pulsar
 pulsar copied to clipboard
pulsar copied to clipboard
Arguments for "why pulsar is secure?"
Search before asking
- [X] I searched in the issues and found nothing similar.
Motivation
When people/companies evaluate open source software to rely and build on they more and more do not only look on its functional value alone but also on topics like
- trust giving name/membership (e.g. part of Apache family)
- existing community size and growth
- development progress and
- especially security.
One thing often done, is a quick automated analysis
- of used dependencies
- their updated state
- number of contained unfixed CVEs (total)
- risk of these CVEs
- number of contained CVEs with available fix (unfixed)
This quick analysis gives a first taste/impression on two things:
- the potential of having a meaningful security problem when using the software
- the awareness of the community for the topic security
Often you do not even have to do the analysis on your own, but you can directly find analysis results using web search.
When doing this for pulsar, you easily find e.g. on artifacthub.io an analysis of the latest official helm chart for Apache Pulsar https://github.com/apache/pulsar-helm-chart
the summarized result of security analysis shows:
992 vulnerabilities (623 fixable) have been detected in this package's images.
In detail:
- there are dependencies with well known security issues (with official CVE numbers)
- there is a pretty huge number of known and documented vulnerabilities: 992
- including important ones (critical, high rating)
- not only in the accompanying software in helm (prometheus, grafana) but in core directly (pulsar)
- some were known for 9 years (CVE numbers from 2013)
- there are possible fixes for most of them (for 623)
see source https://artifacthub.io/packages/helm/apache/pulsar?modal=security-report
Of course, this is only a first rough impression given by this analysis. And the chart does not contain the very latest version of pulsar (even so, it's the latetst official helm chart) When looking into every detail of the reported numbers, you can of course argue why not every counted vulnerabilities is a disaster...
=> But how can you easily argue to anyone having seen this fast result
In general, this software (pulsar) is secure, you can use it without any concerns. ?
Solution
- finding/giving some good arguments e.g. in doc
or
- if this is really not possible today, a way/plan to find a solution to make it possible to say in the near future:
Pulsar is secure, you can use it without any concerns.
Alternatives
No response
Anything else?
No response
Are you willing to submit a PR?
- [ ] I'm willing to submit a PR!
this is how the summary from link above looks like:

some details:

before writing this issue, I had a conversation with Apache Security team, that it is no problem to contribute this as normal issue:
we'd warmly welcome .... if you'd contribute this finding as a normal bug report and/or patch to the project. Since outdated dependencies without further analysis are quite public, there is no need to use this private reporting mechanism in that case.
@hpvd thanks for opening this issue. I think that your point is really valid.
I think that it is appropriate to start this discussion on the mailing lists ([email protected]), as that's the place we run broad discussions.
Regarding this issue: this issue is more about the "Apache Pulsar Helm Chart", that is on https://github.com/apache/pulsar-helm-chart maybe it is better to post your findings there.
Regarding the core Pulsar package we try to keep all the dependencies as up-to-date as possible and to cut releases as soon as problems are discovered and reported to the PMC. Unfortunately the Pulsar Helm Chart is not very active and this is way the default versions, even for the Pulsar docker image are pretty out-dated and we should upgrade
@eolivelli thanks for your comment.
Just opened an issue also in the repository of pulsars helm chart: https://github.com/apache/pulsar-helm-chart/issues/294
would be very interesting to see, how an updated helm chart with
- latest pulsar image (2.9.3 -> 2.10.1 or even 2.11) https://github.com/apache/pulsar
- latest prometheus image (2.17.2 -> 2.39.1) https://github.com/prometheus/prometheus
- latest streamnative/pulsar grafana image (0.0.16 -> no new release but in repository are some commits with updates) https://github.com/streamnative/apache-pulsar-grafana-dashboard
would/will perform in the same scan. => is the update already the big part of the solution?
just as background info, the security scanner used by artifacthub, providing results shown above is trivy, so all the finding should be pretty valid.
For details, see: https://artifacthub.io/docs/topics/security_report/
and trivy https://github.com/aquasecurity/trivy
there is also an easy to use github action for scanning with trivy
- the complete repository,
- pull requests,
- docker container
- IaC
- etc.
=> Maybe this is interesting to integrate this directly into the CI pipeline... See Readme of https://github.com/aquasecurity/trivy-action
number of vulnerabilities is still growing:
Today images in Pulsars helm chart crosses the 1k: 1005 vulnerabilities (683 fixable) have been detected in this package's images. see https://artifacthub.io/packages/helm/apache/pulsar?modal=security-report
Good to know there was hard work done during last week and there will be soon a major update with updated pulsar (2.10.2) and a new monitoring stack https://github.com/apache/pulsar-helm-chart/issues/326
Details and voting: https://lists.apache.org/thread/b02r3605jvmom23p1ccjbzsfwrq5tkjv
new Helm chart v 3.0 on the base of Pulsar 2.10.2 was just released: https://github.com/apache/pulsar-helm-chart/releases/tag/pulsar-3.0.0
Latest security analysis show
- a stunning step in reducing the number of included vulnerabilities (minus 85%!)
