www-project-top-25-parameters
 www-project-top-25-parameters copied to clipboard
www-project-top-25-parameters copied to clipboard
OWASP Foundation Web Respository
OWASP Top-25 Parameters
For basic researches, top 25 vulnerability parameters that can be used in automation tools or manual recon
What is top25-parameter 🧙⚔️
For basic researches, top 25 vulnerable parameters based on frequency of use with reference to various articles. These parameters can be used for automation tools or manual recon. Although the prevalence percentages of these parameters cannot be proven precisely, they were prepared by the TR Bug Hunters Community, which I founded, and myself.
This repo contains common parameters of the following vulnerabilities:
ToC
- Cross-Site Scripting
- Server-Side Request Forgery
- Local File Inclusion
- SQL Injection
- Remote Code Execution
- Open Redirect
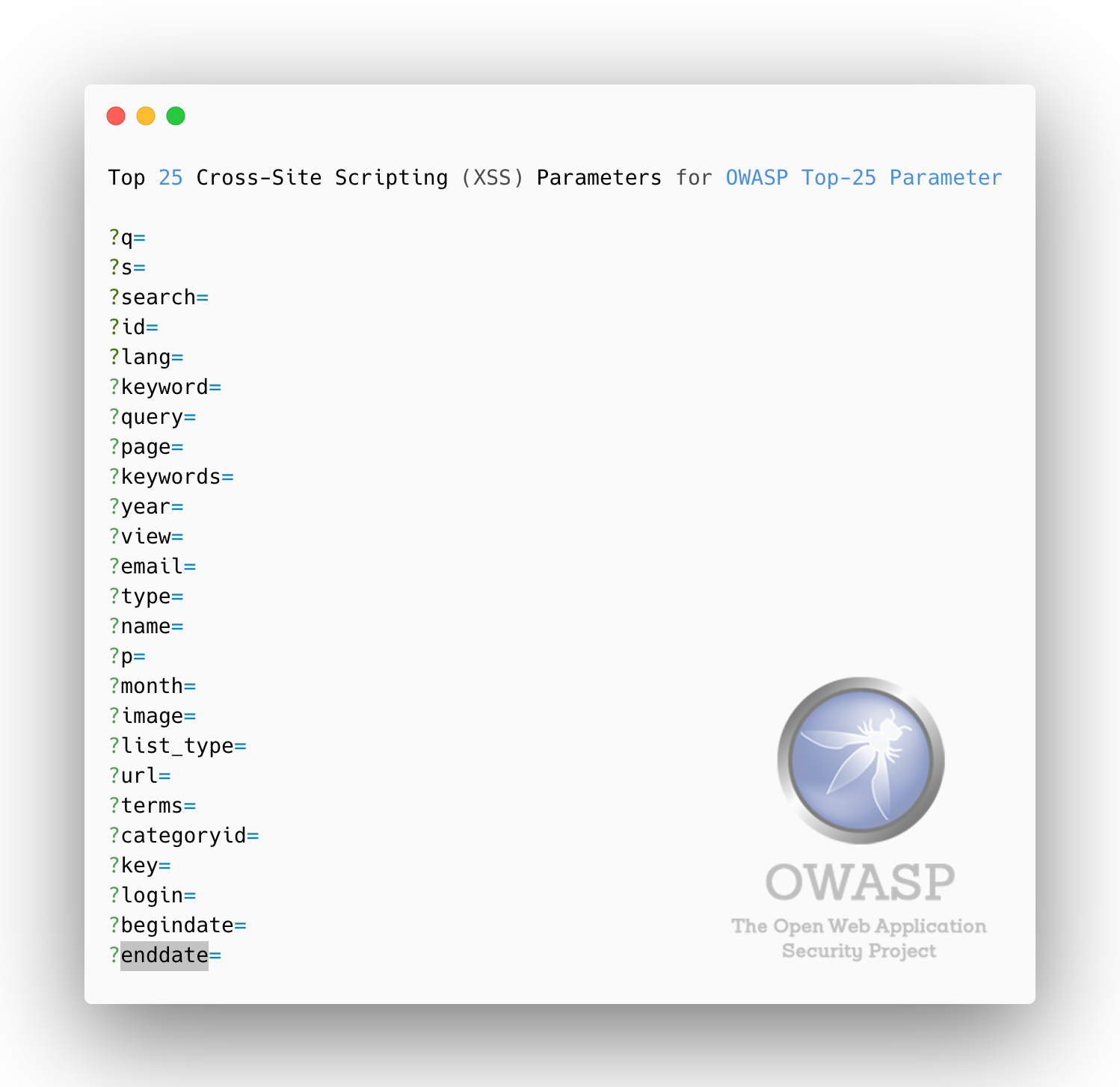
