, 0 changed, 0 destroyed.
labfirewall # config router access-list
labfirewall (access-list) # show
config router access-list
edit "static-redistribution"
set comments "Used to specify networks which get redistributed into OSPF"
config rule
edit 10
set prefix 10.0.0.0 255.0.0.0
next
end
next
end
Step2 Set exact_match = enable
resource "fortios_router_accesslist" "static_ospf_redistribution_networks" {
name = "static-redistribution"
comments = "Used to specify networks which get redistributed into OSPF"
rule {
id = 10
action = "permit"
prefix = "10.0.0.0 255.0.0.0"
exact_match = "enable"
}
}
# terraform apply
fortios_router_accesslist.static_ospf_redistribution_networks: Refreshing state... [id=static-redistribution]
An execution plan has been generated and is shown below.
Resource actions are indicated with the following symbols:
~ update in-place
Terraform will perform the following actions:
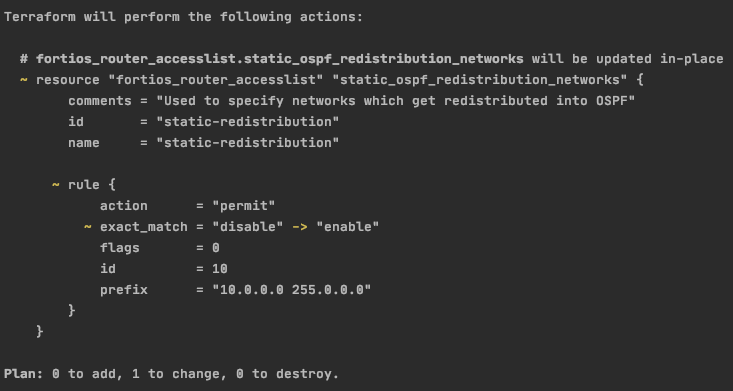
# fortios_router_accesslist.static_ospf_redistribution_networks will be updated in-place
~ resource "fortios_router_accesslist" "static_ospf_redistribution_networks" {
comments = "Used to specify networks which get redistributed into OSPF"
dynamic_sort_subtable = "false"
id = "static-redistribution"
name = "static-redistribution"
~ rule {
action = "permit"
~ exact_match = "disable" -> "enable"
flags = 0
id = 10
prefix = "10.0.0.0 255.0.0.0"
}
}
Plan: 0 to add, 1 to change, 0 to destroy.
Do you want to perform these actions?
Terraform will perform the actions described above.
Only 'yes' will be accepted to approve.
Enter a value: yes
fortios_router_accesslist.static_ospf_redistribution_networks: Modifying... [id=static-redistribution]
fortios_router_accesslist.static_ospf_redistribution_networks: Modifications complete after 0s [id=static-redistribution]
Apply complete! Resources: 0 added, 1 changed, 0 destroyed.
labfirewall (access-list) # show
config router access-list
edit "static-redistribution"
set comments "Used to specify networks which get redistributed into OSPF"
config rule
edit 10
set prefix 10.0.0.0 255.0.0.0
set exact-match enable
next
end
next
end
BTW https://github.com/fortinetdev/terraform-provider-fortios/issues/99#issuecomment-712997264 "Option I: Update to FortiOS 6.4.2, the FortiAPI bug has been fixed on FortiOS 6.4.2." The judgment is wrong, please ignore it.
Thank you @pacrutchet !
@frankshen01 Will it be fixed in 6.4.6 or a following version?
Hi @pacrutchet, I'm not too sure about their plan. So far, I haven’t received any relevant information about it. If there is any update from the API team, I will give feedback here in time! Thanks!
I will go ahead to close this case, if you still have questions, feel free to reopen it or another case.