rita
 rita copied to clipboard
rita copied to clipboard
Consider Bro intel.log as a blacklist data source
Bro has an intel log documented here.
One notable service that integrates with this log is Critical Stack which acts as a sort of blacklist marketplace/aggregator.
The suggestion I have is reading intel.log as a blacklist source. All the matching will already be done and we will just have to report the entries in this file. Users would be responsible for configuring Bro to populate the intel.log as they see fit.
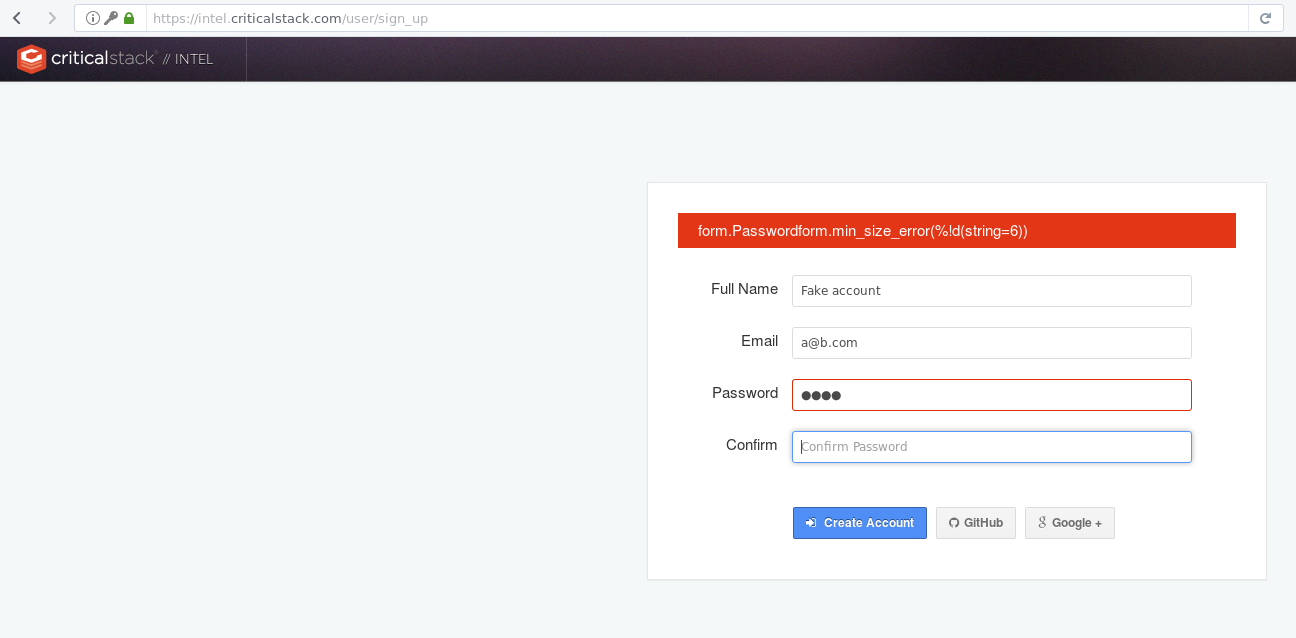 I do not feel comfortable using that critical stack site, and cannot in good faith recommend it.
I do not feel comfortable using that critical stack site, and cannot in good faith recommend it.
- Not sure if that is relevant to the core idea unless there are no other ways for intel.log to be populated with blacklist info. And there seems to be at least one other. Critical Stack was simply an example that a RITA user brought to my attention because they were using it.
- Wondering what your honest take is on actual risk here? Looks to me that they are using a format string incorrectly which is obviously not good but not necessarily a security issue. I'm not sure what language that is but it appears to be server-side rather than JavaScript. Also not good. It's also not the only strange message displayed. However, I'd be more interested to see what their response to a bug report is rather than damning their whole service for one issue.
- Assuming there is real risk here, would the transitive property apply and we need to avoid mentioning Security Onion since they advocate using Critical Stack?
All fair points. Critical Stack seems awesome in theory. I did a quick search and could not find a decent guide for setting up bro's intel log without Critical Stack. The links I did find did not provide anything more than what we are offering with RITA-BL. The link you posted is a tutorial for using the "justdomains" list we are using in RITA-BL with intel.log.
I worry about encouraging the use of this website due to blatant errors in their login page that I feel would have (should have) been noticed.
If Security Onion feels comfortable recommending the site, perhaps I shouldn't be so dismissive.
The feature itself (intel.log) seems nice as it provides a standard way for integrating blacklists. I will have to do some more research into it. Perhaps we could even provide some tools for generating the .dat files for it. I'm not sure that reading blacklist entries from intel.log will play nice with rita-bl / google safebrowsing. I don't know if there is a way to integrate google safebrowing with bro to produce intel.log entries, but that would be ideal if we go down this path.
Just to be clear, I don't think this should replace rita-bl. A rita user requested it as an additional feature, but their main use case is supporting custom blacklists which rita-bl will already do. Since Critical Stack appeared very polished from glancing at their marketing material I thought other users might like the integration. But merging rita-bl in should be the first step and this issue doesn't have any sort of priority right now.
If we go down this route, I would prefer to replace Rita-bl. Managing this feed for blacklist results in addition to Rita-bl's results will become unwieldy rather quickly.
I've done a bit more research into the critical stack website. Looks like they've been acquired by Capital One. Having a backing company makes me feel a bit more comfortable using their site. Additionally, the previous owner of Critical Stack is Liam Randall
I feel better about recommending their services. We should discuss this further in the future.
Sadly Critical Stack has quit developing on their Bro/ Zeek projects: https://github.com/criticalstack/bro-scripts
We will need to find an alternative source of zeek scripts for populating the intel log.
MISP looks interesting for aggregating threat intel feeds and integrating them with Zeek: https://www.misp-project.org/
It looks like there are two integration libraries which handle notifying Zeek of new threat intel data from MISP and notifying MISP of new Zeek sightings.
- Dovehawk (recommended on the MISP tools page): https://github.com/tylabs/dovehawk available via the Zeek package manager
- Threatbus (I've seen recommendations for this on the Zeek mailing list): https://github.com/tenzir/threatbus