Cyberonix
 Cyberonix copied to clipboard
Cyberonix copied to clipboard
Cyberonix is a complete resource hub for Cyber Security Community. Our aim is to make this tool an 1 stop solution for all the Hackers out there to get resources of various topics in Cyber Security. W...
CYBERONIX











Description
Cyberonix is an open source & free tool by Team Defronix Cyber Security Pvt. Ltd. The tool at first is developed by a team of students as part of their Internship at Defronix Solution after their Diploma in Cyber Security Training.
It is a complete resource hub for Cyber Security Community. Our aim is to make this tool an 1 stop solution for all the Hackers out there to get resources of various topics in Cyber Security. We will keep updating this tool & adding new & updated resources on the go.
Feel free to suggest any feature that you want to see in this tool, We will be happy to include that in our next update.
Install
Usage
Categories
ScreenShots
Contributors
Installation
sudo apt update -y && apt full-upgrade -y
git clone https://github.com/TeamDefronix/Cyberonix.git
cd Cyberonix
chmod +x setup.py
sudo python3 setup.py
cyberonix
PIP intallation
pip install cyberonix
If you get Externally-Managed-Environment issue in your machine please check this blog click here
Usage
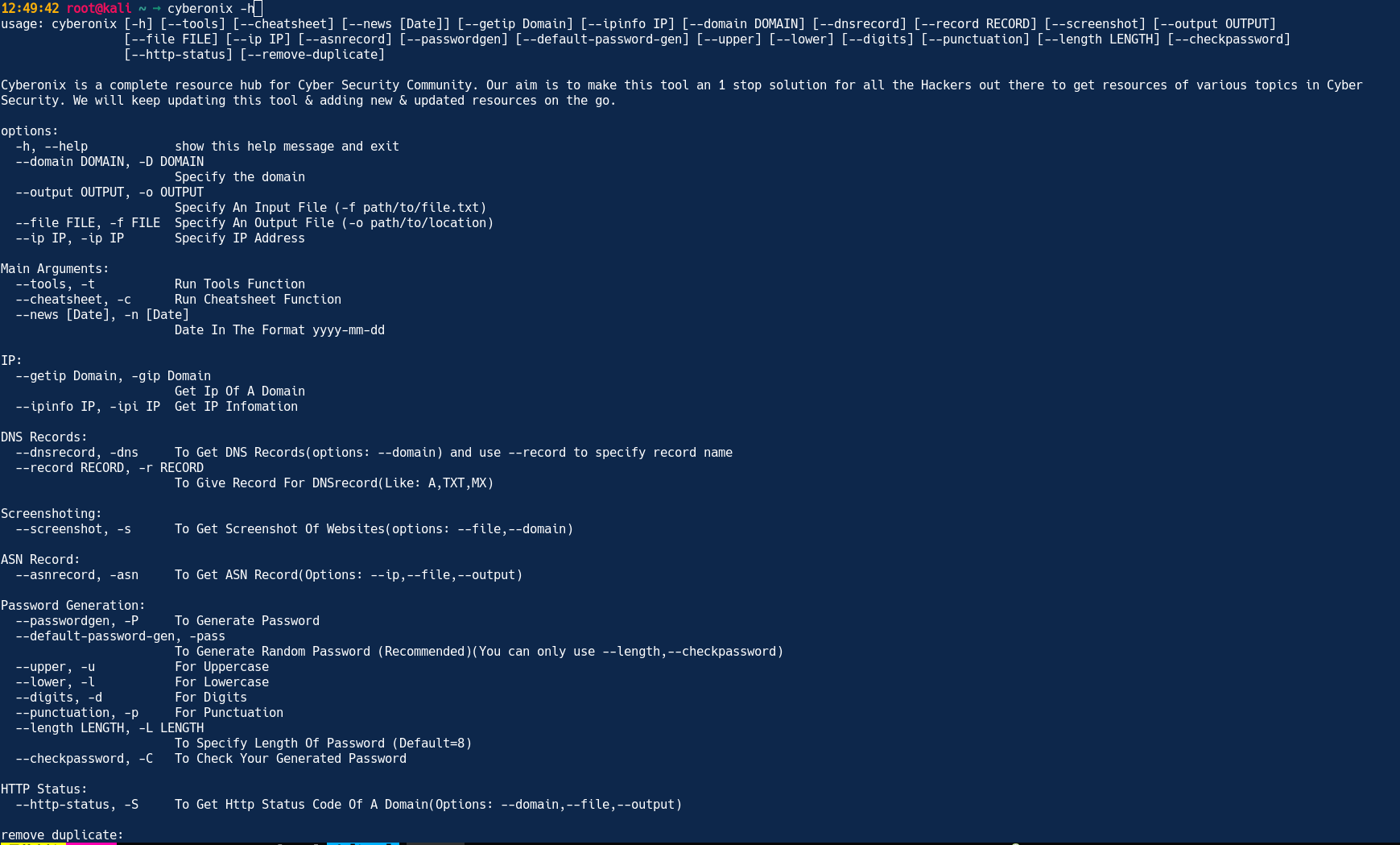
cyberonix -h
ctrl+c for exit
enter for back
Please find below the instructions to access the tool's help function, along with a list of all available switches:
Cyberonix is a complete resource hub for Cyber Security Community. Our aim is to make this
tool an 1 stop solution for all the Hackers out there to get resources of various topics in
Cyber Security. We will keep updating this tool & adding new & updated resources on the go.
options:
-h, --help how this help message and exit
--domain DOMAIN, -D DOMAIN Specify the domain
--output OUTPUT, -o OUTPUT Specify An Output File (-o path/to/location)
--file FILE, -f FILE Specify An Input File (-f path/to/file.txt)
--ip IP, -ip IP Specify IP Address
Main Arguments:
--tools, -t Run Tools Function
--cheatsheet, -c Run Cheatsheet Function
--news [Date], -n [Date] Date In The Format yyyy-mm-dd
IP:
--getip, -gip Get Ip Of A Domain(options: --file,--domain,--output)
