start-os
 start-os copied to clipboard
start-os copied to clipboard
[feat]: Allow services to use HTTPS internally for .local
Steps to reproduce:
- Install and run CLN
- try to access <.local-address>:3001 (where the rest api is listening)
- bad gateway:
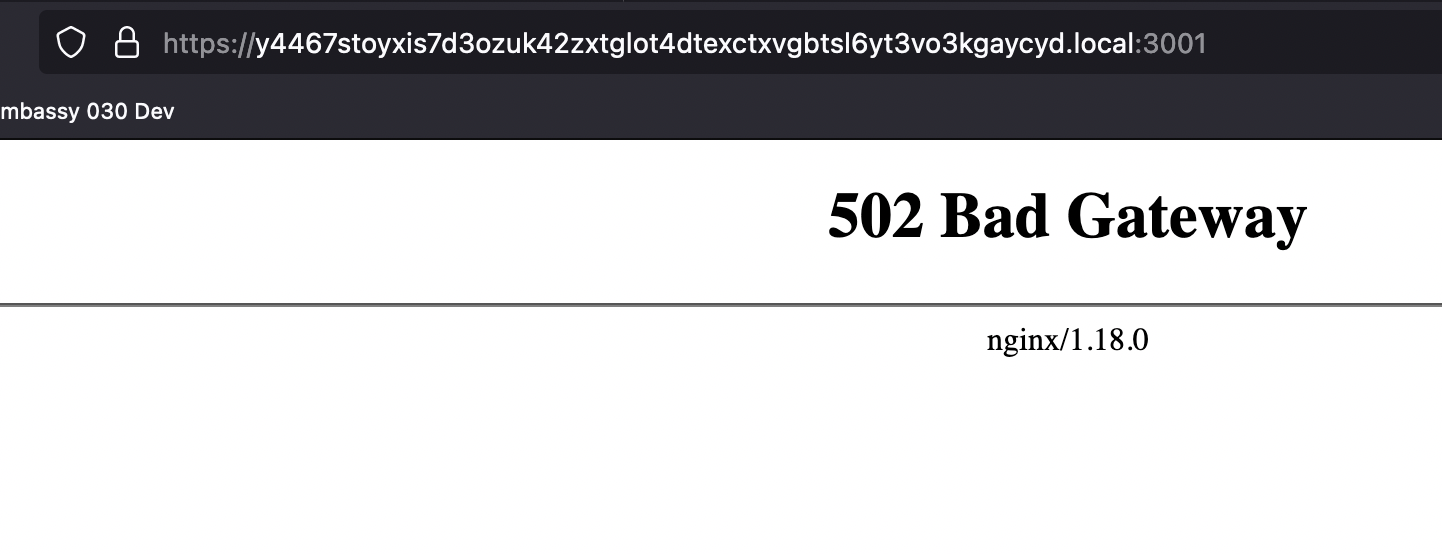
CLN lan config looks like:
rest:
name: C-Lightning-REST API
description: C-Lightning-REST is a plugin for Core Lightning written by the RTL team that exposes an LND-like REST API for C-Lightning.
tor-config:
port-mapping:
3001: "3001"
lan-config:
3001:
ssl: true
internal: 3001
ui: false
protocols:
- tcp
- http
(see https://github.com/Start9Labs/c-lightning-wrapper/blob/357043734b7df0cf4c41ae5526d70ff9ea5dcf84/manifest.yaml#L116-L129 for whole config spec)
nginx config looks like:
server {
listen 3001 ssl;
listen [::]:3001 ssl;
server_name .y4467stoyxis7d3ozuk42zxtglot4dtexctxvgbtsl6yt3vo3kgaycyd.local;
ssl_certificate /etc/nginx/ssl/c-lightning/rest.cert.pem;
ssl_certificate_key /etc/nginx/ssl/c-lightning/rest.key.pem;
location / {
proxy_pass http://172.18.0.3:3001/;
proxy_set_header Host $host;
proxy_set_header X-Forwarded-Proto $scheme;
client_max_body_size 0;
proxy_request_buffering off;
proxy_buffering off;
proxy_http_version 1.1;
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection $connection_upgrade;
}
}
I can curl the endpoint from on the embassy. No 502 here:
root@embassy-2ef08502:~# curl -k https://172.18.0.3:3001
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="utf-8">
<title>Error</title>
</head>
<body>
<pre>Cannot GET /</pre>
</body>
</html>
I can't figure out why this wouldn't work except for some kind of OS bug.
