[Security] Remove Portis Cookie by Default
From what I can tell a Portis cookie is automatically injected into my application when using the Web3Modal even if I don't have the Portis module installed.
I'm sure the Portis team is great, but I don't particularly want them to have the ability to track me when I'm not even using them as a Web3 provider.
Possible to prevent that?
If you didn't click on their Portis provider then Web3Modal wouldn't trigger the enable... However maybe this is happening from importing their module alone?
Could you test if the cookie doesn't show up if you don't import their module in the app?
You know... It might actually be from the 3Box as they're injecting it via the 3ID-connect and I just falsely assumed it was Web3Modal because I enabled both at around the same time.
Nevermind 😅
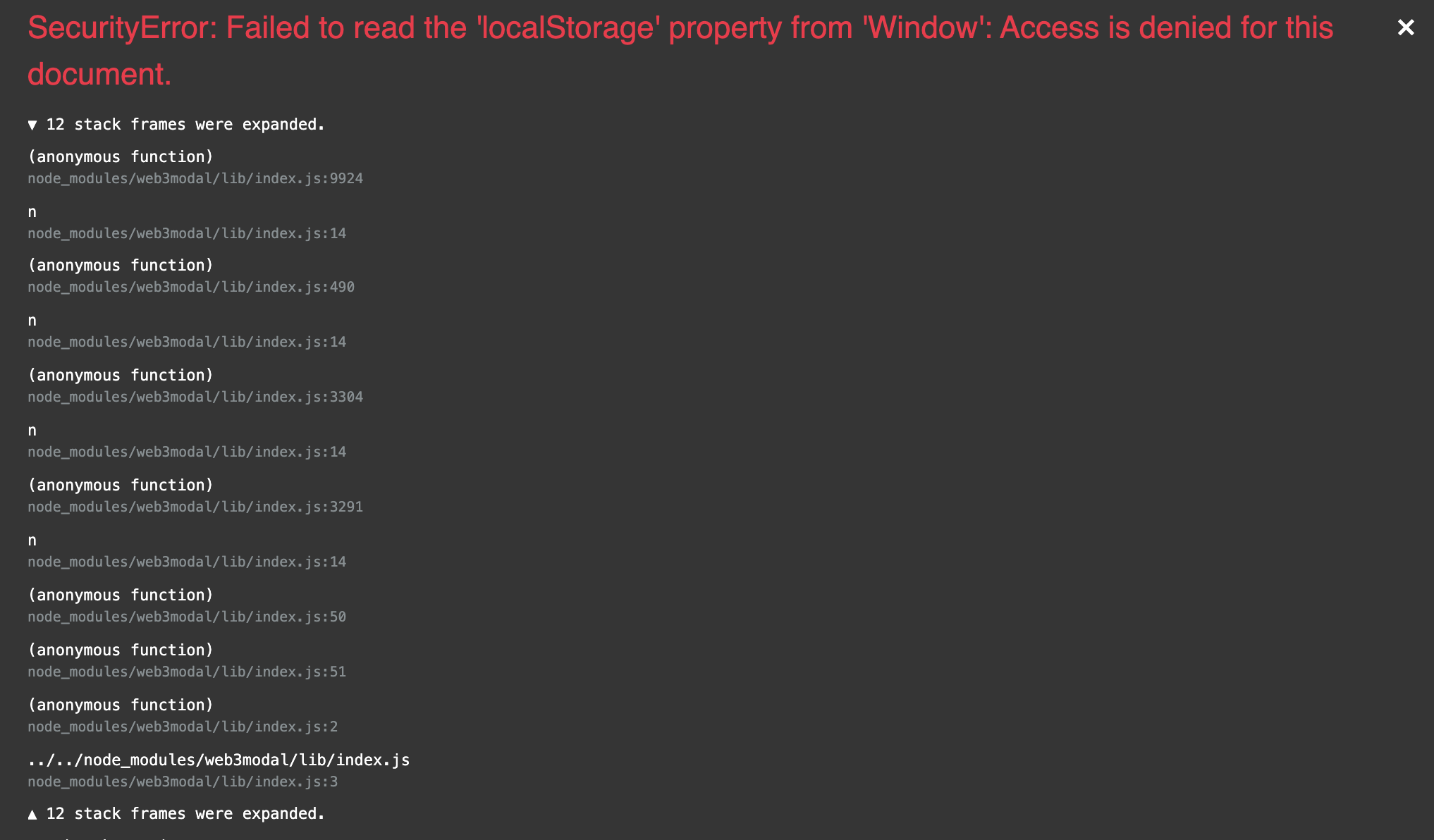
From the stacktrace an error is occurring in Web3Modal when strict cookie settings are enabled though.
Below is a screenshot of Chromium with MetaMask installed and cookies disabled.
Here is the Web3Modal settings with the following dependency versions.
"web3modal": "^1.1.0"
export const web3Modal = new Web3Modal({
network: 'rinkeby', // optional
cacheProvider: false, // optional
providerOptions: {}, // required
});
I think I remember this issue a while back but has since been removed, could you bump the Web3Modal version (latest=1.6.3) or delete the lock file and install again?
With stable version 2.0.0 of Web3Modal now released, we are officially dropping support for version 1.x Due to this this issue/pr was marked for closing. It is highly recommended to upgrade as 2.x will be receiving further updates that will enable functionality for some of our newer sdks like auth and push as well as support for WalletConnect v2 (See this post about WalletConnect v1 being deprecated https://medium.com/walletconnect/walletconnect-v1-0-sunset-notice-and-migration-schedule-8af9d3720d2e)
If you need to continue using Web3Modal 1.x and require this feature/fix implemented, we suggest adding it via forking V1 branch.