--ipinfo, -ipi Get IP Infomation(Options: --ip,--file,--output)
DNS Records:
--dnsrecord, -dns To Get DNS Records(options: --domain,--file,--output) and use --record to specify record name
--record RECORD, -r RECORD To Give Record For DNSrecord(Like: A,TXT,MX)
Screenshoting:
--screenshot, -s To Get Screenshot Of Websites(options: --file,--domain,--output)
ASN Record:
--asnrecord, -asn To Get ASN Record(Options: --ip,--file,--output)
Password Generation:
--passwordgen, -P To Generate Password
--default-password-gen, -pass
To Generate Random Password (Recommended)(You can only use --length,--checkpassword)
--upper, -u For Uppercase
--lower, -l For Lowercase
--digits, -d For Digits
--punctuation, -p For Punctuation
--length LENGTH, -L LENGTH To Specify Length Of Password (Default=8)
--checkpassword, -C To Check Your Generated Password
HTTP Status:
--http-status, -S To Get Http Status Code Of A Domain(Options: --domain,--file,--output)
remove duplicate:
--remove-duplicate, -rd To Remove Dublicates From a File(Options: --file,--output)
Categories
-
Tools
-
Information Gathring
NmapMaltegoDracnmapRed_HawkTh3InspectorHping3ArpingNetdiscoverWafw00f
-
Vulnerability Analysis
WpscanWapitiNmapLegionNikto
-
Web Application Analysis
Burp SuiteOwasp ZapNiktoWapitiNessusDirbSkipfishNuclei
-
Password Attacks
-
Brute Force Attacks
HashcatJohn The RipperHydraJohnnyCrackstatiioncyberchef
-
Dicitionary Attacks
HashcatJohn The RipperHydraMedusaNrackJohnnyCrackstationCyberchef
-
Rainbow Table Attacks
RainbowcrackOphcrack
-
Wordlist Generator
Social-EngineerHiddeneyeR3Bu5ZphisherShellphishGophish
-
Phishing Attacks
Social-EngineerHiddeneyeR3Bu5ZphisherShellphisGophish
-
Keylogger Attacks
Zlogger
-
-
Wireless Attacks
KismetWifiteFern Wifi CrackerAircrack-NgFluxionWifiphisherBettercap
-
Exploitation Tools
MetasploitCrackmapexecSearchsploitBeefRoutersploitSqlmapAirmitageCommix
-
Sniffing And Spoofing
WiresharkBettercapTcpdumpArpspoofDsniffScapyNetsniff-NgMacchangerResponderAirgeddonSharesnifferWifi-Pumpkin-3
-
Post Exploitation
-
Privilege Escalation
Metasploit-FrameworkLinpeasSudo KillerBerrotLinux Exploit Suggester 2LsePspyBasharkLinux Private-I
-
Maintain Access
Metasploit-FrameworkShellterAmberUpx
-
