icmptunnel
 icmptunnel copied to clipboard
icmptunnel copied to clipboard
authentication
there should be some means of encrypted (one-time) authentication (per ip) so not everyone can use the icmp proxy server.
agreed
On server startup the user could specify a pre-shared key or password and we have the client send the password as the first message to the server. Everything is plain text, so it could be sniffed, but not anyone could use the server anymore just by knowing the server IP + port.
+1 for pre-shared key/password. I'm also planning to add encryption, that is, when I get some time for this.
In that case it probably makes more sense to use TLS with a client certificate. That'll provide encryption and authentication that can't be sniffed since it uses a DH handshake.
Have there been any problems with reliability? The handshake could be difficult to complete over ICMP since it's unreliable like UDP.
Also, is a session defined by a client IP?
rather than going for an overkill solution like TLS (which will be hard to implement with icmp packet size!) i'd rather go for something based on djb's tweetnacl crypto primitives, which fit in a single, small .c file. ( https://tweetnacl.cr.yp.to/ )
@Gandalf- If the client and server are accessible within the same LAN network, the connection can be assumed to be reliable. Cannot say much for connections over the internet. And yes TLS with client certificate might be too much for icmptunnel.
I hadn't heard about tweetnacl; it does look like a good option. Is there already a fork or branch working on this?
So @DhavalKapil have you have a change to add some form of authentication?
@greg5678 Not yet
@rofl0r
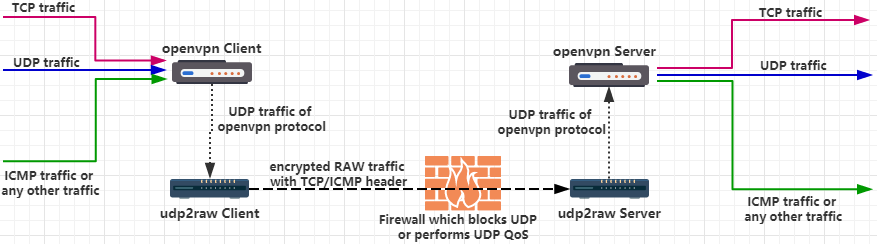
if you need a solution with authentication and encryption ,you can try my repo:
https://github.com/wangyu-/udp2raw-tunnel
https://github.com/wangyu-/udp2raw-tunnel#tunneling-any-traffic-via-raw-traffic-by-using-udp2raw-openvpn