pulsar-helm-chart
 pulsar-helm-chart copied to clipboard
pulsar-helm-chart copied to clipboard
[security] helm chart is outdated and includes images with 992 vulnerabilities (623 fixable)
Describe the bug helm chart is outdated and includes images with 992 vulnerabilities
In detail:
- there are dependencies with well known security issues (with official CVE numbers)
- there is a pretty huge number of known and documented vulnerabilities: 992
- including important ones (critical, high rating)
- not only in the accompanying software in helm (prometheus, grafana) but in core directly (pulsar)
- some were known for 9 years (CVE numbers from 2013)
- there are possible fixes for most of them (for 623)
see source https://artifacthub.io/packages/helm/apache/pulsar?modal=security-report
Of course, this is only a first rough impression given by this analysis. And the chart does not contain the very latest version of pulsar (even so, it's the latest official helm chart) When looking into every detail of the reported numbers, you can of course argue why not every counted vulnerabilities is a disaster...
=> But how can you easily argue to anyone having seen this fast result
In general, this software (pulsar) is secure, you can use it without any concerns.
?
This issue is a shortened copy from Arguments for "why pulsar is secure?" https://github.com/apache/pulsar/issues/18041 for more details and comments, please see there.
overview from link above:

more details:
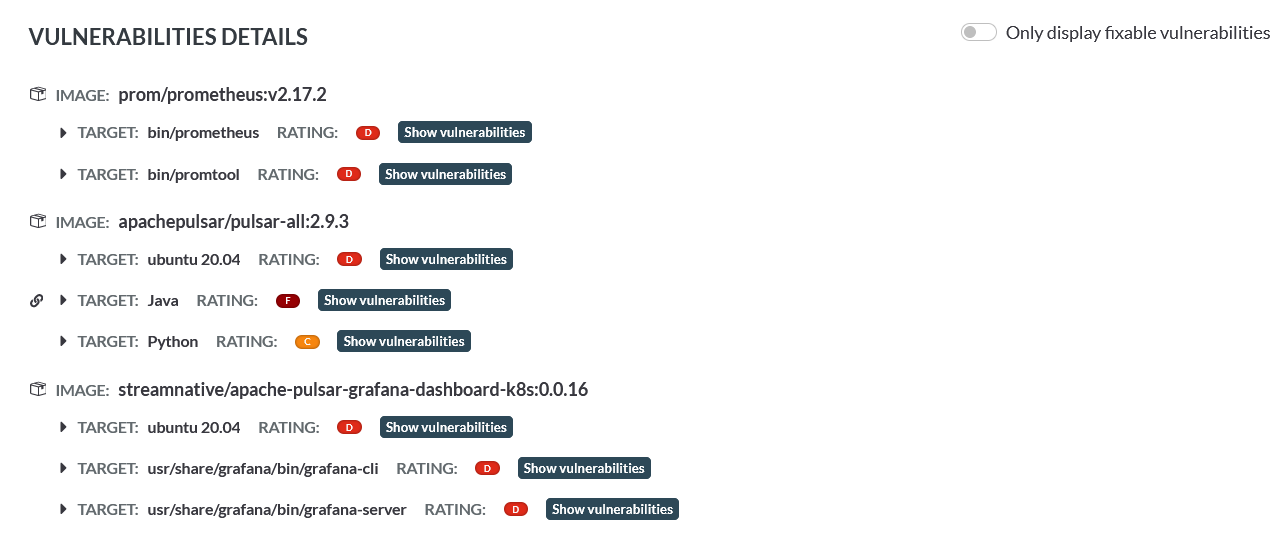
would be very interesting to see, how an updated helm chart with
- latest pulsar image (2.9.3 -> 2.10.1 or even 2.11) https://github.com/apache/pulsar
- latest prometheus image (2.17.2 -> 2.39.1) https://github.com/prometheus/prometheus
- latest streamnative/pulsar grafana image (0.0.16 -> no new release but in repository are some commits with updates) https://github.com/streamnative/apache-pulsar-grafana-dashboard
would/will perform in the same scan. => is the update already the big part of the solution?
@hpvd - thank you for creating this issue. I am going to look into how we can get these issues resolved.
@michaeljmarshall many thanks for starting looking in it that fast and especially your proposal to make a general approach setting the ground to finally solve this (https://github.com/apache/pulsar-helm-chart/pull/299)!
imho this is really important.
just as background info, the security scanner used by artifacthub, providing results shown above is trivy, so all the finding should be pretty valid.
For details, see: https://artifacthub.io/docs/topics/security_report/
and trivy https://github.com/aquasecurity/trivy)
Thank you for raising this issue @hpvd, and thank you for the extra context. It is very important to get the helm chart into a better place. Part of the reform is updating the release process, which I started here #301. This will take some extra time in the beginning, but should lead to easier releases in the future.
@michaeljmarshall
there is also an easy to use github action for scanning with trivy
- the complete repository,
- pull requests,
- docker container
- IaC
- etc.
=> Maybe this is interesting to integrate this directly into the CI pipeline... See Readme of https://github.com/aquasecurity/trivy-action
We could definitely investigate using that tool. For now, I am focused on getting the relevant dependencies upgrade and fixing the release process.
wow just saw the latest release 3.0.0! What a great progress :-)
just did the same quick security check up again:
Latest security analysis show
- a stunning step in reducing the number of included vulnerabilities (minus 85%!)
