PyMISP
 PyMISP copied to clipboard
PyMISP copied to clipboard
Some object of my stix2 bundle doesn't appear in my MISP event
Hello,
Today I noticed that some attributes of my stix2 bundles did not appear in my events of my MISP platform. I'm using this code to upload my stix2 bundle in my MISP instance:
from pymisp import PyMISP
import io
import json
my_misp = PyMISP(misp_url, misp_auth_key, ssl=misp_is_ssl)
f = io.StringIO(json.dumps(bundle_dic))
my_misp.upload_stix(f)
Where bundle_dic is:
{
"id": "bundle--3fd2a34d-3eb4-4706-93db-30e5aedc03f1",
"objects": [
{
"id": "identity--eb8aacf7-6148-4cd6-97f9-fda0c83622d7",
"created": "2019-01-01T00:00:00.000Z",
"modified": "2020-04-20T00:00:00.000Z",
"name": "LastInfoSec",
"identity_class": "organization",
"description": "LastInfoSec offers automated solutions to collect data, refine it and turn it into useful and actionable information, quickly available to improve the protection, detection and investigation capabilities of companies and government organizations.",
"contact_information": "[email protected]",
"labels": [
"cyber security",
"threatintel",
"CTI"
],
"sectors": [
"technology"
],
"type": "identity"
},
{
"id": "intrusion-set--c93fccb1-e8e8-42cf-ae33-2ad1d183913a",
"created": "2020-05-15T11:11:25.000Z",
"modified": "2021-11-18T12:03:33.000Z",
"name": "Lazarus Group",
"created_by_ref": "identity--eb8aacf7-6148-4cd6-97f9-fda0c83622d7",
"description": "[Lazarus Group](https://attack.mitre.org/groups/G0032) is a North Korean state-sponsored cyber threat group that has been attributed to the Reconnaissance General Bureau.(Citation: US-CERT HIDDEN COBRA June 2017)(Citation: Treasury North Korean Cyber Groups September 2019) The group has been active since at least 2009 and was reportedly responsible for the November 2014 destructive wiper attack against Sony Pictures Entertainment as part of a campaign named Operation Blockbuster by Novetta. Malware used by [Lazarus Group](https://attack.mitre.org/groups/G0032) correlates to other reported campaigns, including Operation Flame, Operation 1Mission, Operation Troy, DarkSeoul, and Ten Days of Rain. (Citation: Novetta Blockbuster) North Korean group definitions are known to have significant overlap, and some security researchers report all North Korean state-sponsored cyber activity under the name [Lazarus Group](https://attack.mitre.org/groups/G0032) instead of tracking clusters or subgroups, such as [Andariel](https://attack.mitre.org/groups/G0138), [APT37](https://attack.mitre.org/groups/G0067), [APT38](https://attack.mitre.org/groups/G0082), and [Kimsuky](https://attack.mitre.org/groups/G0094). ",
"object_marking_refs": [
"marking-definition--34098fce-860f-48ae-8e50-ebd3cc5e41da"
],
"external_references": [
{
"source_name": "mitre_attack",
"url": "https://attack.mitre.org/groups/G0032/"
},
{
"source_name": "mitre_attack_enterprise",
"url": "https://attack.mitre.org/"
},
{
"source_name": "mitre_attack_mobile",
"url": "https://attack.mitre.org/"
},
{
"source_name": "mitre_attack_pre",
"url": "https://attack.mitre.org/"
