aws-deployment-framework
 aws-deployment-framework copied to clipboard
aws-deployment-framework copied to clipboard
ADF Installation from scratch: Step Function not run bootstrap in deployment account
Describe the feature
I created the ADF installation from scratch and in code pipeline the pipeline "[aws-deployment-framework-bootstrap-pipeline]--> finish with success"
My deployment account directly will put in OU deployment in AWS organization.
But unfortunately in deployment account i will not deploy nothing and bootstrap in this account dosen't works.
and i recive the error that i attached:
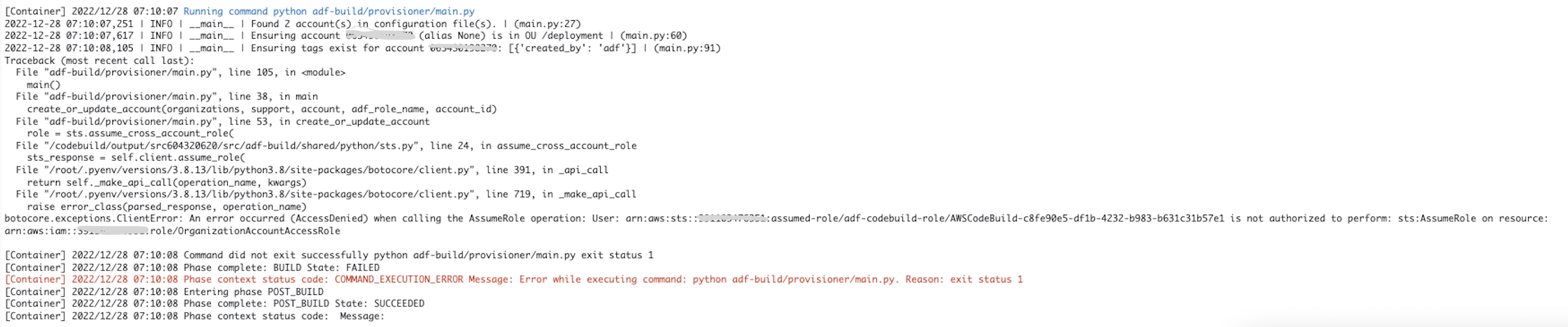
Could you help me please to fix this issue. Thanks a lot.
Use Case
ADF Error bootstrap
Proposed Solution
No response
Acknowledgements
- [ ] I may be able to implement this feature request
Hi @EBO2022E,
Thanks for reaching out. Apologies for not replying earlier.
The adf-build/provisioner/main.py script runs inside the AWS Organization Management Account.
What this process does, is create or update all accounts as defined in the adf-accounts/adf.yml file.
The default account that is added to that file is the deployment account. To ensure it exists and is placed in the deployment OU.
As you mentioned, the deployment account was created before.
So this process will only update that account if needed.
When it tries to assume into the OrganizationAccountAccessRole role, it failed.
Can you verify if that role exists in the deployment account? And can you verify who is allowed to assume that. Typically that should be the management account, like so:
Trusted entities section should be something like this:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::111111111111:root"
},
"Action": "sts:AssumeRole",
"Condition": {}
}
]
}
Where 111111111111 is the account id of the AWS Organization Management account. I.e. where you deployed ADF in the us-east-1 region.
You can retrieve the role (if it exists) in the deployment account with this link: https://us-east-1.console.aws.amazon.com/iamv2/home?#/roles/details/OrganizationAccountAccessRole?section=trust_relationships
If it does not exist, we first need to determine why.
When you create an account from AWS Organizations, you can specify the name of the cross account access role that you would like to have.
If you used Control Tower to create the account, the cross account access role to use is named differently too.
In both cases, remove ADF and deploy it again with the correct CrossAccountAccessRoleName that you can specify when installing ADF.
I hope this helps figure out what went wrong and resolve that.
I am happy to inform you that we released v3.2.0 just now. You might want to give that a try. Updating could resolve the issue too.