rust-u2f
 rust-u2f copied to clipboard
rust-u2f copied to clipboard
Security key cannot be registered by the `master` version
Describe the bug
Tried to build this program against rust 1.63, Kernel 5.19.2 under ArchLinux. Everything seems good except the security key cannot be recognized and registered. 45a073f9283026dcf74f99536d0f2899b6caee99 works, buf master doesn't. test-authenticator also fails to work.
$ ./target/release/test-authenticator
Using 15s as the timeout
Asking a security key to register now...
thread 'main' panicked at 'Registration failed: U2FToken(NotAllowed)', linux/test-authenticator/src/main.rs:140:56
note: run with `RUST_BACKTRACE=1` environment variable to display a backtrace
[1] 43525 IOT instruction (core dumped) ./target/release/test-authenticator
Logs Here are logs of my systemd daemon
$ systemctl --user status softu2f
● softu2f.service - Software-only U2F Emulation Service
Loaded: loaded (/usr/lib/systemd/user/softu2f.service; enabled; preset: enabled)
Active: active (running) since Sat 2022-08-20 00:26:19 EDT; 6min ago
Main PID: 42111 (user-daemon)
Tasks: 11 (limit: 18356)
Memory: 3.3M
CPU: 4ms
CGroup: /user.slice/user-1000.slice/[email protected]/app.slice/softu2f.service
└─42111 /usr/lib/softu2f/user-daemon
Aug 20 00:26:19 archinpocket systemd[1142]: Started Software-only U2F Emulation Service.
Aug 20 00:26:19 archinpocket user-daemon[42111]: Starting rust-u2f user daemon
Aug 20 00:26:19 archinpocket user-daemon[42111]: Storing secrets in an unencrypted file
Aug 20 00:26:19 archinpocket user-daemon[42111]: registering event source with poller: token=Token(1), intere>
Aug 20 00:26:19 archinpocket user-daemon[42111]: Sending create device request
Aug 20 00:26:19 archinpocket user-daemon[42111]: UHID device created with id: TODO
$ systemctl status softu2f
● softu2f.service - Software-only U2F Emulation Service
Loaded: loaded (/usr/lib/systemd/system/softu2f.service; static)
Active: active (running) since Sat 2022-08-20 00:06:08 EDT; 27min ago
TriggeredBy: ○ softu2f.socket
Main PID: 32248 (system-daemon)
Tasks: 16 (limit: 18356)
Memory: 1.4M
CPU: 4ms
CGroup: /system.slice/softu2f.service
└─32248 /usr/lib/softu2f/system-daemon
Aug 20 00:09:46 archinpocket system-daemon[32248]: registering event source with poller: token=Token(3), inte>
Aug 20 00:09:46 archinpocket system-daemon[32248]: Running getpwuid_r for user #1000
Aug 20 00:09:46 archinpocket system-daemon[32248]: Loading user with uid 1000
Aug 20 00:09:46 archinpocket system-daemon[32248]: Creating UHID virtual U2F device
Aug 20 00:09:46 archinpocket system-daemon[32248]: Sending create device input event
Aug 20 00:26:19 archinpocket system-daemon[32248]: registering event source with poller: token=Token(4), inte>
Aug 20 00:26:19 archinpocket system-daemon[32248]: Running getpwuid_r for user #1000
Aug 20 00:26:19 archinpocket system-daemon[32248]: Loading user with uid 1000
Aug 20 00:26:19 archinpocket system-daemon[32248]: Creating UHID virtual U2F device
Aug 20 00:26:19 archinpocket system-daemon[32248]: Sending create device input event
$ systemctl status softu2f.socket
○ softu2f.socket
Loaded: loaded (/usr/lib/systemd/system/softu2f.socket; enabled; preset: enabled)
Active: inactive (dead) since Sat 2022-08-20 00:25:44 EDT; 8min ago
Duration: 19min 44.790s
Triggers: ● softu2f.service
Listen: /run/softu2f/softu2f.sock (Stream)
Aug 20 00:06:00 archinpocket systemd[1]: Listening on softu2f.socket.
And
# journalctl -u softu2f.service
Aug 20 00:26:19 archinpocket system-daemon[32248]: registering event source with poller: token=Token(4), inte>
Aug 20 00:26:19 archinpocket system-daemon[32248]: Running getpwuid_r for user #1000
Aug 20 00:26:19 archinpocket system-daemon[32248]: Loading user with uid 1000
Aug 20 00:26:19 archinpocket system-daemon[32248]: Creating UHID virtual U2F device
Aug 20 00:26:19 archinpocket system-daemon[32248]: Sending create device input event
# journalctl --user -u softu2f.service
Aug 20 00:26:19 archinpocket systemd[1142]: Started Software-only U2F Emulation Service.