}
],
"type": "intrusion-set"
},
{
"id": "indicator--3638e19f-e42e-4554-aabe-ea16355890c5",
"created": "2018-11-08T01:12:15.000Z",
"modified": "2021-11-18T12:00:29.000Z",
"name": "7c67da8edde1ecd51d599edac9594286a40d658fafa41e8497b6bfd0e530d9e1 from LastInfoSec",
"description": "The '7c67da8edde1ecd51d599edac9594286a40d658fafa41e8497b6bfd0e530d9e1' indicator is a Suspicious SHA256.\nThis SHA256 is linked to a malware attack of the WannaCry family and organised by Lazarus Group intrusion set.\nThe following vulnerability is exploited in this attack : CVE-2017-0147.\nWe advised to use this IoC in detection mode.",
"labels": [
"malicious-activity"
],
"pattern": "[file:hashes.'SHA-256' = '7c67da8edde1ecd51d599edac9594286a40d658fafa41e8497b6bfd0e530d9e1']",
"created_by_ref": "identity--eb8aacf7-6148-4cd6-97f9-fda0c83622d7",
"object_marking_refs": [
"marking-definition--34098fce-860f-48ae-8e50-ebd3cc5e41da"
],
"external_references": [
{
"source_name": "twitter",
"url": "https://t.co/wiXeXpPXMd"
},
{
"source_name": "hybrid_analysis_public_feeds",
"url": "https://hybrid-analysis.com/sample/7c67da8edde1ecd51d599edac9594286a40d658fafa41e8497b6bfd0e530d9e1/5be38a367ca3e1506d7ffac7"
},
{
"source_name": "twitter",
"url": "https://twitter.com/i/web/status/1273831630797488128"
}
],
"valid_from": "2018-11-08T01:12:15Z",
"lis_usage_mode": "detection",
"type": "indicator"
},
{
"id": "indicator--87ab933c-0c1d-452f-a0b0-3897d11a6172",
"created": "2018-11-08T01:12:13.000Z",
"modified": "2021-11-18T12:00:29.000Z",
"name": "e85e5c33d24de5b9e32f5fa974a075cd from LastInfoSec",
"description": "The 'e85e5c33d24de5b9e32f5fa974a075cd' indicator is a Malicious MD5.",
"labels": [
"malicious-activity"
],
"pattern": "[file:hashes.MD5 = 'e85e5c33d24de5b9e32f5fa974a075cd']",
"created_by_ref": "identity--eb8aacf7-6148-4cd6-97f9-fda0c83622d7",
"object_marking_refs": [
"marking-definition--34098fce-860f-48ae-8e50-ebd3cc5e41da"
],
"external_references": [
{
"source_name": "hybrid_analysis_public_feeds",
"url": "https://hybrid-analysis.com/sample/7c67da8edde1ecd51d599edac9594286a40d658fafa41e8497b6bfd0e530d9e1/5be38a367ca3e1506d7ffac7"
}
],
"valid_from": "2018-11-08T01:12:13Z",
"lis_usage_mode": "",
"type": "indicator"
},
{
"id": "malware--75ecdbf1-c2bb-4afc-a3f9-c8da4de8c661",
"created": "2020-05-15T11:04:10.000Z",
"modified": "2021-11-18T12:03:33.000Z",
"name": "WannaCry",
"labels": [
"malware"
],
"created_by_ref": "identity--eb8aacf7-6148-4cd6-97f9-fda0c83622d7",
"description": "[WannaCry](https://attack.mitre.org/software/S0366) is ransomware that was first seen in a global attack during May 2017, which affected more than 150 countries. It contains worm-like features to spread itself across a computer network using the SMBv1 exploit EternalBlue.(Citation: LogRhythm WannaCry)(Citation: US-CERT WannaCry 2017)(Citation: Washington Post WannaCry 2017)(Citation: FireEye WannaCry 2017)",
"object_marking_refs": [
"marking-definition--34098fce-860f-48ae-8e50-ebd3cc5e41da"
],
"external_references": [
{
"source_name": "mitre_attack",
