blokada
 blokada copied to clipboard
blokada copied to clipboard
Feature Request: Log which app requested
I like the easy to see log and search of the v4 GUI, one addition I'd really like to see in there, is when you click an entry to open it up, {domain forwarded/domain blocked} I'd really like to see which specific app caused the request.
Agree! That would be very heplful!
This is a much appreciated feature
Is this even possible without root?
Showing which app produced connection XY is an awesome idea. Adding to this, it would also be helpful to see all connections per app.
This is planned. Feel free to "like" this ticket to let me know how many people is interested so we can prioritise.
I'll go one further, if the request has GET parameters visible, would be great to be able to see those and filter on those. Reason being an app may use one common domain name or basic URL for data including ads, and the differentiator is in the GET parameters. May be trickier if they are in the POST parameters (not visible until after the connection is made).
Yes, but that's another layer of OSI network design, which we don't operate on yet. It's related to 'cosmetic filtering'.
I was looking for this:). I would like to see which app is using what..It would be also nice to have some additional info/grouping for the blocked domain (advertising/analytics etc.). So I can get some insight about each app. It could also show which apps are using particular tracker.
Hi, for me this would be my favorite feature from the app, can we see this being on the next to do list?
Pls add this feature!
This feature is absolutely needed. It would really help people identify apps that need removing and/or disabling, which would result in less filtering needed.
Bad news. Starting with Android 10 access to the info which app created a connection is blocked so until we find a new way to get this information its pointless to implement this feature as it would only support Android < 10.