Aug 20 00:26:19 archinpocket user-daemon[42111]: Starting rust-u2f user daemon
Aug 20 00:26:19 archinpocket user-daemon[42111]: Storing secrets in an unencrypted file
Aug 20 00:26:19 archinpocket user-daemon[42111]: registering event source with poller: token=Token(1), intere>
Aug 20 00:26:19 archinpocket user-daemon[42111]: Sending create device request
Aug 20 00:26:19 archinpocket user-daemon[42111]: UHID device created with id: TODO
Update: debug build works, but release doesn't. That's even more weird.
I tested the profile settings one by one and found the reason. With one more line under release profile the security key starts to be recognized:
debug-assertions = true
which convert debug_assert! macros to conditional compilations. Please help to close this issue when it gets fixed :-D
@hammerfunctor, I don't suppose you still have your repo around? I tried to apply your workaround but failed.
Specifically I have https://github.com/kousu/rust-u2f/commit/9c28a3e8d0b014c983ec524bc9f2e7fe7889b9de which I'm building with this
PKGBUILD
pkgname=softu2f-git
pkgver=0.4.2.r12.g9c28a3e
pkgrel=1
pkgdesc="Software U2F HID token daemon (rust-u2f)"
url="https://github.com/danstiner/rust-u2f"
arch=(x86_64)
depends=(libdbus libsystemd openssl)
makedepends=(rust)
source=("git+https://github.com/kousu/rust-u2f#commit=9c28a3e8d0b014c983ec524bc9f2e7fe7889b9de")
sha256sums=('SKIP')
prepare() {
cd rust-u2f
cargo fetch --locked --target "$CARCH-unknown-linux-gnu"
sed -i 's,/libexec/,/lib/,' linux/{system,user}-daemon/softu2f.service
}
pkgver() {
cd rust-u2f
git describe --tags | sed 's/^v//; s/-/.r/; s/-/./'
}
build() {
cd rust-u2f
export RUSTUP_TOOLCHAIN=stable
export CARGO_TARGET_DIR=target
cargo build --frozen --release --all-features
}
package() {
cd rust-u2f
install -Dm 755 target/release/softu2f-user-daemon \
"$pkgdir"/usr/lib/softu2f/user-daemon
install -Dm 755 target/release/softu2f-system-daemon \
"$pkgdir"/usr/lib/softu2f/system-daemon
install -Dm 644 linux/user-daemon/softu2f.service \
"$pkgdir"/usr/lib/systemd/user/softu2f.service
install -Dm 644 linux/system-daemon/softu2f.service \
"$pkgdir"/usr/lib/systemd/system/softu2f.service
install -Dm 644 linux/system-daemon/softu2f.socket \
"$pkgdir"/usr/lib/systemd/system/softu2f.socket
install -Dm 644 linux/system-daemon/softu2f-tmpfiles.conf \
"$pkgdir"/usr/lib/tmpfiles.d/softu2f.conf
}
It builds with makepkg -s and I can install it with pacman -U and it creates
$ ls -l /run/softu2f/softu2f.sock
srw-rw-rw- 1 root root 0 Oct 25 20:03 /run/softu2f/softu2f.sock
but if I try Yubico's Demo it just hangs
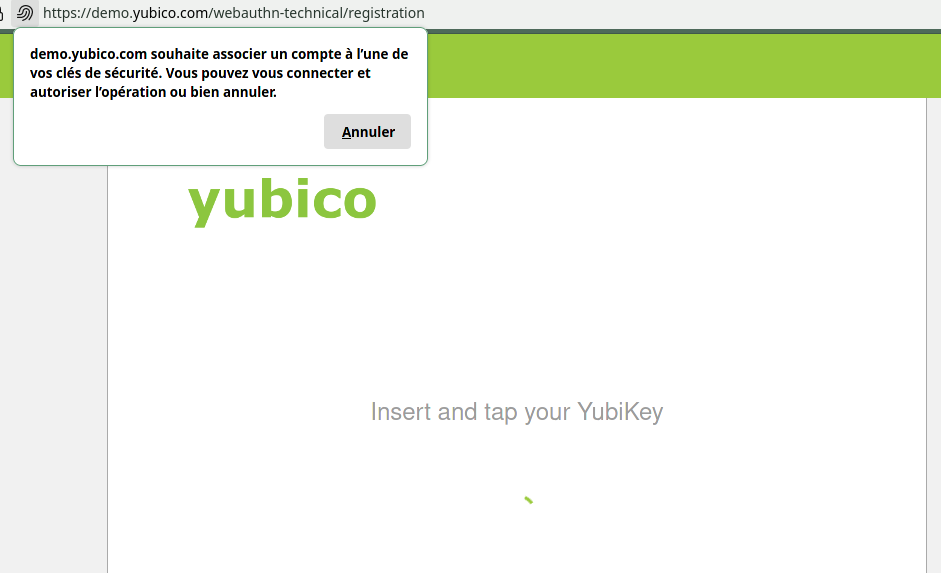
and these are all I see in the logs
journalctl -f -u softu2f
Oct 25 19:45:31 nigiri system-daemon[5325]: Starting rust-u2f system daemon
Oct 25 19:45:31 nigiri system-daemon[5325]: LISTEN_PID = Ok("5325"); LISTEN_FDS = Ok("1")
Oct 25 19:45:31 nigiri system-daemon[5325]: registering event source with poller: token=Token(1), interests=READABLE | WRITABLE
Oct 25 19:58:41 nigiri systemd[1]: Stopping Software-only U2F Emulation Service...