"url": "https://attack.mitre.org/software/S0366/"
},
{
"source_name": "mitre_attack_enterprise",
"url": "https://attack.mitre.org/"
},
{
"source_name": "mitre_attack_mobile",
"url": "https://attack.mitre.org/"
},
{
"source_name": "mitre_attack_pre",
"url": "https://attack.mitre.org/"
}
],
"type": "malware"
},
{
"id": "indicator--389e249d-7324-4673-b084-047adf5d200a",
"created": "2018-11-08T01:12:14.000Z",
"modified": "2021-11-18T12:00:29.000Z",
"name": "8532302ddc2ae79cddc869eb61d70d47c3d09e4d from LastInfoSec",
"description": "The '8532302ddc2ae79cddc869eb61d70d47c3d09e4d' indicator is a Malicious SHA1.",
"labels": [
"malicious-activity"
],
"pattern": "[file:hashes.'SHA-1' = '8532302ddc2ae79cddc869eb61d70d47c3d09e4d']",
"created_by_ref": "identity--eb8aacf7-6148-4cd6-97f9-fda0c83622d7",
"object_marking_refs": [
"marking-definition--34098fce-860f-48ae-8e50-ebd3cc5e41da"
],
"external_references": [
{
"source_name": "hybrid_analysis_public_feeds",
"url": "https://hybrid-analysis.com/sample/7c67da8edde1ecd51d599edac9594286a40d658fafa41e8497b6bfd0e530d9e1/5be38a367ca3e1506d7ffac7"
}
],
"valid_from": "2018-11-08T01:12:14Z",
"lis_usage_mode": "",
"type": "indicator"
},
{
"id": "vulnerability--51541fe6-0307-454c-9d72-3455087c74d9",
"created": "2018-10-17T10:43:36.000Z",
"modified": "2021-11-18T12:03:33.000Z",
"name": "CVE-2017-0147",
"created_by_ref": "identity--eb8aacf7-6148-4cd6-97f9-fda0c83622d7",
"description": "The SMBv1 server in Microsoft Windows Vista SP2; Windows Server 2008 SP2 and R2 SP1; Windows 7 SP1; Windows 8.1; Windows Server 2012 Gold and R2; Windows RT 8.1; and Windows 10 Gold, 1511, and 1607; and Windows Server 2016 allows remote attackers to obtain sensitive information from process memory via a crafted packets, aka Windows SMB Information Disclosure Vulnerability.",
"object_marking_refs": [
"marking-definition--34098fce-860f-48ae-8e50-ebd3cc5e41da"
],
"external_references": [
{
"source_name": "twitter",
"url": "https://unit42.paloaltonetworks.com/network-attack-trends-winter-2020/"
},
{
"source_name": "twitter",
"url": "https://unit42.paloaltonetworks.com/network-attack-trends-winter-2020/?utm_source=bambu&medium=social&campaign=advocacy&blaid=1410056"
},
{
"source_name": "twitter",
"url": "https://unit42.paloaltonetworks.com/network-attack-trends-winter-2020/?utm_source=bambu&medium=social&campaign=advocacy&blaid=1410763"
},
{
"source_name": "twitter",
"url": "https://unit42.paloaltonetworks.com/network-attack-trends-winter-2020/?utm_source=bambu&medium=social&campaign=advocacy&blaid=1410166"
},
{
"source_name": "twitter",
"url": "https://unit42.paloaltonetworks.com/network-attack-trends-winter-2020/?utm_source=bambu&medium=social&campaign=advocacy&blaid=1411558"
},
{
"source_name": "twitter",
"url": "https://unit42.paloaltonetworks.com/network-attack-trends-winter-2020/?utm_source=bambu&medium=social&campaign=advocacy&blaid=1419413"
},
{
"source_name": "twitter",
"url": "https://unit42.paloaltonetworks.com/network-attack-trends-winter-2020/?utm_source=bambu&medium=social&campaign=advocacy&blaid=1437482"