Clearing or Removing Tracks
Metasploit-FrameworkCovermyass
-
-
Pentesting And Bug-Bounty
-
Information Gathering
NmapMaltegoDracnmapRed_HawkTh3InspectorHping3ArpingNetdiscoverWafw00F
-
Configuration Management
DirbgobusterNiktoWfuzzSkipfishDirbusterFeroxbusterNmapHttpieMetasploitSecurityheadersSqlmapTrufflehogGitleaksSecretfinder
-
Secure Transmission
-
Writeups
Check Ssl Version, Algorithms, Key LengthCheck For Digital Certificate ValidityCheck Credentials Only Delivered Over HttpsCheck Session Tokens Only Delivered Over HttpsCheck If Http Strict Transport Security (Hsts) In Use
-
-
Authentication
User EnumerationAuthentication BypassVulnerable Remember Me FunctionalityPassword ResetCaptcha BypassAutocomplete OnMultifactor AuthenticationLogout FunctionalityCache ManagementDefault Credentials
-
Session Management
Owasp ZapBurpsuiteNiktoNmapWapitiNessusNucleiFiddlerPenetration Testers Framework (Ptf)
-
Authorization
BurpsuiteWiresharkOwasp ZapNessusHydraBeefSqlmapMetasploitNmapPenetration Testers Framework (Ptf)
-
Data Validation
XssXxe - XmlHtml InjectionSql InjectionCommand InjectionHttp SmugglingHttp Parameter PollutionOpen RedirectionLfi
-
Denial Of Service
GoldeneyeSlowhttptestThc-Ssl-DosSlowloris
-
Business Logic
-
Writeups
Business LogicExploiting Business Logic VulnerabilitiesWeb Application — Business Logic VulnerabilitiesBusiness Logic Flaw
-
-
Cryptography
SslstriptBettercapEttercap (Graphical Of Bettercap)Sslyze0-SaftSslscanSsllabs
-
Risky Functionality - File Uploads
FuxploiderFuse
-
Risky Functionality - Card Payment
BurpsuiteWiresharkOwasp ZapNessusSqlmapFiddlerMetasploitNmapPenetration Testers Framework (Ptf)
-
Html 5
-
Writeups
Web MessagingWeb Storage Sql InjectionCors ImplementationOffline Web Application
-
-
-
-
Cheatsheets
Nmap CheatsheetMaltego CheatsheetHping3 CheatsheetNetdiscover CheatsheetWafw00F CheatsheetMetasploit-Framework CheatsheetWireshark CheatsheetBettercap CheatsheetTcpdump CheatsheetScapy CheatsheetResponder CheatsheetAirgeddon CheatsheetWpscan CheatsheetWapiti CheatsheetLegion CheatsheetNikto CheatsheetBurp Suite CheatsheetOwasp Zap CheatsheetNessus CheatsheetDirb CheatsheetSkipfish CheatsheetNuclei CheatsheetWifite CheatsheetAircrack-Ng Cheatsheet
-
News
Date Wise
ScreenShots