for-aws
 for-aws copied to clipboard
for-aws copied to clipboard
Unable to use a custom security group in an existing VPC
Hello,
When using an existing VPC, it can be useful to specify an existing security group to the managers or workers launch configuration, for example when many swarm stacks are created on the same VPC.
This is my CloudFormation update allowing to do it, based on https://editions-us-east-1.s3.amazonaws.com/aws/stable/Docker-no-vpc.tmpl :
@@ -62,6 +62,40 @@
"Condition": "CloudStorEfsSelected"
}
]
+ },
+ "HasManagerSecurityGroups": {
+ "Fn::Not": [
+ {
+ "Fn::Equals": [
+ "",
+ {
+ "Fn::Join": [
+ "",
+ {
+ "Ref": "ManagerSecurityGroups"
+ }
+ ]
+ }
+ ]
+ }
+ ]
+ },
+ "HasWorkerSecurityGroups": {
+ "Fn::Not": [
+ {
+ "Fn::Equals": [
+ "",
+ {
+ "Fn::Join": [
+ "",
+ {
+ "Ref": "WorkerSecurityGroups"
+ }
+ ]
+ }
+ ]
+ }
+ ]
}
},
"Description": "Docker CE for AWS 17.09.0-ce (17.09.0-ce-aws1)",
@@ -476,7 +510,8 @@
"Parameters": [
"ManagerInstanceType",
"ManagerDiskSize",
- "ManagerDiskType"
+ "ManagerDiskType",
+ "ManagerSecurityGroups"
]
},
{
@@ -486,7 +521,8 @@
"Parameters": [
"InstanceType",
"WorkerDiskSize",
- "WorkerDiskType"
+ "WorkerDiskType",
+ "WorkerSecurityGroups"
]
},
{
@@ -536,6 +572,9 @@
"ManagerSize": {
"default": "Number of Swarm managers?"
},
+ "ManagerSecurityGroups": {
+ "default": "Manager additional Security Groups"
+ },
"PubSubnetAz1": {
"default": "Public Subnet 1"
},
@@ -556,6 +595,9 @@
},
"WorkerDiskType": {
"default": "Worker ephemeral storage volume type"
+ },
+ "WorkerSecurityGroups": {
+ "default": "Worker additional Security Groups"
}
}
}
@@ -808,6 +850,11 @@
"Description": "Number of Swarm manager nodes (1, 3, 5)",
"Type": "Number"
},
+ "ManagerSecurityGroups": {
+ "Description": "Manager additional Security Groups IDs separated by comma",
+ "Type": "CommaDelimitedList",
+ "ConstraintDescription": "must be a list of EC2 security group ids separated by comma"
+ },
"PubSubnetAz1": {
"Description": "Public Subnet 1",
"Type": "AWS::EC2::Subnet::Id"
@@ -844,6 +891,11 @@
"Default": "standard",
"Description": "Worker ephemeral storage volume type",
"Type": "String"
+ },
+ "WorkerSecurityGroups": {
+ "Description": "Worker additional Security Groups IDs separated by comma",
+ "Type": "CommaDelimitedList",