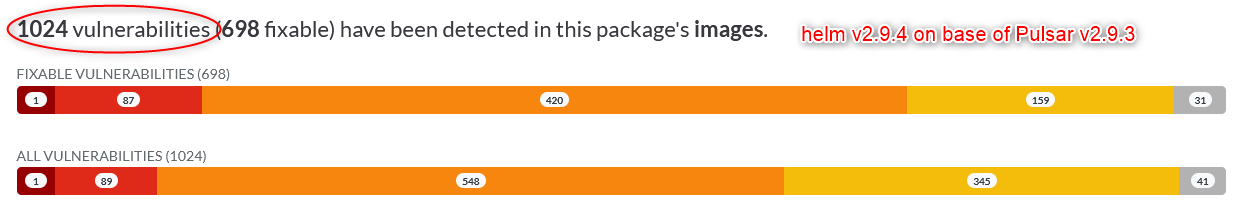
- v2.9.4 with pulsar 2.9.3 1024 vulnerabilities (698 fixable) have been detected in this package's images. https://artifacthub.io/packages/helm/apache/pulsar/2.9.4?modal=security-report
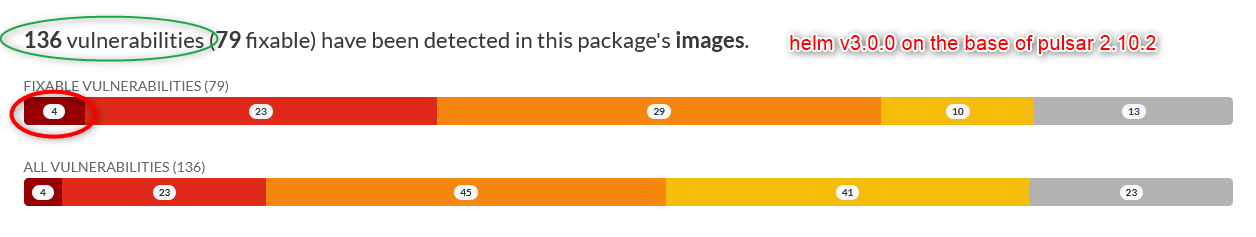
- v3.0.0 with pulsar 2.10.2 136 vulnerabilities (79 fixable) have been detected in this package's images. https://artifacthub.io/packages/helm/apache/pulsar?modal=security-report
- on the other hand
- the number of fixable vulnerabilities with a severity of CRITICAL has risen from 1 to 4 (plus 300%!)
-
- very old fixable and already reported vulnerabilities (up to 9 years old) are still included in pulsar image:
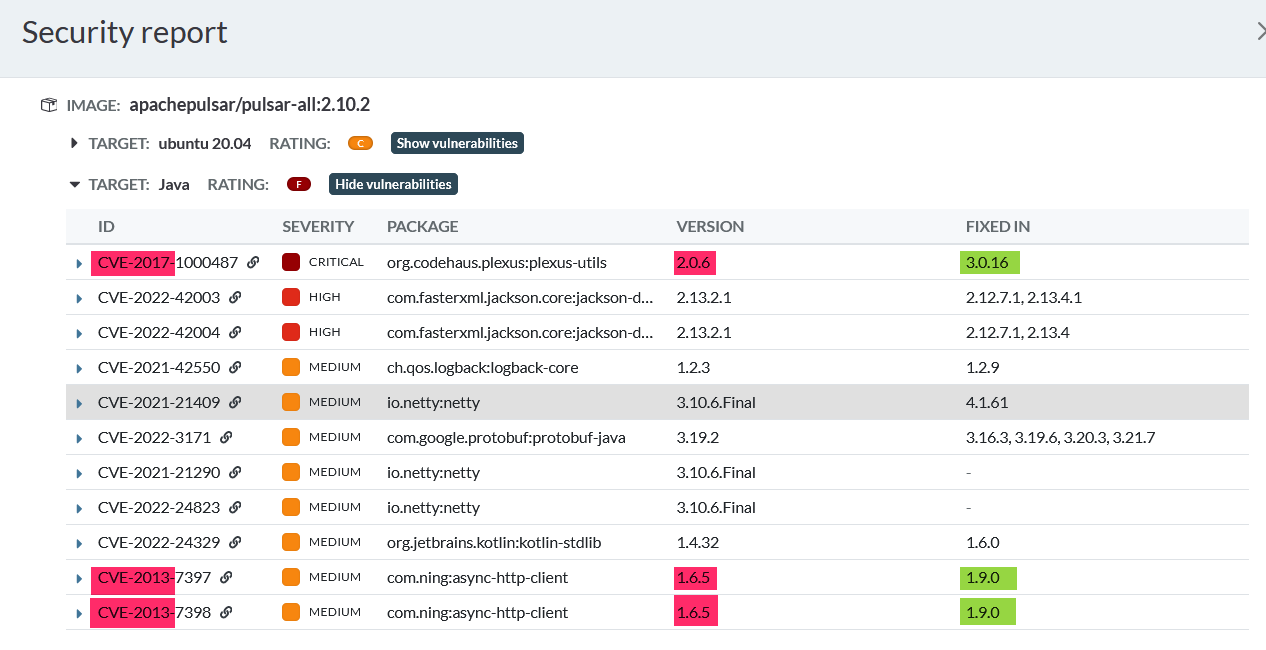
edit: just opened a separate issue for this: https://github.com/apache/pulsar/issues/18338
The issue had no activity for 30 days, mark with Stale label.