Provenance of vulnerabilities
The end user needs to see an explanation for how the vuln was detected.
For each vuln, we should store:
- which scans detected it
- method of detection (for example, through cpe2cve, or which html element wappalyzer scanned)
We should also display this to the end user on the vulnerabilities page.
subdomain.cisa.gov/test has CVE-XXX
cisa.gov (root domain inputted by user) -> findomain found subdomain.cisa.gov -> webscraper scraped subdomain.cisa.gov/test -> wappalyzer detected Apache version 1 -> cpe2cve scan detected CVE-XXX
Draft frontend view:
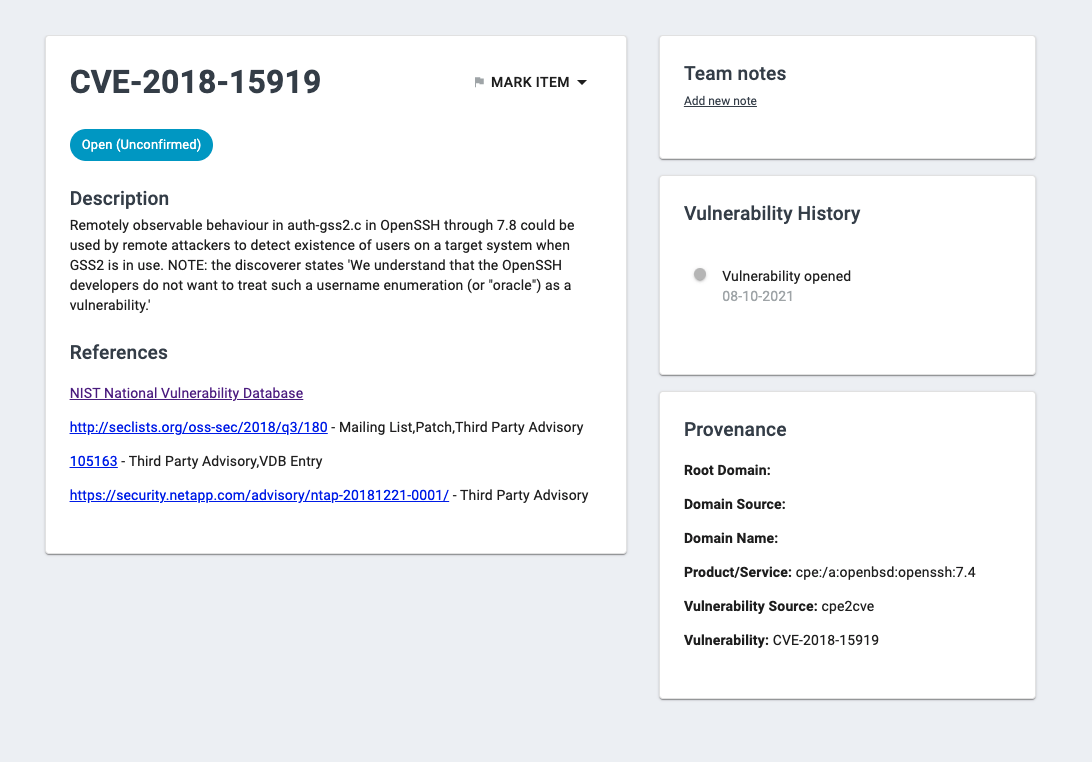 Still working out bugs to get all information...
Still working out bugs to get all information...
@aloftus23 as we discussed today, we should:
- further refine out the end state / UI we want, taking what you have as a start
- then document (maybe in a word doc?) the changes to models necessary to store the data needed. We should share this doc with the team and get feedback from everyone until we agree on the approach
- then, finally, implement this.
Also consider the following things when you create the UI:
- We may want to support multiple sources, for example, if a vuln is detected by both shodan and wappalyzer
- "cpe2cve" is not that helpful, instead, it would be helpful to show the actual source where the CPE was found (for example: "cpe2cve -> wappalyzer")
Reopening as there's still stuff we can do:
- We may want to support multiple sources, for example, if a vuln is detected by both shodan and wappalyzer
- "cpe2cve" is not that helpful, instead, it would be helpful to show the actual source where the CPE was found (for example: "cpe2cve -> wappalyzer")