tyk
 tyk copied to clipboard
tyk copied to clipboard
[TT-6279] JWT Middleware doesn't allow to use a key provided by the claims.
Branch/Environment/Version master
Describe the bug
It seems that the JWT middleware implement a different hash workflow when we use a "key" attached to a policy to create the token than the one implemented in API_KEY. It results an impossibility to load a session from REDIS based on a created key.
Reproduction steps Steps to reproduce the behavior:
- Add an API with JWT auth
- Add a Policy
- Create a key with the POST method
- Try to connect with the key hash/id to the API.
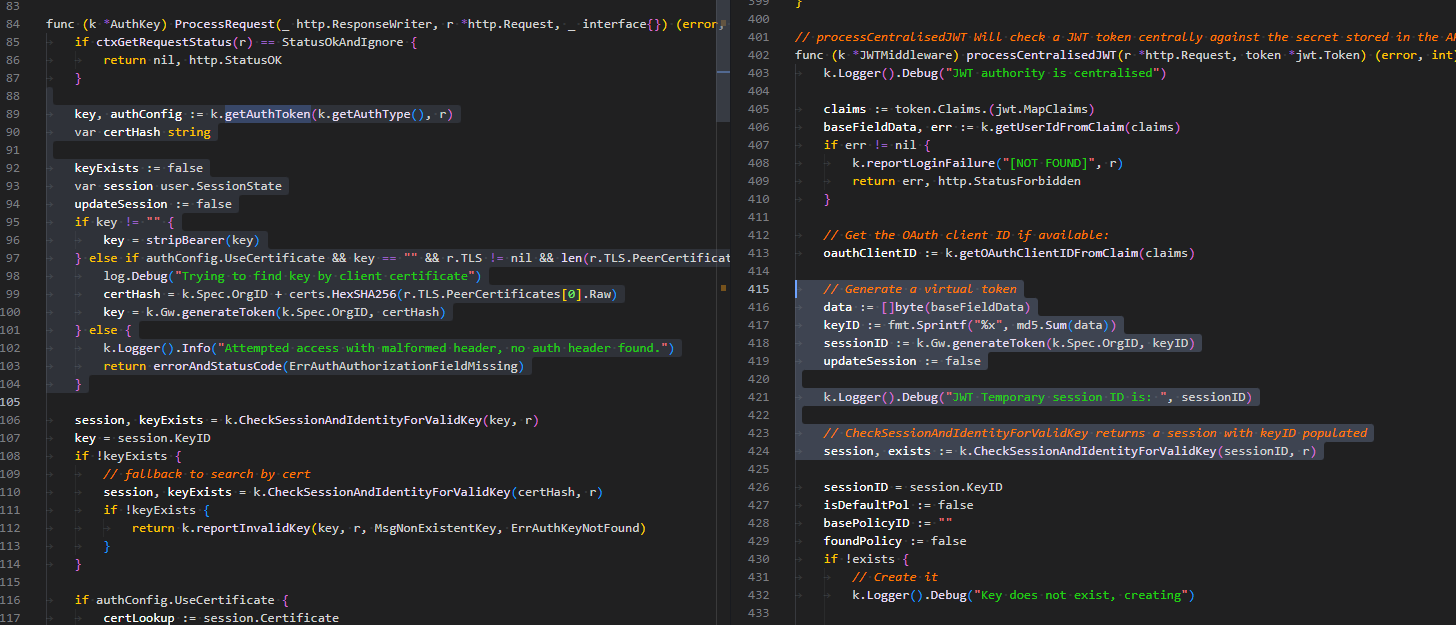
Actual behavior Currently the key that i provide is re-hashed (unconditionnaly) at fly in the "processCentralisedJWT" method ligne 416 and 417. With this fragment of code :
// Generate a virtual token
data := []byte(baseFieldData)
keyID := fmt.Sprintf("%x", md5.Sum(data))
sessionID := k.Gw.generateToken(k.Spec.OrgID, keyID)
This disallow the possibility to load a key from the store because keyID will never be the same as the one registered. At the opposite, in mw_auth_key.go we can find the good pattern :
key, authConfig := k.getAuthToken(k.getAuthType(), r)
[...]
session, keyExists = k.CheckSessionAndIdentityForValidKey(key, r)
Expected behavior
We need to be able to load the session and its attached policies from a key provided by the JWT claim.
Screenshots/Video
Do not hesitate to ask for details if it isn't clear enough.
Best regards.
Hi @Dje-G, thank you for submitting this in the detail that you have.
I'll relay this to our support and internal engineers.
Hello any update here?
Hello @jgouro-hub, I am not sure what you are looking to do here. Can you please explain the use case? When you talk about reproduction steps. What JWT Signing Method are you using to validate the JWT? Which POST endpoint are you hitting? What does the key look like?
We don't understand and cannot reproduce the issue you're reporting here, as the use case is not clear.
If you're still having problems, please don't hesitate to comment with an explanation of what you're trying to do, then we can re-open the ticket.
Thank you for supporting Tyk!