backintime
 backintime copied to clipboard
backintime copied to clipboard
The Encryption password disappears ever few days.
For some reason, the encryption password seems to get lost every few days. This causes a backup to fail and is not detectable unless you open the app.
Why is this happening? I'm not removing it myself it just goes disapears.
@cnobile2012 There is a new forming maintaining team and we do review all issues. Is this problem still relevant for you or did you find a solution?
Tag: Password, Encryption, Feedback
Since I posted this issue I have a better understanding of the issue. As long as you don't reboot the machine the password is stored between runs, however, once you reboot the machine the password is lost, and if you do not remember to reset the password no backups are done.
It seems the password is stored in memory for security reasons, this is fine however there needs to be a way to alert the user that the password needs to be reset as soon as the machine comes back up or figure out a way to store the password on disk in a secure way.
//cc @aryoda
@cnobile2012 Could you please give me some more details how you configured the profile
- where do you enter the password in your OS and BiT
- how are the backups scheduled - as cron job?
- which BiT version on which OS, how installed (packaged or from github)?
- BiT started as root or normal?
- what type of encryption (file system?)
In the BiT settings you can eg. store the password in a password safe ("keyring") if you check the checkbox "save password to keyring":
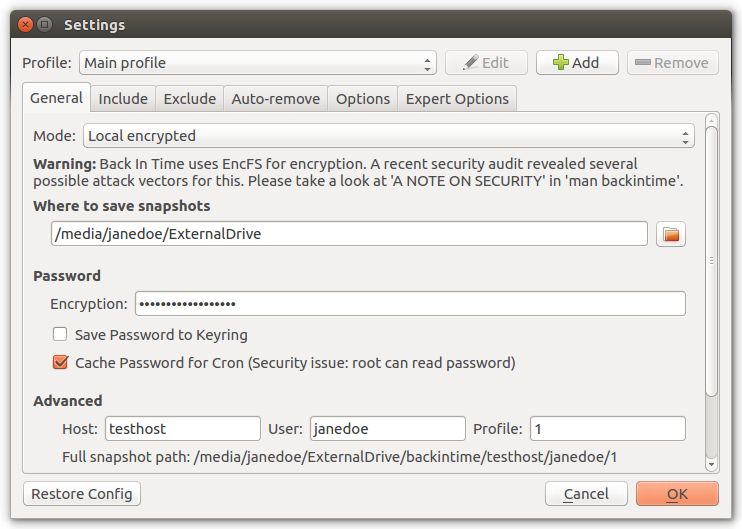
For scheduled backup jobs (cron) you need to check the "cache password for cron" checkbox...
- I enter the password on the screen you have in your last post.
- It's in a corn job. This was the default in BiT.
- This is version 1.2.1 on an Ubuntu system. I used
sudo aptto install it. - The corn is in my user account, so it is started normally or not as root.
- I'm using "Local encrypted", however, I just noticed that "SSH encrypted" can be used. I may switch to that.
- "Save Password to Keying" is grayed out so I cannot use it.
THX for your input, that suffice to look into it (takes some time to come back since we have currently other high prio issues to fix).
One last question: Is the password also lost
- if you just lock the computer and unlock it later (the user session should stay active)
- if you log out the user and do not reboot but login again (so a new user session starts even for the same user)
Regarding 6: To unlock the checkbox a config file must be created and edited See: https://github.com/bit-team/backintime#non-working-password-safe--bit-forgets-passwords-keyring-backend-issues But there is also a bug in 1.2.1 (not fixed in this old version) that requires you to open the dialog twice before it is unlocked (see #1321).
Just browsed the user documentation and saw this description:
https://backintime.readthedocs.io/en/latest/settings.html#local-encrypted
The keyring is unlocked with the users password during login. When running a scheduled backup-job while the user is not logged in the keyring is not available. For this case, the password can be cached in memory by Back in Time.
So I guess it works as designed (but not as I want it as user).
I will look into code anyhow to check if the documentation reflects the current state of code...
As a side note, I'm always logged into this machine unless I'm out of town for an extended period of time. So does this mean that I need to put the encription password in my keychain? This I have not done, but is BiT supposed to do that for me? If so it isn't doing it.
The documentation of the password storage mechanisms and limitations is a little bit hidden I must admit.
There are two ways to store a password in BiT (as you can see in the prev. posted screen shot):
-
(In-memory) caching the password for scheduled
cronjobs so that you can log out (but NOT reboot because the in-memory-password is lost then! -
In the password safe via checking "Save password to keyring". This is persistent but manual and scheduled (
cron) backups can access the password (safe) only if you are actually logged in with your user name and the password safe is unlocked together with the user login into Linux (some password safes may have the option to unlock on the first use instead of the OS login and show a "enter master password" dialog popping up then.
The best documentation I have found so far is man backintime:
Password
If 'Save Password to Keyring' is activated Back In Time will save the Password into GnomeKeyring (Sea‐ horse) or KDE-KWallet. Both are secure password storages which encrypt the password with the users lo‐ gin-password. So they can only be accessed if the user is logged in.
A backup cronjob during the user isn't logged in can not collect the password from keyring. Also if the homedir is encrypted the keyring is not accessible from cronjobs (even if the user is logged in). For these cases the password can be cached in RAM. If 'Cache Password for Cron' is activated Back In Time will start a small daemon in user-space which will collect the password from keyring and provide them for cronjobs. They will never be written to the harddrive but a user with root permissions could access the daemon and read the password.
Can you estimate if this documented password behaviour of BiT is consistent with password disappearance that you observe?
If not there could be a bug or external side effect.
If yes we must improve the documentation and online help...
Edit: So in your case I think it would be better to use the password safe (keyring option in BiT)