Bad news. Starting with Android 10 access to the info which app created a connection is blocked so until we find a new way to get this information its pointless to implement this feature as it would only support Android < 10.
And yet adguard manages to show that just fine...... On a OnePlus 7 Pro running Android 10
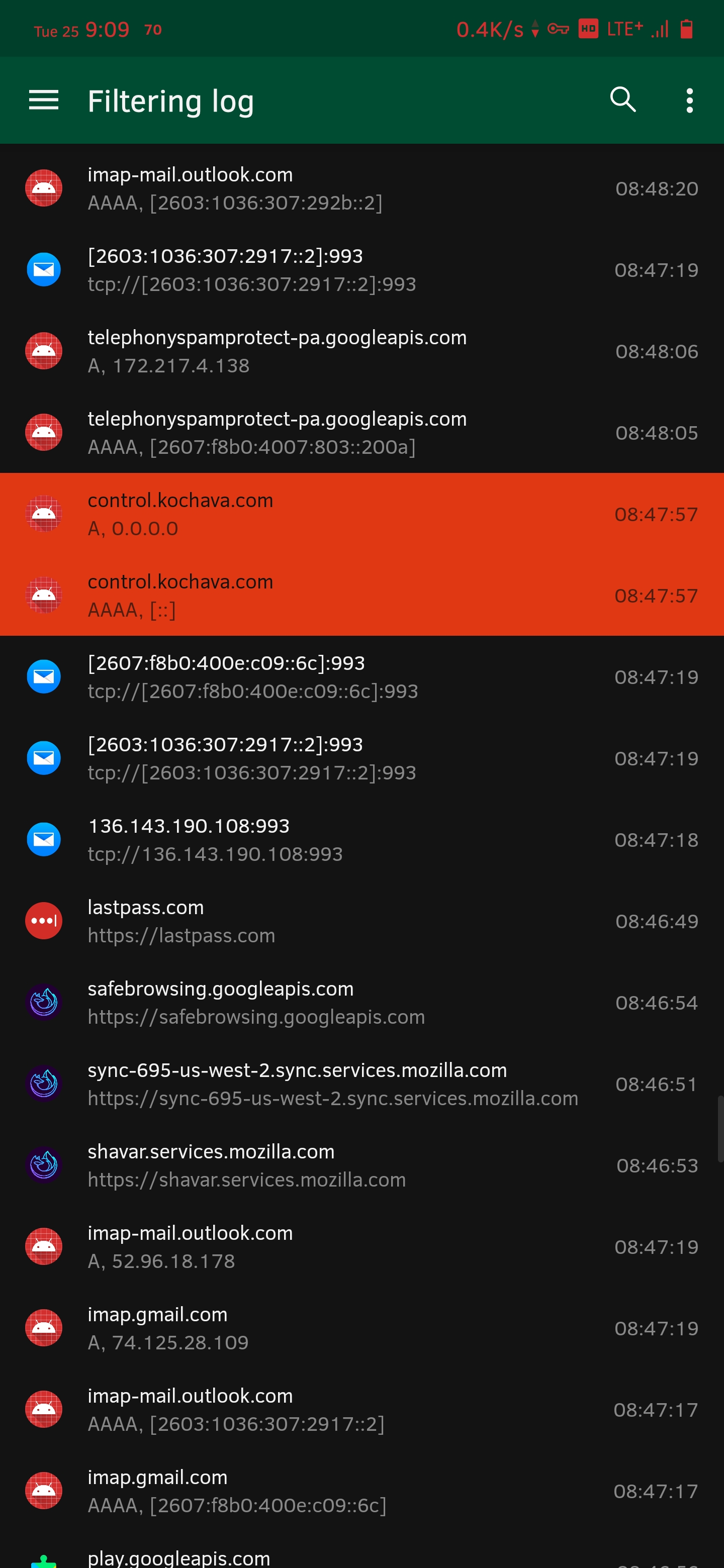
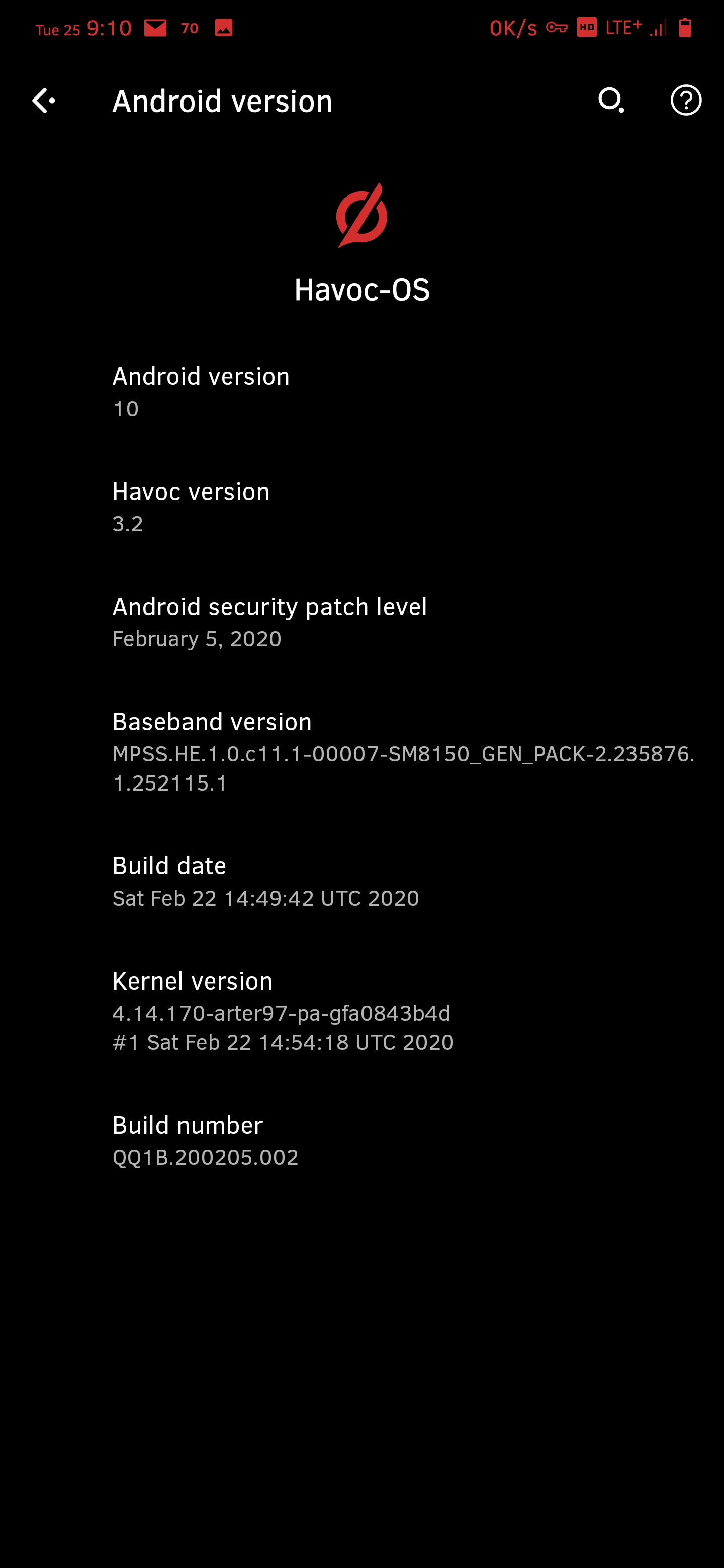 Also working fine on stock OxygenOS 10.3.1 along with havoc (screenshots from havoc)
Also working fine on stock OxygenOS 10.3.1 along with havoc (screenshots from havoc)
@linuxandria If your manufacturer still allows access to /proc/net/ you can call yourself lucky or unlucky depending on how you want to look at it. In addition adguard might use something like being a device admin to get more info. I don't know for sure as I'm neither a Adguard-developer nor user but just a hobby-dev doing stuff for Blokada.
@anibalcatheringer you are incorrect. AdGuard never requested device admin
@ps100000 I do however find it odd for me it works on both a stock and custom ROM. Though why do you even access that? Especially as every packet goes through your tunnel anyhow?
AdGuard does however request usage access. I bet that's it
@ps100000 I do however find it odd for me it works on both a stock and custom ROM. Though why do you even access that? Especially as every packet goes through your tunnel anyhow?
Because we have to find out which app the package belongs to. There might be some other way. I'll have another look at some point.
This would be an incredibly helpful feature. Netguard (https://github.com/M66B/NetGuard) is able to associate requests with specific apps -- no rooting required. Perhaps their source code could be a starting point for figuring out how to implement this in Blokada. I'm not a Java developer, but it looks like the AdapterLog.java might be where this functionality is implemented in Netguard. https://github.com/M66B/NetGuard/blob/297c8b2c3030dff502882f2e2ac215a76a6ec3a3/app/src/main/java/eu/faircode/netguard/AdapterLog.java#L329