},
{
"source_name": "twitter",
"url": "https://unit42.paloaltonetworks.com/network-attack-trends-winter-2020/?utm_source=bambu&medium=social&campaign=advocacy&blaid=1427026"
},
{
"source_name": "twitter",
"url": "http://asec.ahnlab.com/1067"
},
{
"source_name": "lastinfosecfileplatformanalysis",
"url": "https://asec.ahnlab.com/1067"
},
{
"source_name": "twitter",
"url": "https://har-sia.info/CVE-2017-0147.html"
},
{
"source_name": "nsfocus",
"url": "http://update.nsfocus.com/update/listNewipsDetail/v/rule5.6.9"
},
{
"source_name": "nsfocus",
"url": "http://update.nsfocus.com/update/listNewipsDetail/v/rule5.6.10"
},
{
"source_name": "twitter",
"url": "https://www.infosecmatter.com/metasploit-auxiliary-modules-detailed-spreadsheet/"
},
{
"source_name": "twitter",
"url": "https://owasp.org/www-project-vulnerability-management-guide/OWASP-Vuln-Mgm-Guide-Jul23-2020.pdf"
},
{
"source_name": "twitter",
"url": "https://technet.microsoft.com/library/security/MS17-010/"
},
{
"source_name": "twitter",
"url": "https://blog.talosintelligence.com/2021/06/necro-python-bot-adds-new-tricks.html"
},
{
"source_name": "twitter",
"url": "https://www.zdnet.com/article/necro-python-bot-revamped-with-new-vmware-smb-exploits/#ftag=RSSbaffb68"
},
{
"source_name": "twitter",
"url": "https://www.zdnet.com/google-amp/article/necro-python-bot-revamped-with-new-vmware-smb-exploits/"
},
{
"source_name": "twitter",
"url": "https://www.zdnet.com/article/necro-python-bot-revamped-with-new-vmware-smb-exploits/?ftag=TRE21e7bbc&bhid=24290312138359866353453975212583&mid=13390049&cid=716445877&eh=09dd3f90fd919a32d6f1c699e692837564325e0d61bd1f834aba74d15a3f38dd"
},
{
"source_name": "twitter",
"url": "https://www.bleepingcomputer.com/news/security/freakout-malware-worms-its-way-into-vulnerable-vmware-servers/"
},
{
"source_name": "twitter",
"url": "https://metacurity.substack.com/p/us-elevates-ransomware-attacks-to"
},
{
"source_name": "twitter",
"url": "https://www.bleepingcomputer.com/news/security/freakout-malware-worms-its-way-into-vulnerable-vmware-servers/amp/?__twitter_impression=true"
},
{
"source_name": "twitter",
"url": "https://securityaffairs.co/wordpress/118584/malware/necro-python-bot.html"
},
{
"source_name": "twitter",
"url": "https://hubs.li/H0PG13J0"
},
{
"source_name": "twitter",
"url": "https://www.redpacketsecurity.com/necro-python-bot-now-enhanced-with-new-vmware-server-exploits/"
},
{
"source_name": "twitter",
"url": "https://hubs.li/H0PG15f0"
},
{
"source_name": "twitter",
"url": "https://www.bleepingcomputer.com/news/security/freakout-malware-worms-its-way-into-vulnerable-vmware-servers/#.YLzmg6B9QiM.twitter"
},
{
"source_name": "nsfocus",
"url": "http://update.nsfocus.com/update/listRsasDetail/v/vulsys"
},
{
"source_name": "anquanke",
"url": "https://go.microsoft.com/fwlink/?linkid=843149"
},
{
"source_name": "twitter",
"url": "https://www.cronup.com/top-malware-series-trickbot/"
},
{
"source_name": "nsfocus",
"url": "http://update.nsfocus.com/update/listNewidsDetail/v/rule5.6.9"
},
{
"source_name": "nsfocus",