Thoughts?
out of curiosity if you set the outer port to 443, do things work?
Not sure if changing the outer port to 443 works better or not. Now I just get redirected to the embassy login page. Same result in curl.
For the record, I also can't get this interface to work over Tor either, but I'm not sure if that's because of the current Tor ddos attack.
issue here looks like that it's using ssl internally
Are you suggesting that i turn ssl to false?
i suppose i could also use the system cert
no, I'm saying the issue is here:
curl -k https://172.18.0.3:3001
you are using https to hit the container. the system is not set up to allow this, and wouldn't be able to verify the authenticity of the cert even if it could
So what's the fix?
The rest api requires https, obviously, otherwise a middleman can steal the macaroon
Tried it with ssl: false in the manifest and the output is different, but still not working. guessing you were saying this
% curl -k https://kyikw2zkhwye3zpenl35bizk7vowsn4mxs3hyxxgjijosjhriru2iwid.local:3001
curl: (35) error:1400410B:SSL routines:CONNECT_CR_SRVR_HELLO:wrong version number
Ok at least i figured out Tor. Forgot to put https:// when connecting over Tor xD
% curl -k --socks5-hostname localhost:9050 https://kyikw2zkhwye3zpenl35bizk7vowsn4mxs3hyxxgjijosjhriru2iwid.onion:3001
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="utf-8">
<title>Error</title>
</head>
<body>
<pre>Cannot GET /</pre>
</body>
</html>
The rest api requires https, obviously, otherwise a middleman can steal the macaroon
The system should be managing the SSL. If the container requires its own SSL, how is it generating that cert and how would you expect that cert to be communicated to the end user?
You need to disable the SSL tunnel between nginx and the CLN container. SSL will be handled between the client and nginx as normal.
I'm just trying to ascertain whether accessing https services on ports other than 443/80 is possible at all. Currently the plugin is generating its own cert, but this is not necessary; I'm reasonably certain we could use a system cert. Either way, we could communicate the cert to the end user in the same way we do on LND... by outputting the base64 encoding of the cert to the properties. Or we could offer a .crt file for download. Zeus, for instance, tells the user to install the cert on their phone:
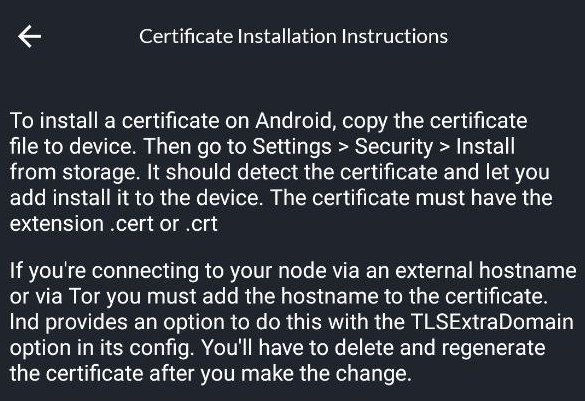
I just want to know if it's even worth going down this road, since I'm having trouble getting this connection to work at all, under any circumstances.
You need to disable the SSL tunnel between nginx and the CLN container. SSL will be handled between the client and nginx as normal.
Is this the fix? How do I do this?
the underlying service ideally needs to not use ssl the OS can add ssl on lan, and tor has tls built in if this is not possible, you need to use the system generated cert, and we need an os feature to connect to the service over lan with https, which is out of scope for 0.3.1
Ahhh I see now, thanks. Yes, it looks like it's possible to disable https on the underlying service: https://github.com/Ride-The-Lightning/c-lightning-REST#configuration-parameters
Just need to set PROTOCOL to http.
As for the OS feature to connect via lan with HTTPS, that does seem useful as there are several services that don't allow disabling SSL (for instance, LND).
Renaming this issue to reflect the new status.
Linked to #1594