Provide ca.crt with Ingress
Title
Provide ca.crt with Ingress
Description
Although a TLS secret used in a Kubernetes Ingress may contain a ca.crt this is not used in the BigIP device.
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
annotations:
cert-manager.io/cluster-issuer: cluster-ca-issuer
kubernetes.io/ingress.class: f5
virtual-server.f5.com/ip: controller-default
name: argocd-f5
namespace: argocd
spec:
rules:
- host: argocd.kubernetes-dev-1.int
http:
paths:
- backend:
service:
name: argocd-server
port:
number: 80
pathType: ImplementationSpecific
tls:
- hosts:
- argocd.kubernetes-dev-1.int
secretName: argocd-secret
> k get secret -o yaml argocd-secret | yq '.data'
{
"ca.crt": "LS0tLS1CR...",
"tls.crt": "...",
"tls.key": "..."
}
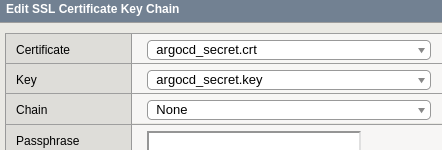
Actual Problem
In our case the CA in the cluster is a intermediate CA. Since this is not configured in the F5 clients can not verify the Ingress endpoint at the F5.
Solution Proposed
The k8s-bigip-ctlr should configure the CA for in the SSL profile according to the field ca.crt in the Ingress TLS secret.
Alternatives
The clients could themselves install the intermediate CA. However, that leads to more work and possible problems when the intermediate CA has to be exchanged.
@Timoses could you reference the profile which is already created on BIG-IP via the ingress. Example clientssl profile below.
Here is example how you reference a profile from BIG-IP
https://github.com/F5Networks/k8s-bigip-ctlr/blob/master/docs/config_examples/ingress/single-service-tls-ingress.yaml
# Follows the format "/partition/profile_name".
- secretName: /Common/clientssl
Hi @mdditt2000 .
I don't quite understand.
In the BigIP device when I have the Kubernetes partition selected I have the following 3 profiles (which were created by the f5-bigip-ctlr):
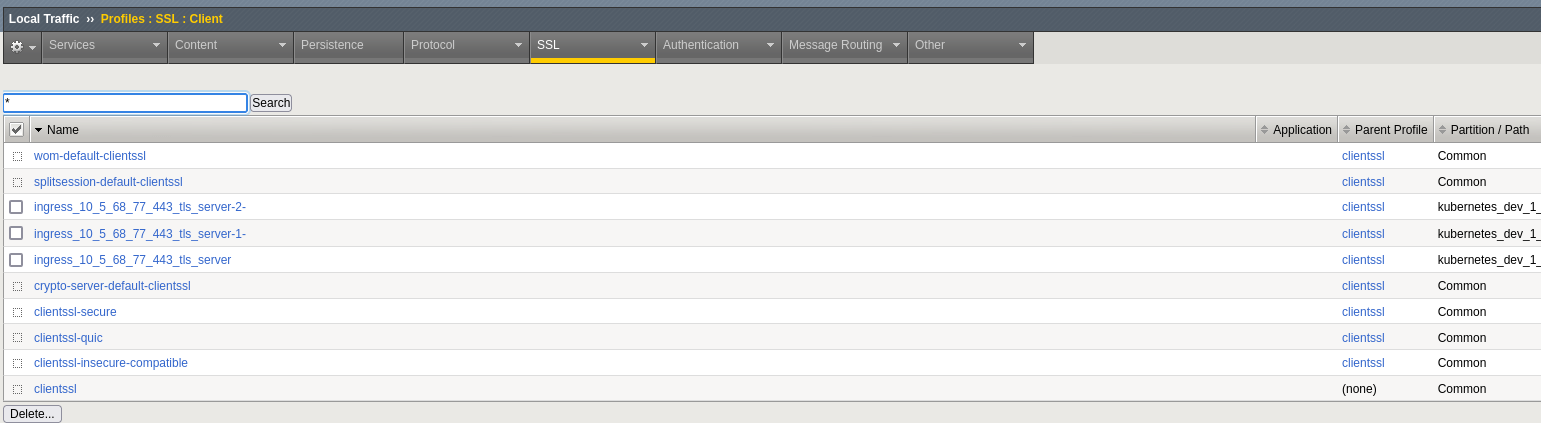
Selecting on and viewing the Cert Key Chain shows:
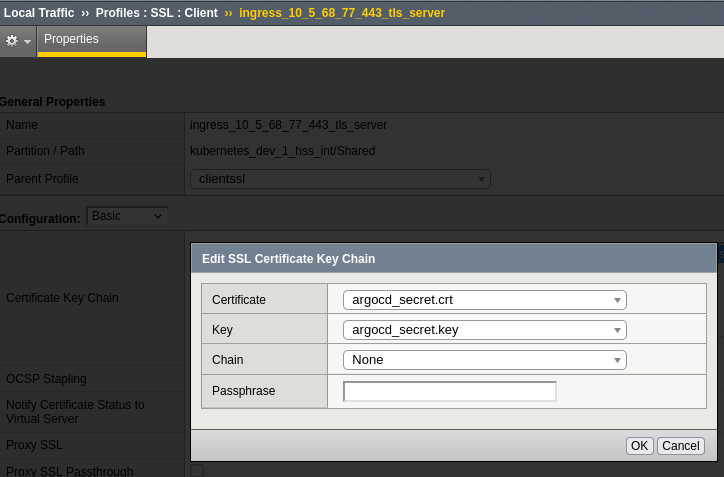
=> The ca.crt is missing.
Would you like me to use
- secretName: /Common/clientssl
in the related Ingress resource in Kubernetes? What would be the motivation for that (as that profile most probably is not related to the service and will probably lead to Cert verification error on client side)?
No update to CIS. closing this issue.