openmptcprouter
 openmptcprouter copied to clipboard
openmptcprouter copied to clipboard
VPS Multiple IPs bridged directly to router at home
Is your feature request related to a problem? Please describe. Currently I am using a Wireguard Tunnel on pfsense which is connected to an Ubuntu VPS. This will route all additional IPv4 IPs and an IPv6 /56 to pfsense. This is only used for DMZ services like Exchange, Web etc. Then I ordered a second fiber line which is configured as Multi WAN on pfsense resulting in problems like double IP and missing IPv6 due to dynamic prefix. In addition, this is not used at all for Wireguard because pfsense only supports the default kernel route for Wireguard tunnels. So this will be no bonding but just failover in case of an outage.
Then I found your nice work on Github and started a test config directly. Unfortunately, I am not able to use public IPs at home directly as they were assigned by an ISP. I can only do NAT for all IPs and another NAT or routed setup as described in the pfsense section of your documentation.
Describe the solution you'd like Public IPs directly routed through tunnel and optional layer-2 bridge to a router behind like pfsense or Sophos.
Describe alternatives you've considered Using additional tunnels like GRE, Wireguard or IPsec over MPTCP bonding interface to route everything I want in an inner tunnel -> ugly and higher overhead. Maybe problems with MPTCP mechanism?
Additional context
Current setup I use (2x Fiber Tier 1 load balancing, 1x 5G Tier 2 failover)

My plan using your software (2x Fiber real single stream bonding, 1x 5G failover)
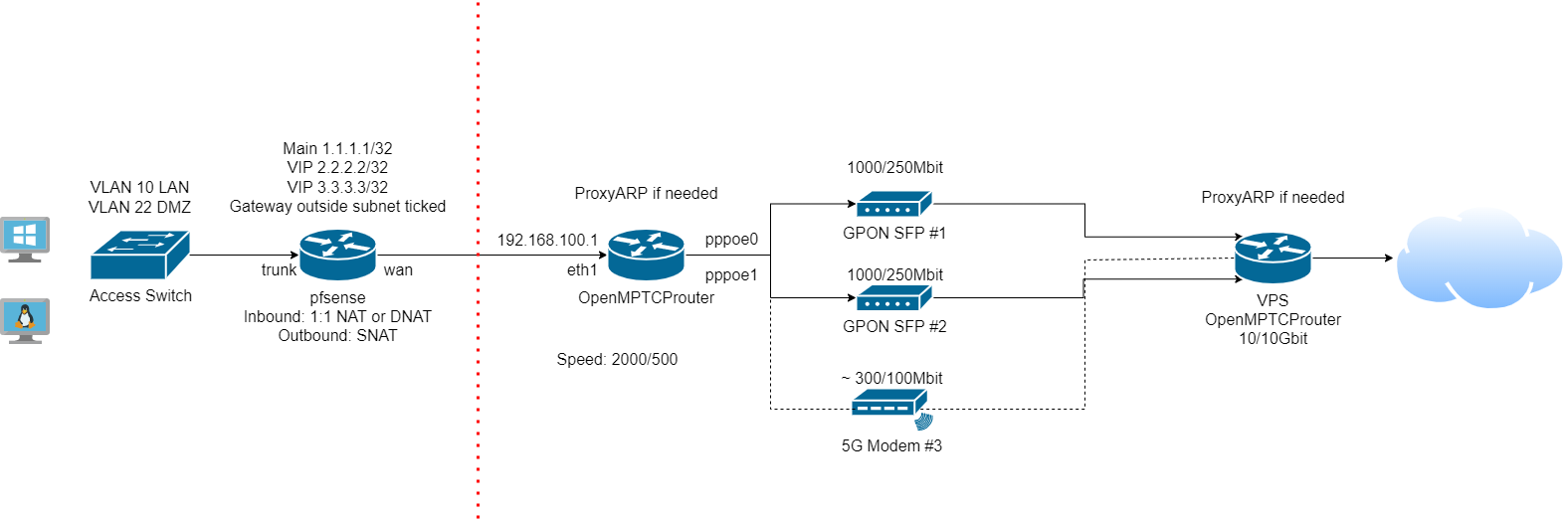
Considers everything before red line as "ISP hardware" which does not matter for pfsense.
I think you have to use a GRE tunnel if you want to get all IPs on pfsense. By default it's what is done to get public IPs on OpenMPTCProuter.
Thanks for your answer. How does this work in principle? GRE is not using either TCP or UDP. How is it distributed over MPTCP?
It's GRE over VPN, the VPN doing the aggregation.
Works but is really slow. Even the direct tun on Openwrt to VPS is slow. So nothing related to pfsense or a VPN on top. Using default Glorytun TCP Started iperf3 -s on VPS
Upload iperf3 -c 10.255.255.1 SUM 368Mbit/s That's fine.
Download iperf3 -c 10.255.255.1 -R SUM 699Mbit/s Not even close to the speed of a single link Same for -P x
Anything that can be improved here?
For comparison omr-iperf vps 459Mbit/s omr-iperf vps -R 1,79Gbit/s
iperf openwrt to client 9,6Gbit / 9,6Gbit
iperf VPS to internet 8,9Gbit / 9,4Gbit
Hardware Openwrt: ESXi Cluster 4 vCore on Xeon E5-2640 v4, 4GiB memory VPS: Proxmox 4 vCore on Xeon E-2136 (root server), 4GiB memory
You can try another VPN in the wizard.
This issue is stale because it has been open 90 days with no activity. Remove stale label or comment or this will be closed in 5 days