Image Upload Issue at product section from Backend
I am trying to host magento on centminmod but I am not able to add the image from backend
Sharing the nginx conf file for my virtual host
Centmin Mod Getting Started Guide
must read http://centminmod.com/getstarted.html
redirect from non-www to www
uncomment, save file and restart Nginx to enable
if unsure use return 302 before using return 301
#server {
listen 80;
server_name magento.game5.ml;
return 301 $scheme://www.magento.game5.ml$request_uri;
}
server {
server_name magento.game5.ml www.magento.game5.ml;
access_log /home/nginx/domains/magento.game5.ml/log/access.log combined buffer=256k flush=5m; error_log /home/nginx/domains/magento.game5.ml/log/error.log;
#include /usr/local/nginx/conf/autoprotect/magento.game5.ml/autoprotect-magento.game5.ml.conf; set $MAGE_ROOT /home/nginx/domains/magento.game5.ml/public; root $MAGE_ROOT/pub; include /usr/local/nginx/conf/503include-main.conf;
index index.php; autoindex off; charset UTF-8; error_page 404 403 = /errors/404.php; #add_header "X-UA-Compatible" "IE=Edge";
PHP entry point for setup application
location ~* ^/setup($|/) { root $MAGE_ROOT; location ~ ^/setup/index.php { include /usr/local/nginx/conf/php.conf; }
location ~ ^/setup/(?!pub/). {
deny all;
}
location ~ ^/setup/pub/ {
add_header X-Frame-Options "SAMEORIGIN";
}
}
PHP entry point for update application
location ~* ^/update($|/) { root $MAGE_ROOT;
location ~ ^/update/index.php {
fastcgi_split_path_info ^(/update/index.php)(/.+)$;
include /usr/local/nginx/conf/php_magento.conf;
}
# Deny everything but index.php
location ~ ^/update/(?!pub/). {
deny all;
}
location ~ ^/update/pub/ {
add_header X-Frame-Options "SAMEORIGIN";
}
}
location / { include /usr/local/nginx/conf/503include-only.conf; try_files $uri $uri/ /index.php$is_args$args; }
location /pub/ { location ~ ^/pub/media/(downloadable|customer|import|theme_customization/.*.xml) { deny all; } alias $MAGE_ROOT/pub/; add_header X-Frame-Options "SAMEORIGIN"; }
location /static/ { # Uncomment the following line in production mode expires max;
# Remove signature of the static files that is used to overcome the browser cache
location ~ ^/static/version {
rewrite ^/static/(version\d*/)?(.*)$ /static/$2 last;
}
location ~* \.(ico|jpg|jpeg|png|gif|svg|js|css)$ {
add_header Cache-Control "public";
add_header Access-Control-Allow-Origin *;
add_header X-Frame-Options "SAMEORIGIN";
expires 30d;
if (!-f $request_filename) {
rewrite ^/static/?(.*)$ /static.php?resource=$1 last;
}
}
location ~* \.(swf|eot|ttf|otf|woff|woff2)$ {
add_header Cache-Control "public";
add_header Access-Control-Allow-Origin *;
add_header X-Frame-Options "SAMEORIGIN";
expires +1y;
if (!-f $request_filename) {
rewrite ^/static/?(.*)$ /static.php?resource=$1 last;
}
}
location ~* \.(zip|gz|gzip|bz2|csv|xml)$ {
add_header Cache-Control "no-store";
add_header X-Frame-Options "SAMEORIGIN";
expires off;
if (!-f $request_filename) {
rewrite ^/static/?(.*)$ /static.php?resource=$1 last;
}
}
if (!-f $request_filename) {