Top 25 Cross-Site Scripting (XSS) Parameters
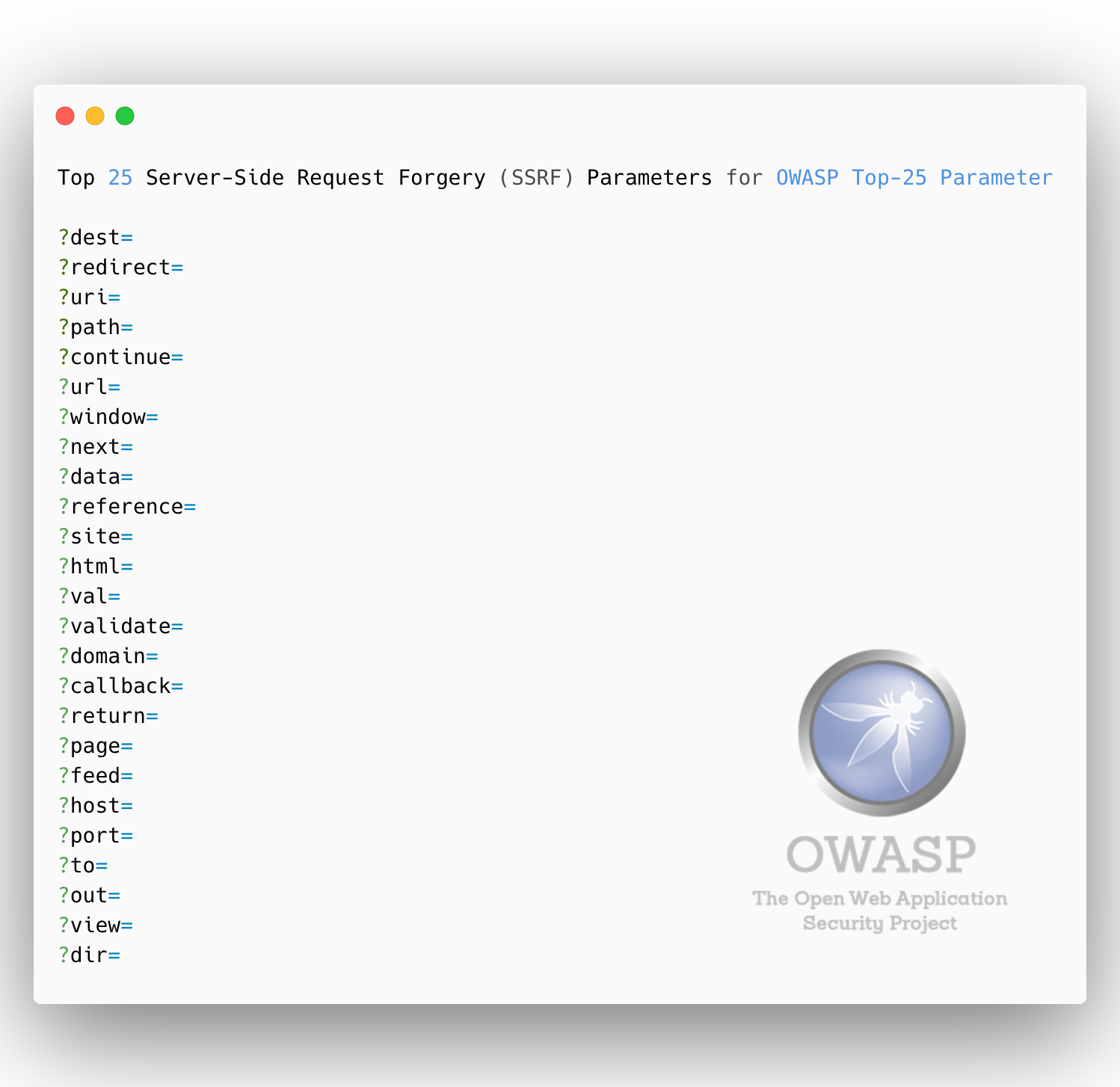
Top 25 Server-Side Request Forgery (SSRF) Parameters
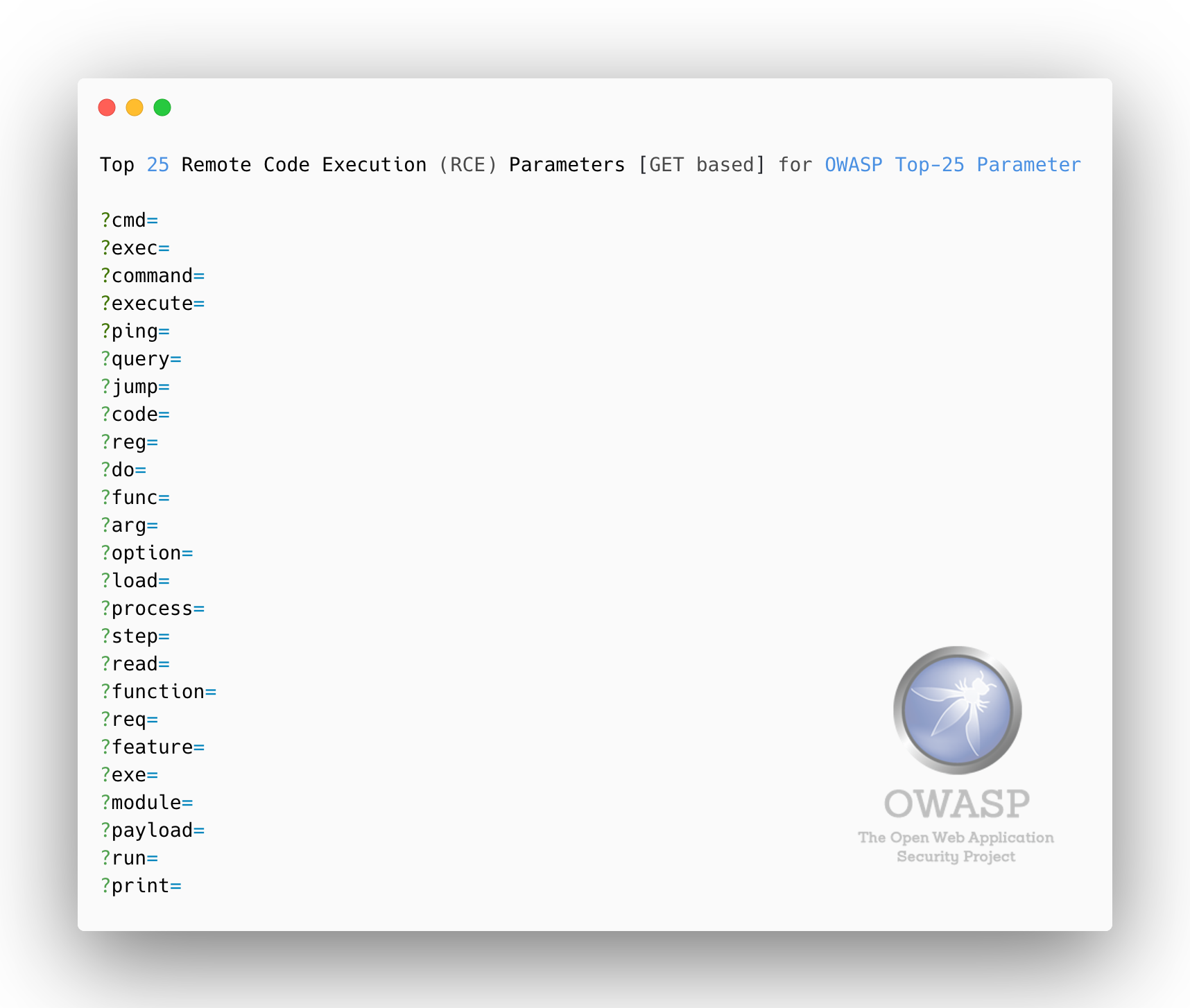
Top 25 Local File Inclusion (LFI) Parameters
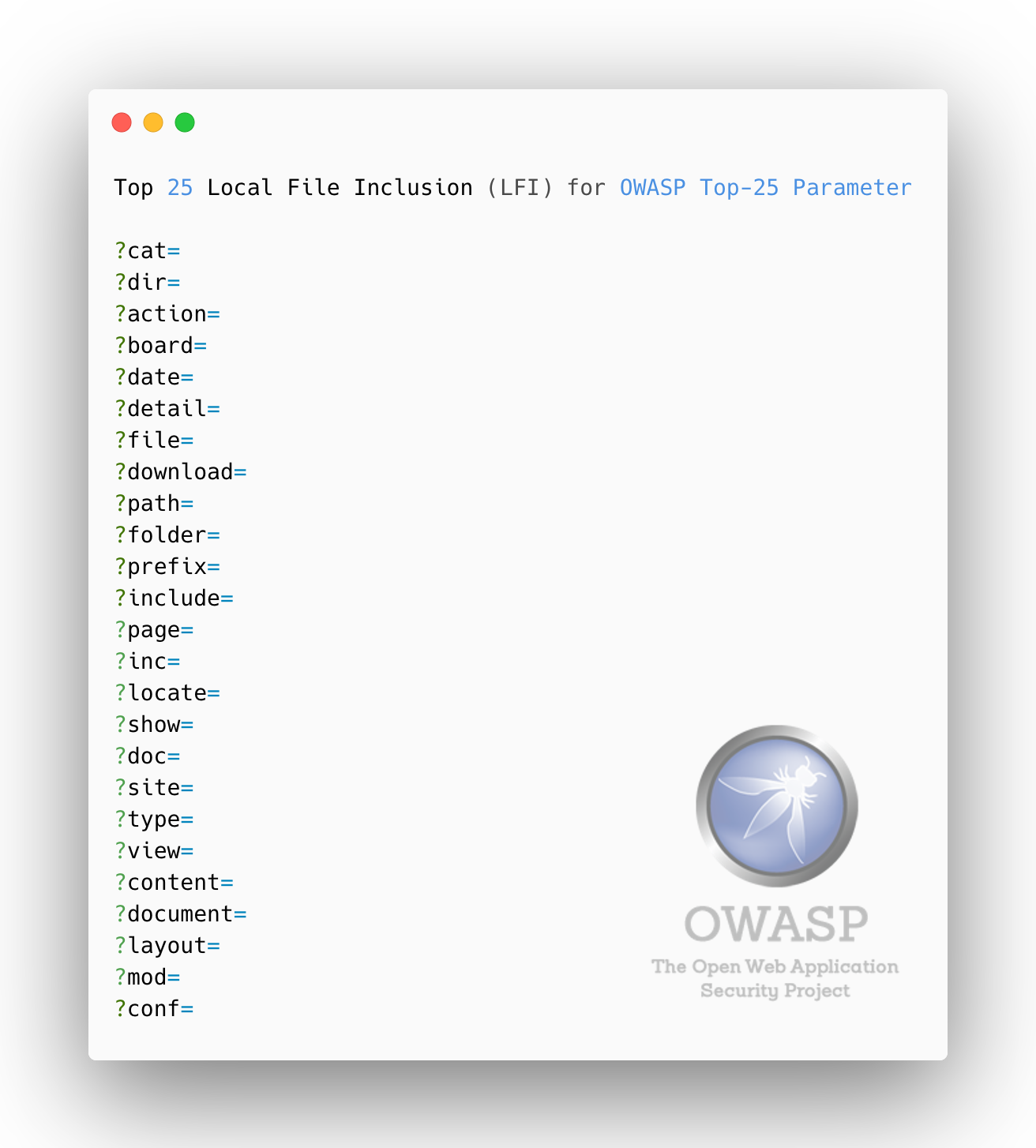