"url": "http://update.nsfocus.com/update/listNewidsDetail/v/rule5.6.10"
},
{
"source_name": "twitter",
"url": "https://docs.google.com/spreadsheets/d/1lkNJ0uQwbeC1ZTRrxdtuPLCIl7mlUreoKfSIgajnSyY/htmlview#gid=2129022708"
},
{
"source_name": "twitter",
"url": "https://www.kumaratuljaiswal.in/2021/09/introduction-to-metasploit.html"
},
{
"source_name": "twitter",
"url": "https://cvedetails.com/cve/CVE-2017-0147/"
},
{
"source_name": "github",
"url": "https://staging.nsfocusglobal.com/wp-content/uploads/2018/10/NuggetPhantom-Analysis-Report-V4.1.pdf"
},
{
"source_name": "lastinfosecfileplatformanalysis",
"url": "http://kumaratuljaiswal.in/"
},
{
"source_name": "twitter",
"url": "https://twitter.com/i/web/status/1051649227611353090"
},
{
"source_name": "google_0day_cve",
"url": "https://docs.google.com/spreadsheets/d/1lkNJ0uQwbeC1ZTRrxdtuPLCIl7mlUreoKfSIgajnSyY/#gid=1123292625"
},
{
"source_name": "hybrid_analysis_public_feeds",
"url": "https://hybrid-analysis.com/sample/1c32da2f1cc41762b53989b96c91627baa56fda46a4db6e84e0ad3113c9d67c4/606712b4858c874b37098e40"
},
{
"source_name": "capev2.1-9",
"url": "http://147.32.83.230:8000/api/tasks/view/6646"
},
{
"source_name": "nsfocus",
"url": "http://blog.nsfocus.net/feed/"
},
{
"source_name": "talos",
"url": "http://feeds.feedburner.com/feedburner/Talos"
},
{
"source_name": "cert europa cti",
"url": "https://media.cert.europa.eu/rss?type=category&id=ThreatsCybercrime&language=all&duplicates=false"
},
{
"source_name": "anquanke",
"url": "https://api.anquanke.com/data/v1/rss"
},
{
"source_name": "github",
"url": "https://github.com/cybermonitor/apt_cybercriminal_campagin_collections/commit/d812bd0fd38f8f0f03b26c0b87fd2343e109d46e"
},
{
"source_name": "cape",
"url": "https://cape.contextis.com/api/tasks/view/52599"
}
],
"type": "vulnerability"
},
{
"id": "relationship--e7330f6f-009f-4858-b15d-bee116fad9a1",
"created": "2021-11-18T12:00:28.000Z",
"modified": "2021-11-18T12:00:28.000Z",
"type": "relationship",
"source_ref": "indicator--3638e19f-e42e-4554-aabe-ea16355890c5",
"relationship_type": "indicates",
"target_ref": "malware--75ecdbf1-c2bb-4afc-a3f9-c8da4de8c661"
},
{
"id": "relationship--a8893db3-757e-4329-8962-bd49b216f1f3",
"created": "2021-11-18T12:00:28.000Z",
"modified": "2021-11-18T12:00:28.000Z",
"type": "relationship",
"source_ref": "indicator--3638e19f-e42e-4554-aabe-ea16355890c5",
"relationship_type": "indicates",
"target_ref": "intrusion-set--c93fccb1-e8e8-42cf-ae33-2ad1d183913a"
},
{
"id": "relationship--d38e8679-26f8-4843-9c9a-9c1642fff95d",
"created": "2021-11-18T12:00:28.000Z",
"modified": "2021-11-18T12:00:28.000Z",
"type": "relationship",
"source_ref": "indicator--3638e19f-e42e-4554-aabe-ea16355890c5",
"relationship_type": "related-to",
"target_ref": "vulnerability--51541fe6-0307-454c-9d72-3455087c74d9"
},
{
"id": "relationship--24ebc57f-6f81-4984-83e4-7785d2a0bac1",
"created": "2021-11-18T12:00:28.000Z",
"modified": "2021-11-18T12:00:28.000Z",
"type": "relationship",
"source_ref": "indicator--389e249d-7324-4673-b084-047adf5d200a",