rewrite ^/static/?(.*)$ /static.php?resource=$1 last;
}
add_header X-Frame-Options "SAMEORIGIN";
}
location /media/ { try_files $uri $uri/ /get.php$is_args$args;
location ~ ^/media/theme_customization/.*\.xml {
deny all;
} location ~* .(ico|jpg|jpeg|png|gif|svg|js|css)$ { add_header Cache-Control "public"; add_header Access-Control-Allow-Origin ; add_header X-Frame-Options "SAMEORIGIN"; expires 30d; try_files $uri $uri/ /get.php$is_args$args; } location ~ .(swf|eot|ttf|otf|woff|woff2)$ { add_header Cache-Control "public"; add_header Access-Control-Allow-Origin ; add_header X-Frame-Options "SAMEORIGIN"; expires +1y; try_files $uri $uri/ /get.php$is_args$args; } location ~ .(zip|gz|gzip|bz2|csv|xml)$ { add_header Cache-Control "no-store"; add_header X-Frame-Options "SAMEORIGIN"; expires off; try_files $uri $uri/ /get.php$is_args$args; } add_header X-Frame-Options "SAMEORIGIN"; }
location /media/customer/ { deny all; }
location /media/downloadable/ { deny all; }
location /media/import/ { deny all; }
Deny cron and files with the obvious names. favorite entry points for hackers and script kiddie
location ~* ^/(cron|phpminiadmin|pma|sqlyog|adminer.+).php { deny all; }
Deny auth and composer
location ~ (auth|package|composer).(json|lock)$ { deny all; }
PHP entry point for main application
location ~ (index|get|static|report|404|503|health_check).php$ { try_files $uri =404; add_header X-Processing-Time $request_time always; add_header X-Request-ID $request_id always; add_header Strict-Transport-Security $mag_hstsheader always; add_header X-UA-Compatible 'IE=Edge,chrome=1'; add_header Link "<$scheme://$http_host$request_uri>; rel="canonical"" always; fastcgi_buffers 1024 4k;
fastcgi_param PHP_FLAG "session.auto_start=off \n suhosin.session.cryptua=off";
fastcgi_param PHP_VALUE "memory_limit=4096M \n max_execution_time=18000 \n max_input_time=18000";
fastcgi_read_timeout 600s;
fastcgi_connect_timeout 600s;
include /usr/local/nginx/conf/503include-only.conf;
include /usr/local/nginx/conf/php.conf;
}
Banned locations (only reached if the earlier PHP entry point regexes don't match)
location ~* (.php$|.htaccess$|.git) { deny all; }
#include /usr/local/nginx/conf/pre-staticfiles-local-magento.game5.ml.conf; include /usr/local/nginx/conf/pre-staticfiles-global.conf; #include /usr/local/nginx/conf/staticfiles.conf; #include /usr/local/nginx/conf/php.conf; #include /usr/local/nginx/conf/drop.conf; #include /usr/local/nginx/conf/errorpage.conf; include /usr/local/nginx/conf/vts_server.conf; }
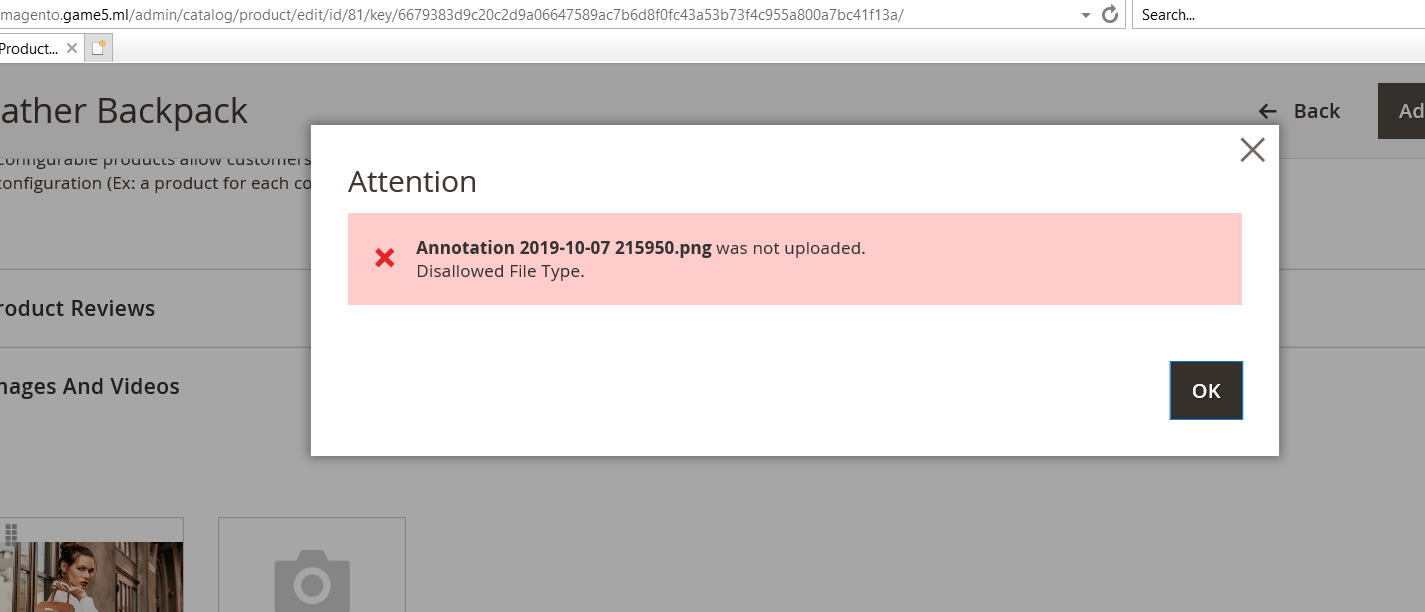
Any issues in my config file?
I haven't looked at Magento since originally post the write up at https://github.com/centminmod/centminmod-magento2/ so whether changes or updates are needed due to Magento changes, I wouldn't know.
Might want to wrap your nginx rules in markdown code for easier formatting at https://guides.github.com/features/mastering-markdown/ and post a thread in official community forums as others may have tips for magento use https://community.centminmod.com/forums/ecommerce-shopping-cart-usage.35/