ergo-pe-av
 ergo-pe-av copied to clipboard
ergo-pe-av copied to clipboard
🧠 🦠 An artificial neural network and API to detect Windows malware, based on Ergo and LIEF.
An artificial neural network and API to detect Windows malware, based on Ergo and LIEF.
Installation
cd /path/to/ergo-pe-av
sudo pip3 install -r requirements.txt
Use as an API
ergo serve /path/to/ergo-pe-av --classes "clean, malware"
From the client, to scan a file that the server can access too:
curl "http://localhost:8080/?x=/path/to/file.exe"
# or
curl --data "x=/path/to/file.exe" "http://localhost:8080/"
To upload the whole file:
curl -F "x=@/path/to/file.exe" "http://localhost:8080/"
To encode a file to a vector of raw features:
curl -F "x=@/path/to/file.exe" "http://localhost:8080/encode"
To scan a vector of raw features:
curl --data "x=0.0,0.0,0.0,0.0,0.0,0.0,0.0,1.0,1.0,0.0,0.0,0.847058823529,......" "http://localhost:8080/"
Model Statistics
The dataset is made of ~200000 samples divided in two subfolders:
classes/pe-maliciouswith 100000 malware samples from VirusTotalclasses/pe-cleanwith 100000 clean samples
The dataset.csv training file has been generated with:
ergo encode ergo-pe-av /media/evilsocket/4TB/datapath-pe/classes --filter "*.exe"
| Training | ROC/AUC |
|---|---|
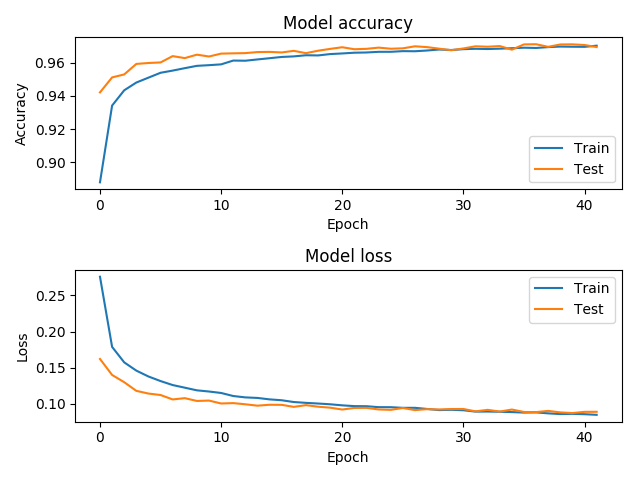 |
 |
| Training | Validation | Testing |
|---|---|---|
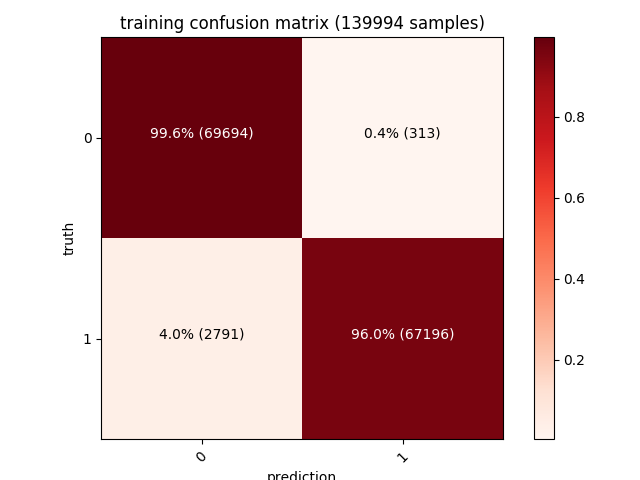 |
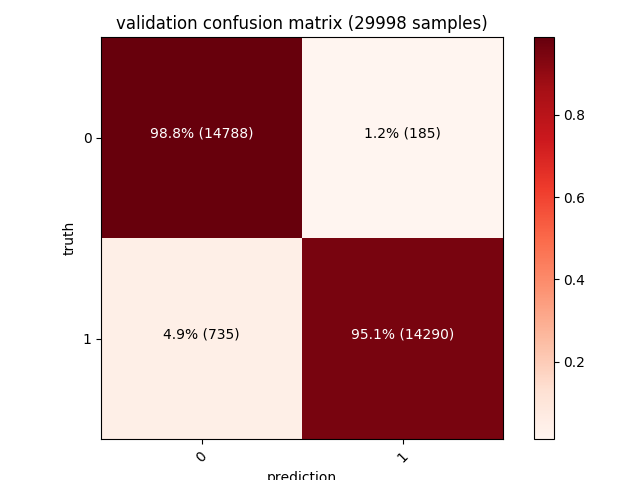 |
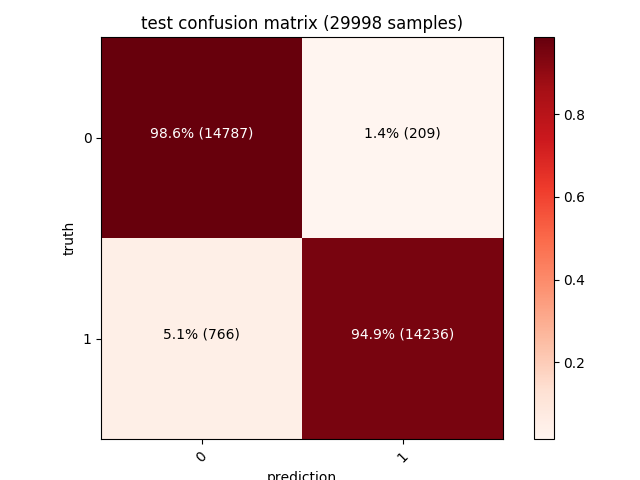 |
License
Made with ♥ by the dev team and it is released under the GPL 3 license.