"relationship_type": "derived-from",
"target_ref": "indicator--3638e19f-e42e-4554-aabe-ea16355890c5"
},
{
"id": "relationship--d1dce49f-c596-49c2-9eed-ba068623f0f9",
"created": "2021-11-18T12:00:28.000Z",
"modified": "2021-11-18T12:00:28.000Z",
"type": "relationship",
"source_ref": "indicator--87ab933c-0c1d-452f-a0b0-3897d11a6172",
"relationship_type": "derived-from",
"target_ref": "indicator--3638e19f-e42e-4554-aabe-ea16355890c5"
},
{
"id": "marking-definition--34098fce-860f-48ae-8e50-ebd3cc5e41da",
"created": "2017-01-20T00:00:00.000Z",
"definition_type": "tlp",
"definition": {
"tlp": "green"
},
"type": "marking-definition"
},
{
"id": "report--3fd2a34d-3eb4-4706-93db-30e5aedc03f1",
"created_by_ref": "identity--eb8aacf7-6148-4cd6-97f9-fda0c83622d7",
"labels": [
"vulnerability",
"intrusion-set",
"indicator",
"threat-report",
"malware"
],
"object_refs": [
"malware--75ecdbf1-c2bb-4afc-a3f9-c8da4de8c661",
"indicator--389e249d-7324-4673-b084-047adf5d200a",
"relationship--e7330f6f-009f-4858-b15d-bee116fad9a1",
"marking-definition--34098fce-860f-48ae-8e50-ebd3cc5e41da",
"indicator--3638e19f-e42e-4554-aabe-ea16355890c5",
"indicator--87ab933c-0c1d-452f-a0b0-3897d11a6172",
"identity--eb8aacf7-6148-4cd6-97f9-fda0c83622d7",
"intrusion-set--c93fccb1-e8e8-42cf-ae33-2ad1d183913a",
"vulnerability--51541fe6-0307-454c-9d72-3455087c74d9",
"relationship--d1dce49f-c596-49c2-9eed-ba068623f0f9",
"relationship--d38e8679-26f8-4843-9c9a-9c1642fff95d",
"relationship--a8893db3-757e-4329-8962-bd49b216f1f3",
"relationship--24ebc57f-6f81-4984-83e4-7785d2a0bac1"
],
"description": "The threat report contains 3 indicators with a high confidence average. The categories of the threat are trojan, exploit, malware, ransom. The software used belongs to WannaCry family. The CVE exploited in this attack: CVE-2017-0147. ",
"external_references": [
{
"source_name": "twitter",
"url": "https://t.co/wiXeXpPXMd"
},
{
"source_name": "hybrid_analysis_public_feeds",
"url": "https://hybrid-analysis.com/sample/7c67da8edde1ecd51d599edac9594286a40d658fafa41e8497b6bfd0e530d9e1/5be38a367ca3e1506d7ffac7"
},
{
"source_name": "twitter",
"url": "https://twitter.com/i/web/status/1273831630797488128"
}
],
"name": "Indicator(s) of 'WannaCry' Malware Report from https://t.co/wiXeXpPXMd",
"published": "2021-11-18T12:00:28Z",
"type": "report",
"created": "2021-11-18T12:03:18.772Z",
"modified": "2021-11-18T12:03:18.772Z"
}
],
"type": "bundle",
"spec_version": "2.0"
}
In this case, the vulnerability doesn't appear:
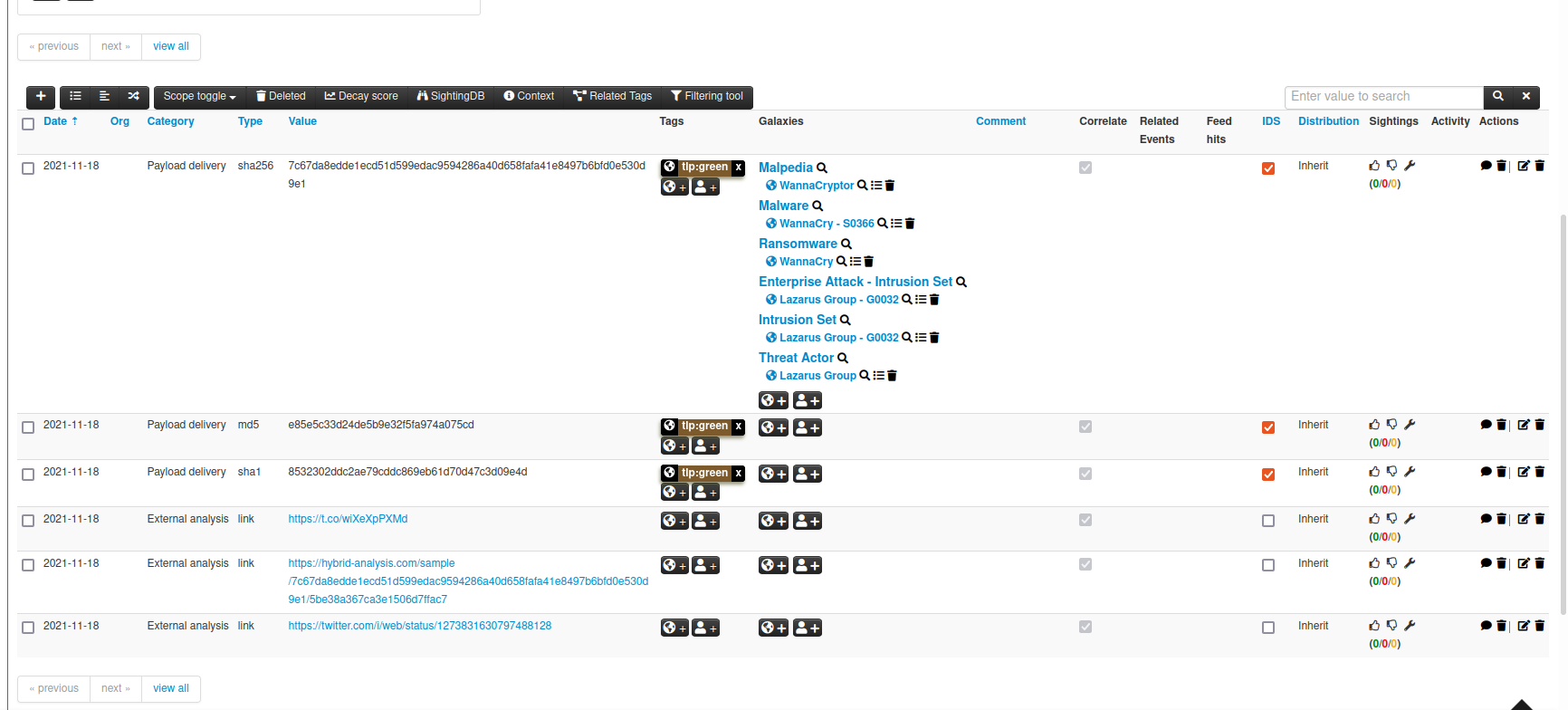 Even when I download the MISP event as "MISP JSON (metadata + all attributes)" I don't see it.
Even when I download the MISP event as "MISP JSON (metadata + all attributes)" I don't see it.
In some others cases, I noticed that some attack-pattern don't appear either. For this case, I think it's because the attack-pattern doesn't exist in the galaxy. I think the two problems are linked.
So can you tell me how my MISP Instance can accept all the objects of my Stix2 bundle to avoid losing context?
Thanks for your help,
Rémy