Top 25 SQL Injection Parameters
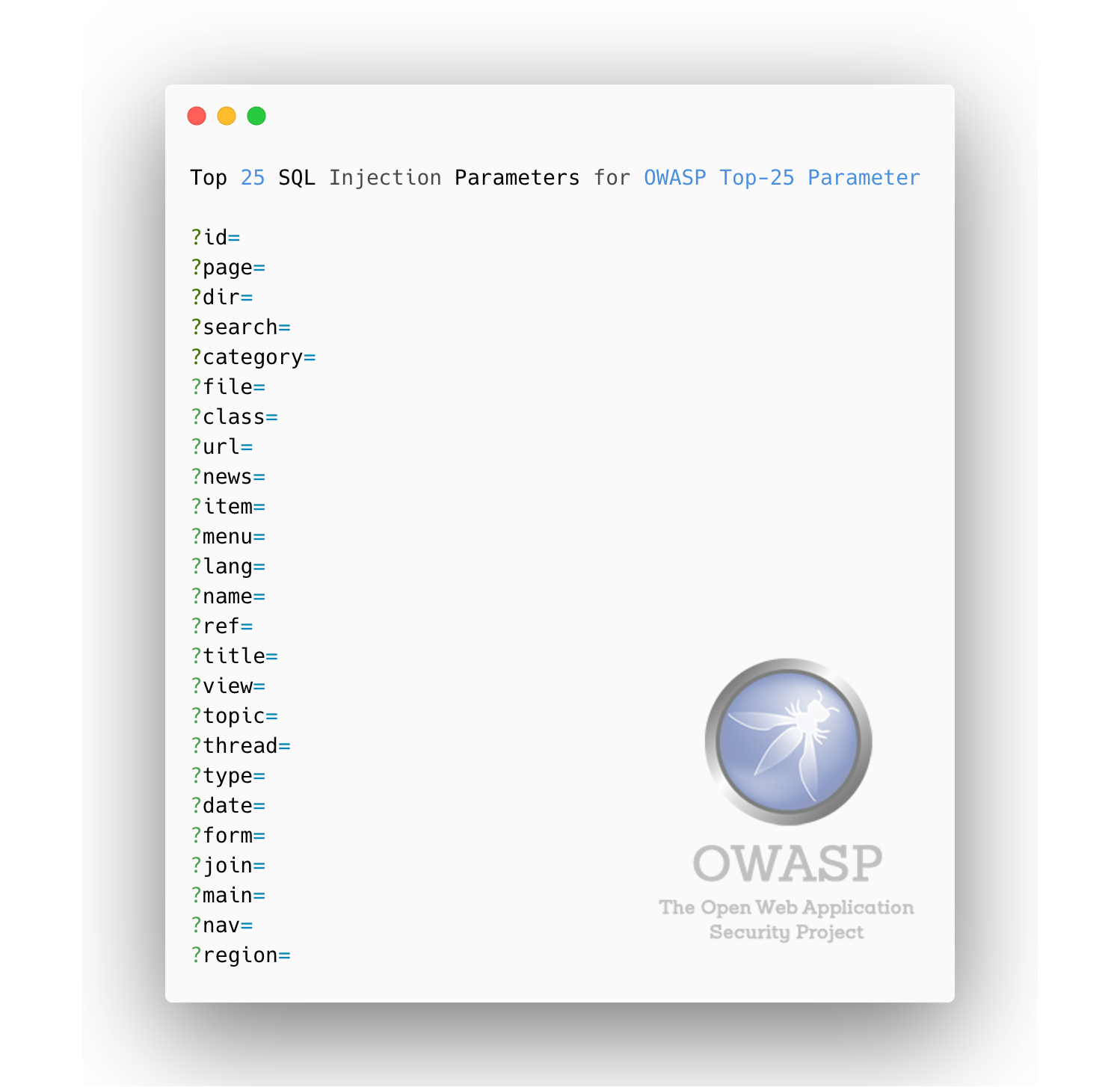
Top 25 Remote Code Execution (RCE) Parameters [GET based]
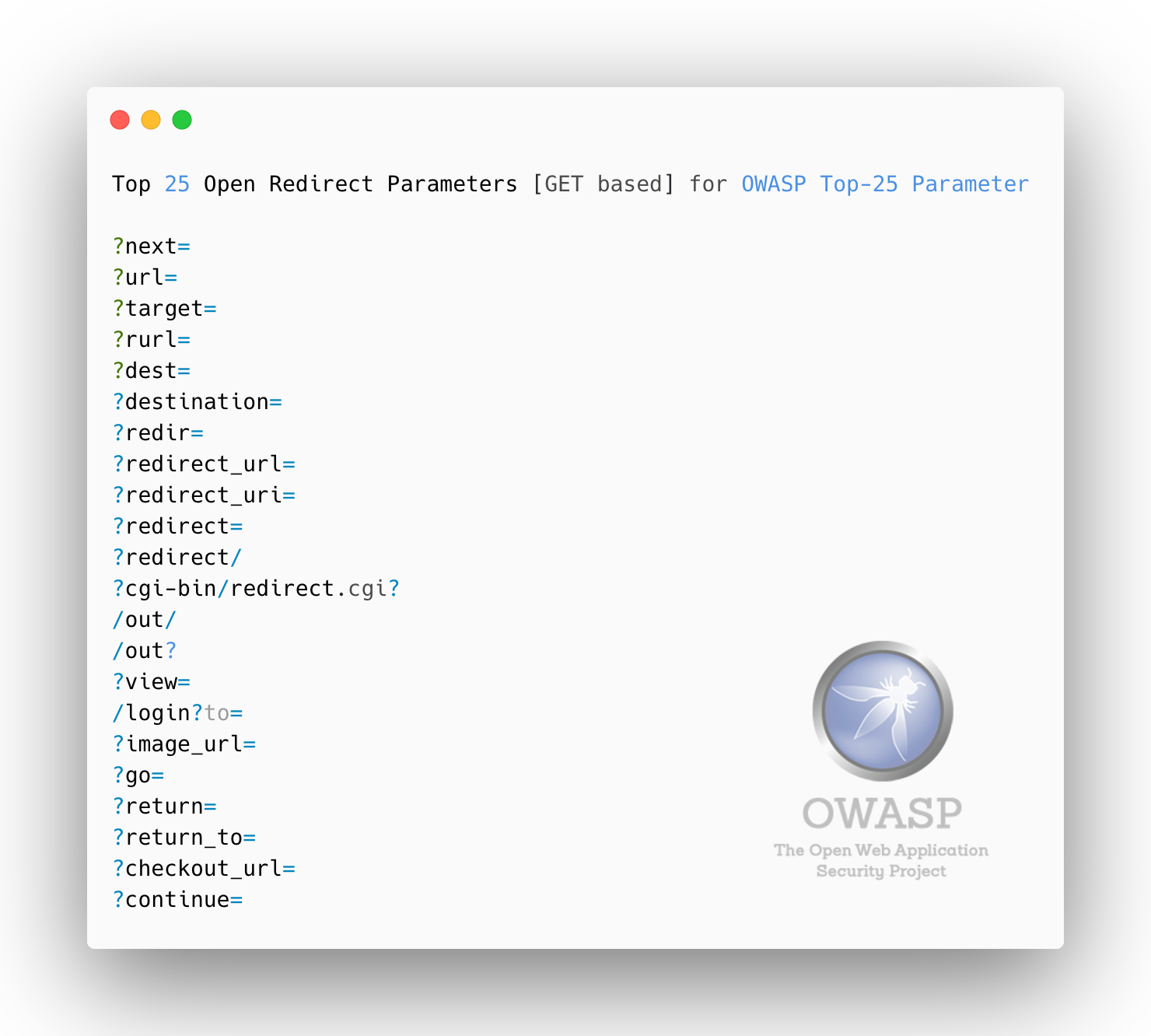
Top 25 Open Redirect Parameters [GET based]