ASVS
 ASVS copied to clipboard
ASVS copied to clipboard
1.11.1 and 1.1.5 seem to overlap
"components"
Agree, need to think about this more...
V1.1 Secure Software Development Lifecycle
Josh edit: Adding history
| # | Description | L1 | L2 | L3 | CWE |
|---|---|---|---|---|---|
| 1.1.5 | Verify definition and security analysis of the application's high-level architecture and all connected remote services. (C1) | ✓ | ✓ | 1059 | |
| 1.1.6 | Verify that a high-level architecture for the application and all connected remote services has been defined and security has been addressed in that architecture. | ✓ | ✓ | tbd | |
| 1.3 | A high-level architecture for the application and all connected remote services has been defined and security has been addressed in that architecture. | ✓ | ✓ | 1.0 |
V1.11 Business Logic Architecture
| # | Description | L1 | L2 | L3 | CWE |
|---|---|---|---|---|---|
| 1.11.1 | Verify the definition and documentation of all application components in terms of the business or security functions they provide. | ✓ | ✓ | 1059 | |
| 1.15.1 | All components are defined in terms of the business functions, and/or security functions, they provide. | ✓ | tbd | ||
| 1.5 | All app components are defined in terms of the business functions and/or security functions they provide. | ✓ | 1.0 |
This is what 3.0.1 looked like:
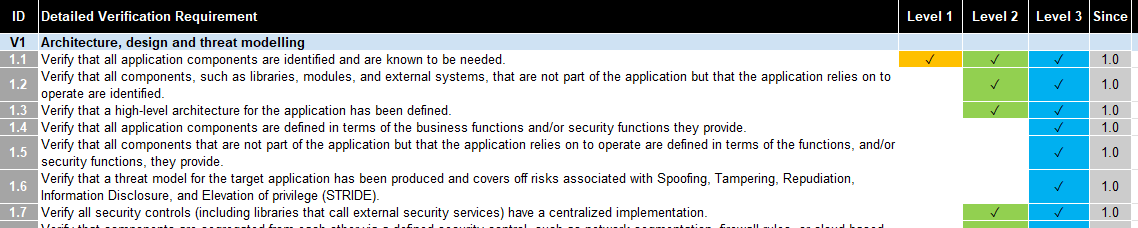
I am struggling a little to see the origin and neither of these two requirements are super clear or actionable.
This is what 3.0.1 looked like:
I am struggling a little to see the origin and neither of these two requirements are super clear or actionable.
I share your concern, Josh.
Ok this would be my attempt to clarify
| # | Description | L1 | L2 | L3 | CWE |
|---|---|---|---|---|---|
| 1.1.5 | [MODIFIED] Verify that a high-level application architecture document exists which also includes remote services upon which the application relies and how interactions with them are secured. (C1) | ✓ | ✓ | 1059 | |
| 1.1.5 | Verify definition and security analysis of the application's high-level architecture and all connected remote services. (C1) | ✓ | ✓ | 1059 | |
| 1.1.6 | Verify that a high-level architecture for the application and all connected remote services has been defined and security has been addressed in that architecture. | ✓ | ✓ | tbd | |
| 1.3 | A high-level architecture for the application and all connected remote services has been defined and security has been addressed in that architecture. | ✓ | ✓ | 1.0 |
| # | Description | L1 | L2 | L3 | CWE |
|---|---|---|---|---|---|
| 1.11.1 | [MODIFIED] Verify that the high-level architecture defines all application components in terms of the business or security functions they provide. | ✓ | ✓ | 1059 | |
| 1.11.1 | Verify the definition and documentation of all application components in terms of the business or security functions they provide. | ✓ | ✓ | 1059 | |
| 1.15.1 | All components are defined in terms of the business functions, and/or security functions, they provide. | ✓ | tbd | ||
| 1.5 | All app components are defined in terms of the business functions and/or security functions they provide. | ✓ | 1.0 |
This feels closer to the initial intention. I would be tempted to move 1.11.1 to L3 as well.
I suggest we keep 1.1.2 and drop all of the other requirements that tell me how to do threat modeling.
| 1.1.2 | Verify the use of threat modeling for every design change or sprint planning to identify threats, plan for countermeasures, facilitate appropriate risk responses, and guide security testing. | ✓ | ✓ | 1053 |
|---|
specifically I think 1.1.4, 1.1.5, 1.1.6 and similar should all go away.
| 1.1.4 | Verify documentation and justification of all the application's trust boundaries, components, and significant data flows. | ✓ | ✓ | 1059 | |
|---|---|---|---|---|---|
| 1.1.5 | Verify definition and security analysis of the application's high-level architecture and all connected remote services. (C1) | ✓ | ✓ | 1059 | |
| 1.1.6 | Verify implementation of centralized, simple (economy of design), vetted, secure, and reusable security controls to avoid duplicate, missing, ineffective, or insecure controls. (C10) | ✓ | ✓ | 637 |
1.11.1 is a documentation requirement. I think all documentation requirements should be respectfully deleted.
I think all documentation requirements should be respectfully deleted.
No. Without documented decisions, it is not possible to develop, configure, and test/verify, whether the application works as expected (as no one knows, what is the "expected")
How we going to use documentation requirements, is up for discussion in https://github.com/OWASP/ASVS/discussions/1831. But the choices there are not just to delete them, but "to have them separately in V1 or as a first chapter in related category".
Agree, we need to keep documentation requirements subject to #1831.
Note also the discussion in #1541