+ "ConstraintDescription": "must be a list of EC2 security group ids separated by comma"
}
},
"Resources": {
@@ -1317,14 +1369,45 @@
"KeyName": {
"Ref": "KeyName"
},
- "SecurityGroups": [
- {
- "Ref": "ManagerVpcSG"
- },
- {
- "Ref": "SwarmWideSG"
- }
- ],
+ "SecurityGroups": {
+ "Fn::If": [
+ "HasManagerSecurityGroups",
+ {
+ "Fn::Split": [
+ ",",
+ {
+ "Fn::Join": [
+ ",",
+ [
+ {
+ "Ref": "ManagerVpcSG"
+ },
+ {
+ "Ref": "SwarmWideSG"
+ },
+ {
+ "Fn::Join": [
+ ",",
+ {
+ "Ref": "ManagerSecurityGroups"
+ }
+ ]
+ }
+ ]
+ ]
+ }
+ ]
+ },
+ [
+ {
+ "Ref": "ManagerVpcSG"
+ },
+ {
+ "Ref": "SwarmWideSG"
+ }
+ ]
+ ]
+ },
"UserData": {
"Fn::Base64": {
"Fn::Join": [
@@ -1899,11 +1982,39 @@
"KeyName": {
"Ref": "KeyName"
},
- "SecurityGroups": [
- {
- "Ref": "NodeVpcSG"
- }
- ],
+ "SecurityGroups": {
+ "Fn::If": [
+ "HasWorkerSecurityGroups",
+ {
+ "Fn::Split": [
+ ",",
+ {
+ "Fn::Join": [
+ ",",
+ [
+ {
+ "Ref": "NodeVpcSG"
+ },
+ {
+ "Fn::Join": [
+ ",",
+ {
+ "Ref": "WorkerSecurityGroups"
+ }
+ ]
+ }
+ ]
+ ]
+ }
+ ]
+ },
+ [
+ {
+ "Ref": "NodeVpcSG"
+ }
+ ]
+ ]
+ },
"UserData": {
"Fn::Base64": {
"Fn::Join": [
And the result :
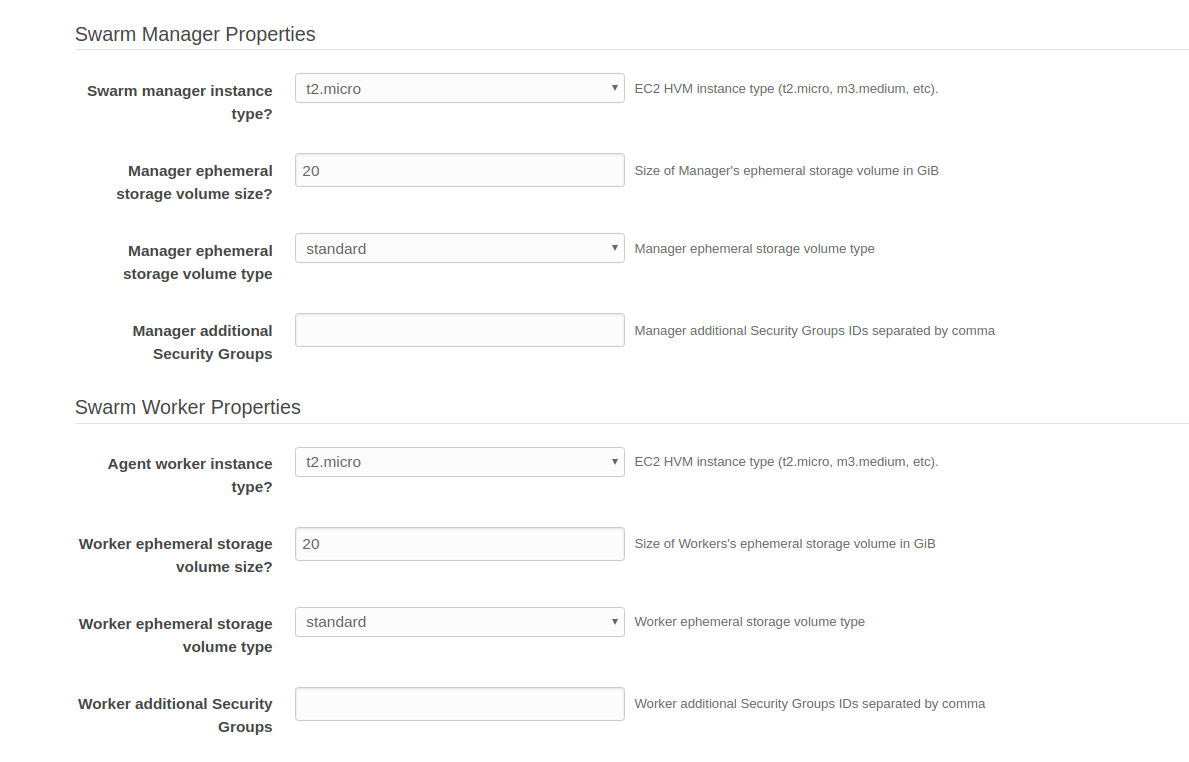
What do you think about it ? Is it possible to add this feature to the official CloudFormation template ?
Do you not see the value of this outside of existing VPC?
I'm not sure to understand you. As a security group is attached to a VPC, when CloudFormation creates a new VPC, there is no existing SG we can use for the moment. And as the template is used to create the VPC, this VPC will be deleted with the CloudFormation stack. I don't see any advantage to allow users to use a custom SG in a "temporary" VPC, as it will be created and deleted with the CloudFormation stack.
@mRoca that was my question - Being able to add an existing SG to a new VPC setup. You mentioned the delete, how is it handled here?
Without existing VPC, there is no available SG. The option is so useless in this situation. Nothing to do.
With an existing VPC, using an (or many) existing SG can be interesting, and this is the purpose of this issue : upgrade the CloudFormation template when we are using our own VPC by allowing to specify some additional existing SG to the EC2 Launch Configurations.