Oct 25 19:58:41 nigiri systemd[1]: softu2f.service: Deactivated successfully.
Oct 25 19:58:41 nigiri systemd[1]: Stopped Software-only U2F Emulation Service.
Oct 25 19:58:41 nigiri systemd[1]: Started Software-only U2F Emulation Service.
Oct 25 19:58:41 nigiri system-daemon[5818]: Starting rust-u2f system daemon
Oct 25 19:58:41 nigiri system-daemon[5818]: LISTEN_PID = Ok("5818"); LISTEN_FDS = Ok("1")
Oct 25 19:58:41 nigiri system-daemon[5818]: registering event source with poller: token=Token(1), interests=READABLE | WRITABLE
Oct 25 20:03:40 nigiri systemd[1]: Stopping Software-only U2F Emulation Service...
Oct 25 20:03:40 nigiri systemd[1]: softu2f.service: Deactivated successfully.
Oct 25 20:03:40 nigiri systemd[1]: Stopped Software-only U2F Emulation Service.
Oct 25 20:03:40 nigiri systemd[1]: Started Software-only U2F Emulation Service.
Oct 25 20:03:40 nigiri system-daemon[5950]: Starting rust-u2f system daemon
Oct 25 20:03:40 nigiri system-daemon[5950]: LISTEN_PID = Ok("5950"); LISTEN_FDS = Ok("1")
Oct 25 20:03:40 nigiri system-daemon[5950]: registering event source with poller: token=Token(1), interests=READABLE | WRITABLE
