seldon-core
 seldon-core copied to clipboard
seldon-core copied to clipboard
Critical Vulnerability in operator/executor
Describe the bug
There's a critical vulnerability in the latest seldon release
Using trivy version 0.22.0 ran trivy image --severity CRITICAL seldonio/seldon-core-operator:1.12.0 I obtained the following report
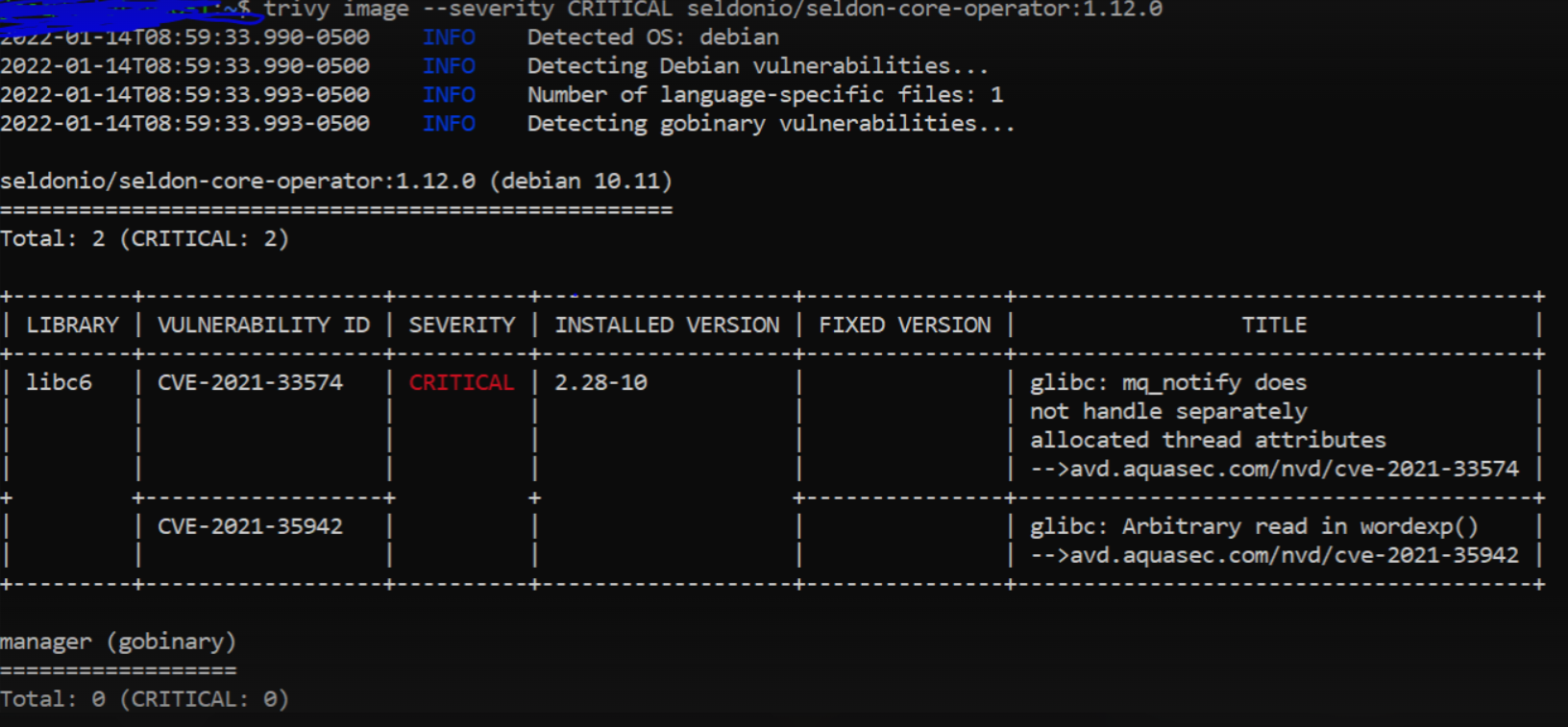
This is the same result if I run trivy image --severity CRITICAL seldonio/seldon-core-executor:1.12.0
To reproduce
Install trivy version 0.22.0
Run trivy image --severity CRITICAL imagename
Expected behaviour
For the result of the trivy scan to be empty
@Jose-Matsuda thank you for reporting the vulnerability - we have security scans that use snyk as well to ensure we identify any potential vulnerabilities as well, however we use the flag --fail-on=upgradable which means the alerts that appear on security vulnerabilities that don't have an upgrade path yet don't have an action we can carry out. Would you be able to provide more context on the vulnerabilitiy? From our current setup it seems there's no current "fix-path" but if you have furhter context we can have a further look.
Thanks for the quick response and for letting me know about your snyk scans! Sorry I don't have more context, my team was just doing some cleanup and noticed this vulnerability so we looked through this repo and could not find an issue.
The action here is just to wait until there's an upgrade for the library and then the team would patch it correct?
That is correct - once there is a version with a fix we'll be able to make sure we update, this is also one of the reasons why we differentiate with the flag mentioned above. You can find the results from the security tests here https://github.com/SeldonIO/seldon-core/actions/workflows/security_tests.yml
Please try latest