Correlation between entities using weighted relationships and graph computation (Modelisation overlap threat actor)
Problem to Solve
In Cyber Threat Intelligence, a threat (or threat actor) is basically an appellation which is arbitrary chosen by the security editor or CERT which is describing it. In a nutshell, an editor's appellation reflects its understanding and/or its visibility on its own telemetry over a malicious activity realized by a threat actor. Therefore, there is no direct link between two distinct appellations, but rather an overlap between two distinct activities associated with two distincts threat actors.
Identifying these overlaps is crucial to understanding the organisation of the attackers, their capabilities or their objectives and this is especially important when considering a paranomic view of threat actors. However, this notion of overlap is often reduced to a notion of "link" between threat actors or to the notion of aliases.
Current Workaround
The threats dashboard located at "/dashboard/threats/threat_actors?" shows either a list or a mosaic of threat actors, based on the name reported by the security editors in their reports. The dashboard doesn't highlight the notion of overlap between these actors, and the analyst is facing many different appellations, which can be misleading. Furthermore, this view lacks of a global panorama, as the number of distinct appellations will increase over the years.
Proposed Solution
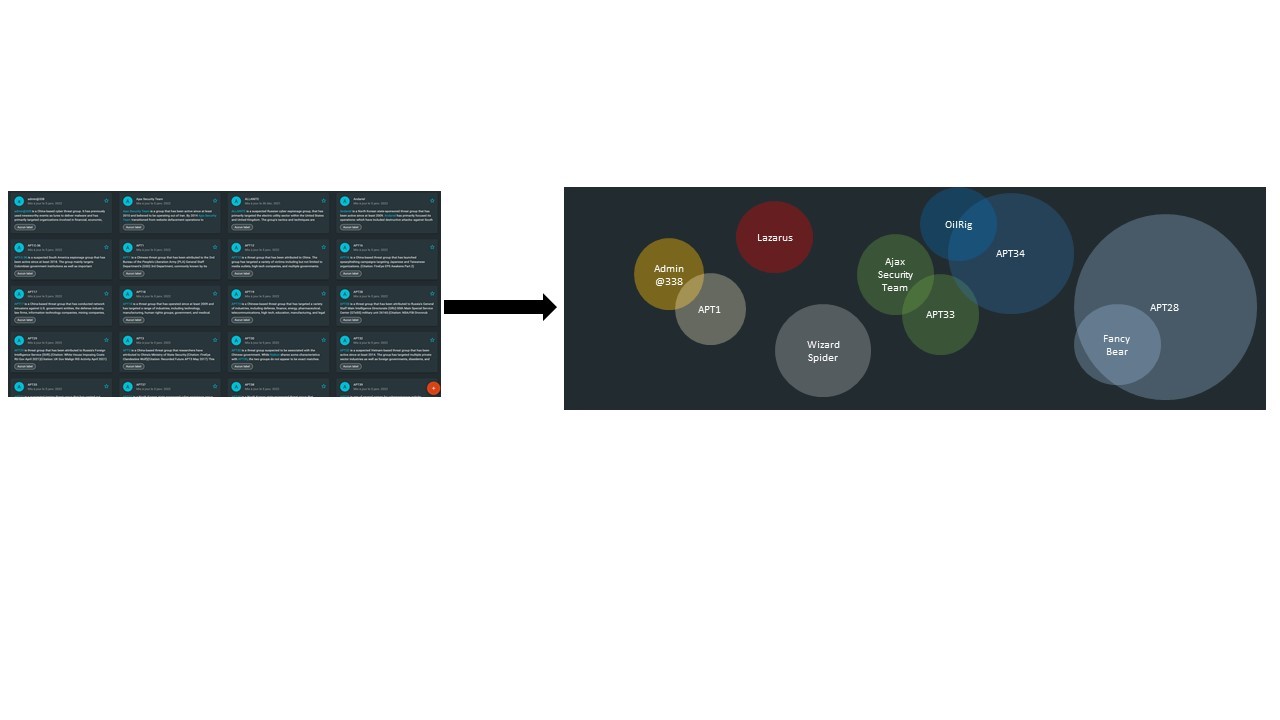
A solution to this situation would be to create another view in the threats dashboard. This view would be focused on the notion of overlap between the threat actors. Therefore, the threat actors would be modelized through circles which radius will be proportionnal to the number of technical elements (IOC) linked to the threat actors. This scale would allow the users to have a quick understanding on the threats actors on which they do have the most important volume of datas.
Several solutions are possible to modelize the notion of overlap between two circles associated with two distinct threat actors :
-
solution A : the overlap is quantified through the number of STIX Cyber-observable linked to both threat actors. This approach is the most simple way to represent the overlap between threat actors in a panoramic view ;
-
solution B : the overlap is quantified through a polynomial expression, as for example <OVERLAP=aX+bY+...+n*Z>, where X, Y and Z represent a coefficient specific for each kind of STIX Cyber-observable Objects and a, b or n stand for the number of distinct values of each kind of STIX Cyber-observable Objects linked to both threat actors. This approach is a bit more complex, as each specific coefficient has to be defined prior any modelisation. However, it allows the analyst to injects some Cyber Threat Intelligence model in this modelization, as for example the Pyramid of Pain.
-
solution C : same approach than solution B regarding the calculation of the OVERLAP. However, this approach will also take into consideration the temporality of each cyber activity linked to the STIX Cyber-observable Objects. This will be symbolized by addtional threshold values, which will stand for the minimum overlap to have in order to consider that two distinct threat actors present indeed overlap or the minimum value to affirm that two distinct threat actors are indeed aliases. Both of these threshold values will be function of time, in order to increase the overlap between two threat actors if the similar cyber activities are temporaly close.
Additional Information
Related to #1516. Be able to modelize correlation as overlapping bubbles computing means.
From another user: There is a need for intelligent fuzzy matching of threat actor names to help with housekeeping and deduplication . For example, matching variations like "BlackBasta" and "Black Basta" . Proposed features: Implement fuzzy matching algorithm to detect similar threat actor names Present potential matches to users for review, similar to contact merging in Apple products Add configurable threshold settings: Allow automatic merging above certain similarity threshold Require manual review below threshold Important considerations: This is primarily for housekeeping purposes, not threat actor attribution Technical intelligence (like IOCs) can vary significantly between vendors for the same actor, so matching should focus on naming patterns