Versions
$ pacman -Q rust
rust 1:1.64.0-1
$ uname -a
Linux laptop 5.19.12-arch1-1 #1 SMP PREEMPT_DYNAMIC Wed, 28 Sep 2022 13:21:25 +0000 x86_64 GNU/Linux
Oh I take it all back! I just hadn't run systemctl --user start softu2f! With that, test-authenticator works:
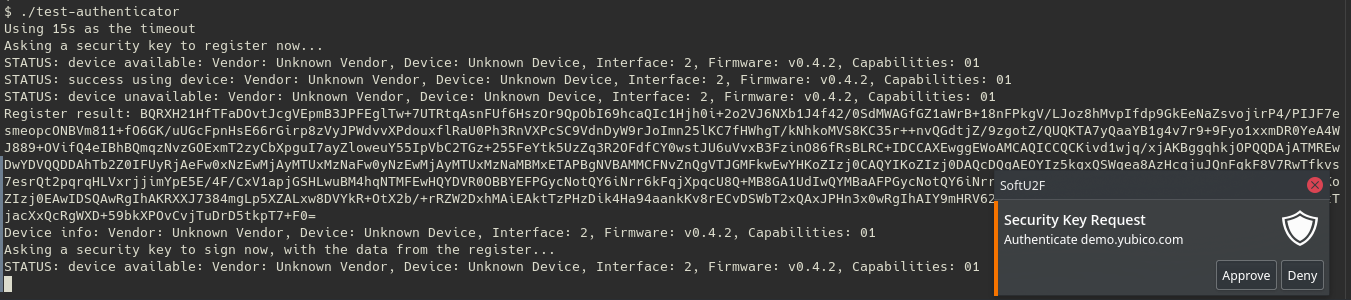
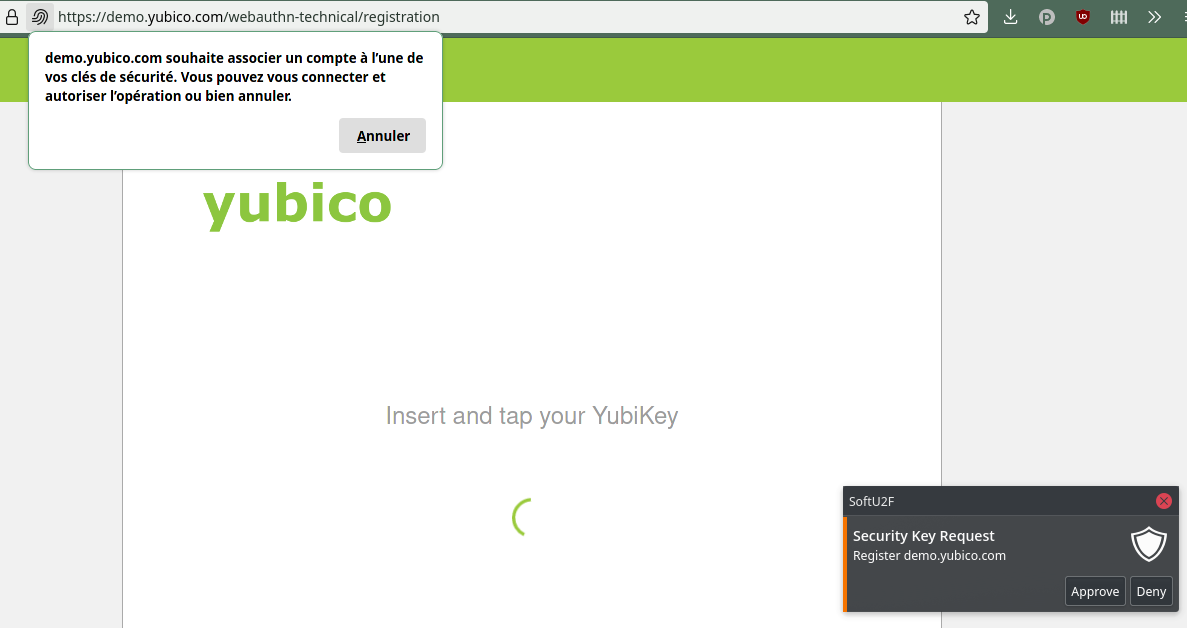
and so does Yubico:
@hammerfunctor Sorry not sure what is going wrong for you, that output indicates the test program is not finding any U2F devices to talk to. I see the same output if I stop the user service:
$ systemctl --user stop softu2f.service
$ cargo run
Using 15s as the timeout
Asking a security key to register now...
thread 'main' panicked at 'Registration failed: U2FToken(NotAllowed)', linux/test-authenticator/src/main.rs:140:56
note: run with `RUST_BACKTRACE=1` environment variable to display a backtrace
STATUS: end
But if I have everything running then it works for me:
$ systemctl --user start softu2f.service
dan@pop-os:~/rust-u2f/linux/test-authenticator$ cargo run
Using 15s as the timeout
Asking a security key to register now...