- v2.9.4 with pulsar 2.9.3 1024 vulnerabilities (698 fixable) have been detected in this package's images. https://artifacthub.io/packages/helm/apache/pulsar/2.9.4?modal=security-report
- v3.0.0 with pulsar 2.10.2 136 vulnerabilities (79 fixable) have been detected in this package's images. https://artifacthub.io/packages/helm/apache/pulsar?modal=security-report
- on the other hand
- the number of fixable vulnerabilities with a severity of CRITICAL has risen from 1 to 4 (plus 300%!)
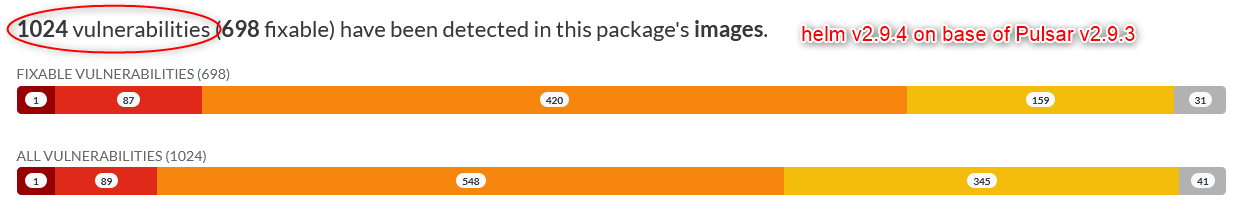
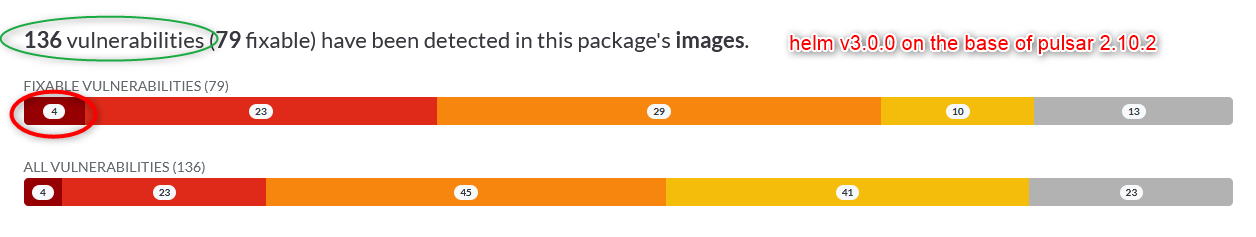
- very old fixable and already reported vulnerabilities (up to 9 years old) are still included:
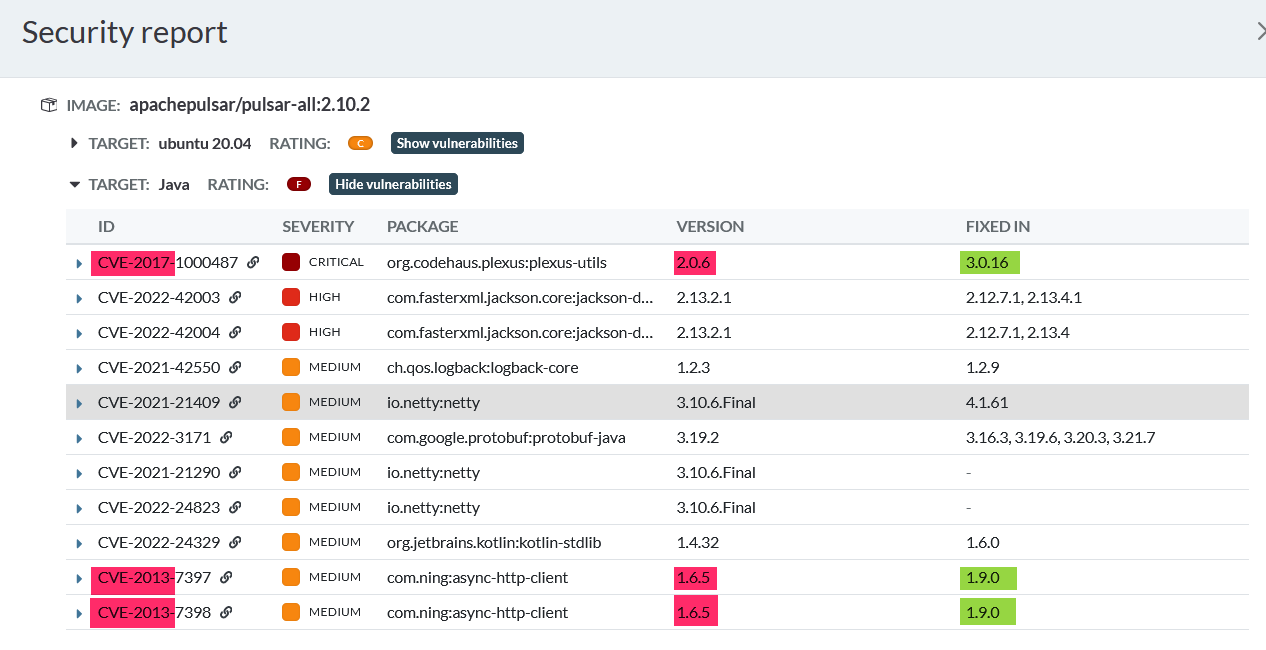
edit: just opened a separate issue for this: https://github.com/apache/pulsar/issues/18338
follow-up issue: https://github.com/apache/pulsar-helm-chart/issues/334
Since we have a follow up issue, can we close this one @hpvd?
@michaeljmarshall Yes I think that's good move!