fix(core): programmatically change PG sslmode to avoid self signed cert errors
Description
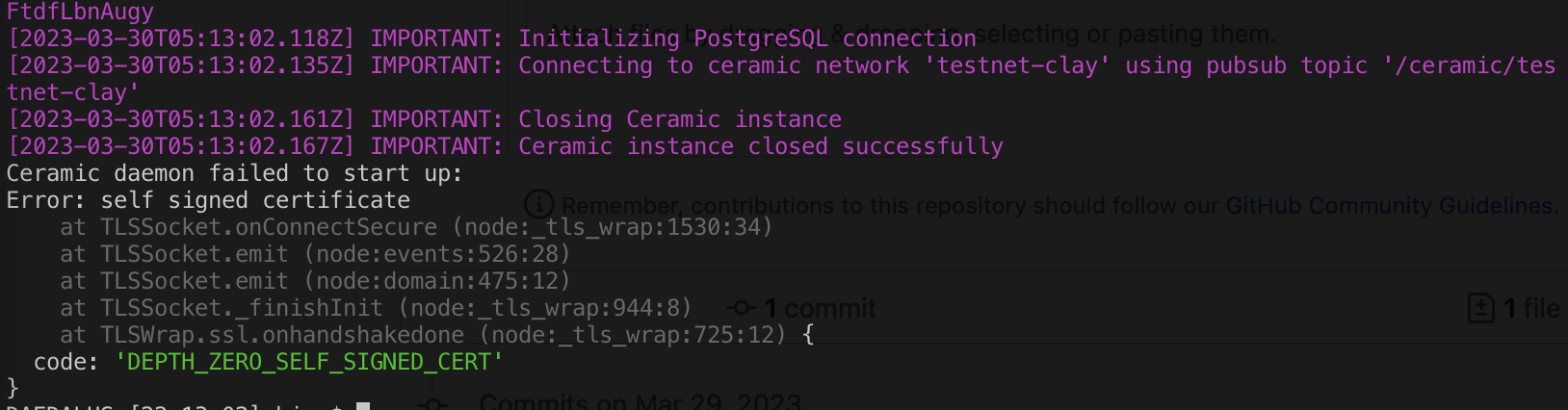
This addresses a common issue that Postgres will throw a self signed cert error with cloud deployments/PaaS (e.g. Heroku, DigitalOcean) and terminate connections because of the reliance on self signed certificated within a VPC and ultimate fail a build. Trying to address the issue directly in the ORM library Knex with the SSL connection properties of: { rejectUnauthorized: false } did not yield the desired effect and the only other recourse would've been to disable TLS verification completely (process.env.NODE_TLS_REJECT_UNAUTHORIZED), which is highly undesirable.
Updating the mode programmatically was chosen over the option to inform the user and do it manually or integrating it into the config file to avoid further friction during node deployments. Overall, this approach should not introduce any security risks as well as a MITM (man in the middle attack) between a node deployment and the Postgres instance within a VPC is fairly unlikely.
Before Fix:
With a PaaS default connection URL example of: postgres://ceramic:[email protected]:5432/ceramic?sslmode=required
After Fix:
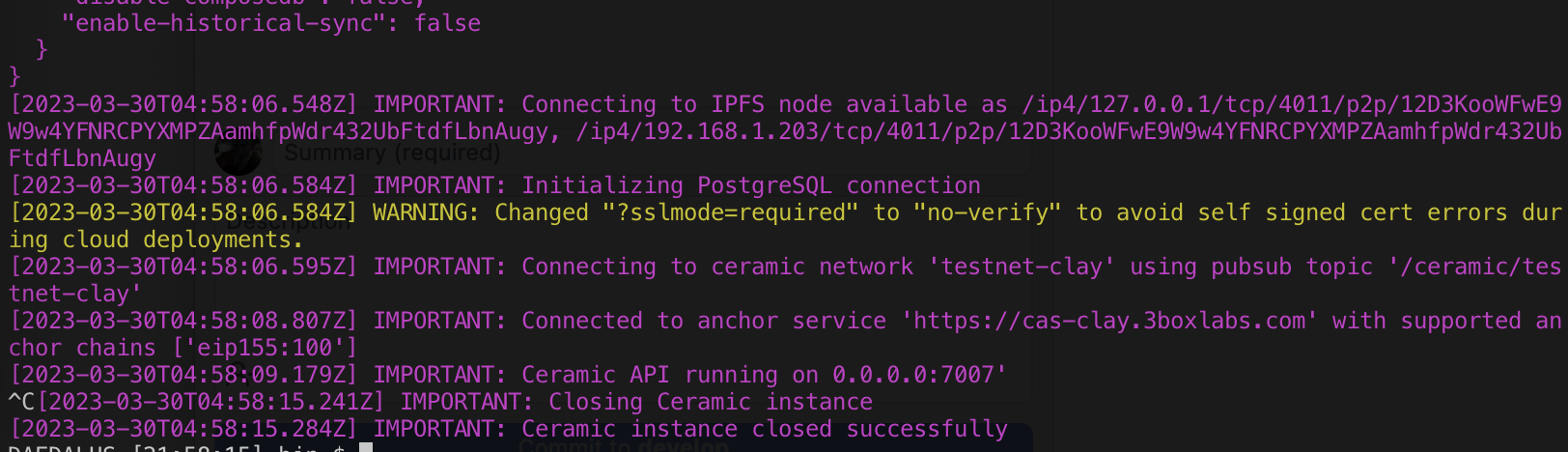
How Has This Been Tested?
Describe the tests that you ran to verify your changes. Provide instructions for reproduction.
- [ ] Local replication of described issue
- [ ] tested all valid
?sslmode=XYZconfig options to verify functionality
References:
This should most likely be listed or called out in the documentation referencing DigitalOcean & Heroku as source for the motivation.
I'd like to see the option of providing a CA cert (which would validate the self-signed server cert) for operators that want to preserve database connection security. It's reasonable to assume the database and credentials could be reused outside ceramic ;( If we go that route, proving an option or client certs would be nice too https://www.postgresql.org/docs/current/auth-cert.html
ping @willex what's the status of this PR?