STATUS: device available: Vendor: Unknown Vendor, Device: Unknown Device, Interface: 2, Firmware: v0.4.2, Capabilities: 01
Register result: BQTI3Ucm55ALKQ3viwLPpKoa0f0ZiOjBqDoAWco1W+JIhiuCe87Xo77+KrZAc1yVvLtJDKrRn92gW3H3V3YYJzky/6RkKWzPW0xseJ7lD8p6HR3tC7jmkXdXzxvInMcHhGPttEOb1baJZxXTT8mgdxphGMx/xPtrWYvlj7XajW+i1qsGoLyIcwvgpjAzZ44w46CwTp5NmcVvvWK7mIcKuN+nYYAMY21LqeFy8orlMqLJfYxJauiLtxDb6Vxr6p+xZlf9wcKfNSOV/Gs8MoH7oB+mfbyzTfDdcAWlkXu8eITc0gPPmHd7RRUhuf3wlZouCm848yEwYOUBQVLNhah47edAuzsEQ+dy1fNEVS3avBeNOUYpg8KaIy6MqN7RFGEuSTpfletK8ozBZj7QFwcdQt0HtrbBlc1slpwSjLkwBxUPYzCCAXEwggEWoAMCAQICCQCKivd1wjq/xjAKBggqhkjOPQQDAjATMREwDwYDVQQDDAhTb2Z0IFUyRjAeFw0xNzEwMjAyMTUxMzNaFw0yNzEwMjAyMTUxMzNaMBMxETAPBgNVBAMMCFNvZnQgVTJGMFkwEwYHKoZIzj0CAQYIKoZIzj0DAQcDQgAEOYIz5kgxQSWqea8AzHcqjuJQnFqkF8V7RwTfkvs7esrQt2pqrqHLVxrjjimYpE5E/4F/CxV1apjGSHLwuBM4hqNTMFEwHQYDVR0OBBYEFPGycNotQY6iNrr6kFqjXpqcU8Q+MB8GA1UdIwQYMBaAFPGycNotQY6iNrr6kFqjXpqcU8Q+MA8GA1UdEwEB/wQFMAMBAf8wCgYIKoZIzj0EAwIDSQAwRgIhAKRXXJ7384mgLp5XZALxw8DVYkR+OtX2b/+rRZW2DxhMAiEAktTzPHzDik4Ha94aankKv8rECvDSWbT2xQAxJPHn3x0wRQIhAKAb1JJ82CRLVByFjupQ4rvT052G5J3DBtKs653Af1E9AiBIF0pdU5pPfu6v1c23gGjh44tsP8RE3dB20A/xeCU9gg==
Device info: Vendor: Unknown Vendor, Device: Unknown Device, Interface: 2, Firmware: v0.4.2, Capabilities: 01
Asking a security key to sign now, with the data from the register...
STATUS: success using device: Vendor: Unknown Vendor, Device: Unknown Device, Interface: 2, Firmware: v0.4.2, Capabilities: 01
STATUS: device unavailable: Vendor: Unknown Vendor, Device: Unknown Device, Interface: 2, Firmware: v0.4.2, Capabilities: 01
STATUS: device available: Vendor: Unknown Vendor, Device: Unknown Device, Interface: 2, Firmware: v0.4.2, Capabilities: 01
STATUS: success using device: Vendor: Unknown Vendor, Device: Unknown Device, Interface: 2, Firmware: v0.4.2, Capabilities: 01
Sign result: AQAAAAEwRQIhAM2hXdRpoyzLGK/4UCbOz+CA5Plu6m8G8qOcivmGwPyJAiAik0V5SyxywHRLkoe/8JWgnz8U6EqmWUTOctqjR4LSwA==
Key handle used: pGQpbM9bTGx4nuUPynodHe0LuOaRd1fPG8icxweEY+20Q5vVtolnFdNPyaB3GmEYzH/E+2tZi+WPtdqNb6LWqwagvIhzC+CmMDNnjjDjoLBOnk2ZxW+9YruYhwq436dhgAxjbUup4XLyiuUyosl9jElq6Iu3ENvpXGvqn7FmV/3Bwp81I5X8azwygfugH6Z9vLNN8N1wBaWRe7x4hNzSA8+Yd3tFFSG5/fCVmi4KbzjzITBg5QFBUs2FqHjt50C7OwRD53LV80RVLdq8F405RimDwpojLoyo3tEUYS5JOl+V60ryjMFmPtAXBx1C3Qe2tsGVzWyWnBKMuTAHFQ9j
Device info: Vendor: Unknown Vendor, Device: Unknown Device, Interface: 2, Firmware: v0.4.2, Capabilities: 01
Done.
STATUS: device unavailable: Vendor: Unknown Vendor, Device: Unknown Device, Interface: 2, Firmware: v0.4.2, Capabilities: 01
STATUS: end
@kousu glad you figured it out, nice to see this old project still works :)
Fixed a bug only affecting release builds, potentially that was the issue here
@kousu glad you figured it out, nice to see this old project still works :)
Yes. This is extremely useful for me. Some sites insist on imposing some dumb 2fa method, none of which I trust: SMS is extremely stealable; installing an push notification app is a DoS waiting to happen because it needs to be online all the time and I lose/break my devices pretty often, and plus I don't know what kind of surveillance comes with such an app; and as for Yubikeys, they're small, and I'm also likely to lose/break them, and they're fairly expensive to replace.
At least with softu2f I can give every device I'm on its own key, and/or I can back up the keys, so I won't get locked out.
I know it kind of defeats the "second" part of "second factor", but like you say in the README, security is about risk trade-offs.
Thanks for the report, I believe the issue was addressed. I can register using latest master.