All Diagnostic polices are not compliant when using custom profileName.
Community Note
- Please vote on this issue by adding a 👍 reaction to the original issue to help the community and maintainers prioritize this request
- Please do not leave "+1" or "me too" comments, they generate extra noise for issue followers and do not help prioritize the request
- If you are interested in working on this issue or have submitted a pull request, please leave a comment
Versions
terraform: 1.0.3
azure provider: Azure/caf-enterprise-scale/azurerm
module: 0.3.3 tags / 0.4.0 tags
Description
All custom "Deploy-Diagnostics" policy definitions apply, but fail to be compliant when you give your own profileName. Going to the resource you can see the diagnostics has been applied with your profile name, however, the assignment never shows as compliant.
The reason it is not compliant, is because of the PolicyRule. All of them have name hardcoded to "setByPolicy". Which means the first part of the rule is looking for a diagnostics called "setByPolicy", as it doesn't find it, it isn't compliant. It then deploys the diagnostic settings, but is given the custom profileName.
Example in CosmosDB.
"policyRule": {
"if": {
"field": "type",
"equals": "Microsoft.DocumentDB/databaseAccounts"
},
"then": {
"effect": "[parameters('effect')]",
"details": {
"type": "Microsoft.Insights/diagnosticSettings",
"name": "setByPolicy",
"existenceCondition": {
"allOf": [
If you take a look at a built-in policy such as the "Deploy Diagnostic Settings for Key Vault to Log Analytics workspace" /providers/Microsoft.Authorization/policyDefinitions/bef3f64c-5290-43b7-85b0-9b254eef4c47 you will see the "name" should match the profileName.
"policyRule": {
"if": {
"field": "type",
"equals": "Microsoft.KeyVault/vaults"
},
"then": {
"effect": "[parameters('effect')]",
"details": {
"type": "Microsoft.Insights/diagnosticSettings",
"name": "[parameters('profileName')]",
"existenceCondition": {
"allOf": [
Steps to Reproduce
- When deploying "Deploy-Resource-Diag" change the profileName to be different from "setByPolicy" e.g., "setbypolicy_LogAnaltyics"
- Create a resource that is using a custom policy, e.g, CosmosDb.
- Wait for the deployifnotexist to kick in.
- Check the CosmosDB diagnostics and see that there is a named diagnostics "setbypolicy_LogAnalytics"
- Check the policy in compliance, see that it states that it's not compliant.
Screenshots
Policy Deployed - Note deployed 23/Aug/2021 @ 1:47PM
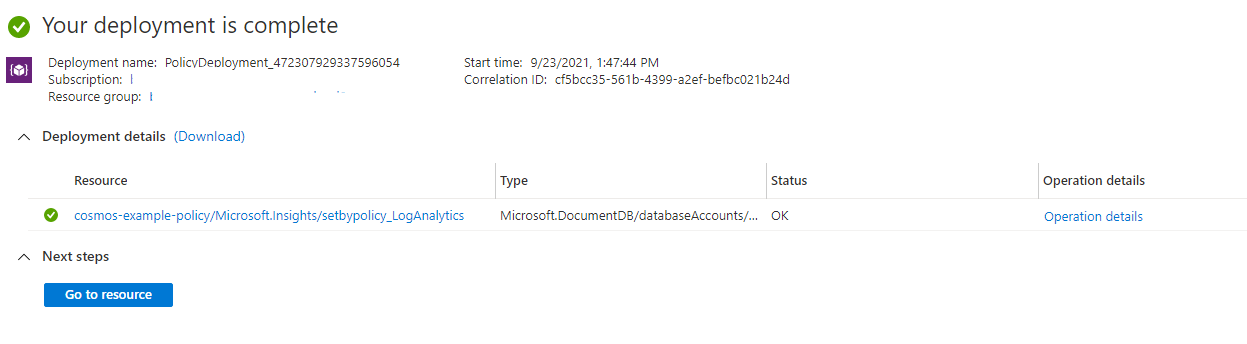
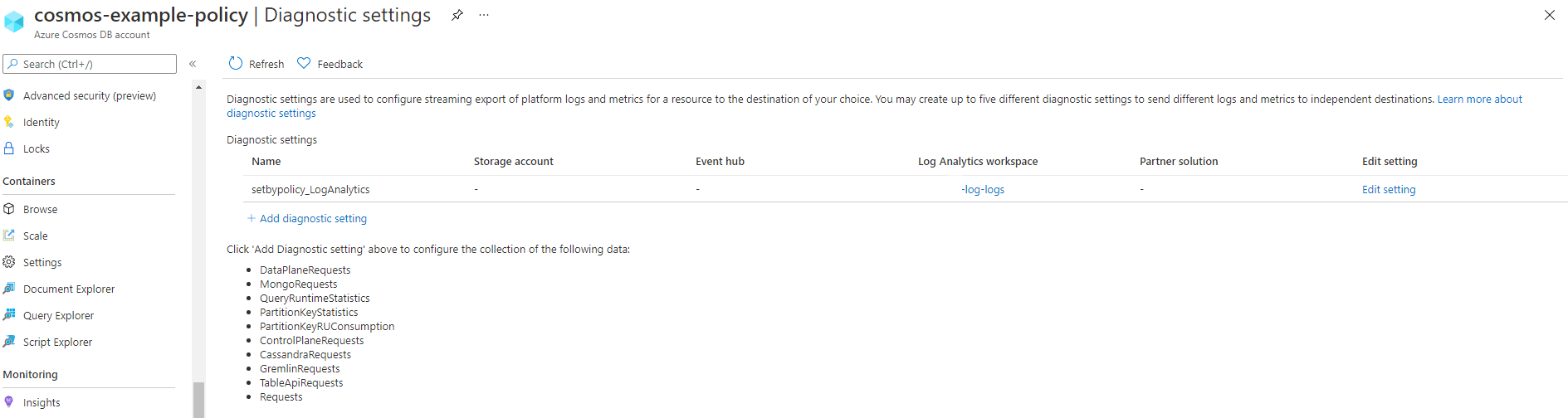
Proof of the policy diagnostic name is setbypolicy_loganalytics
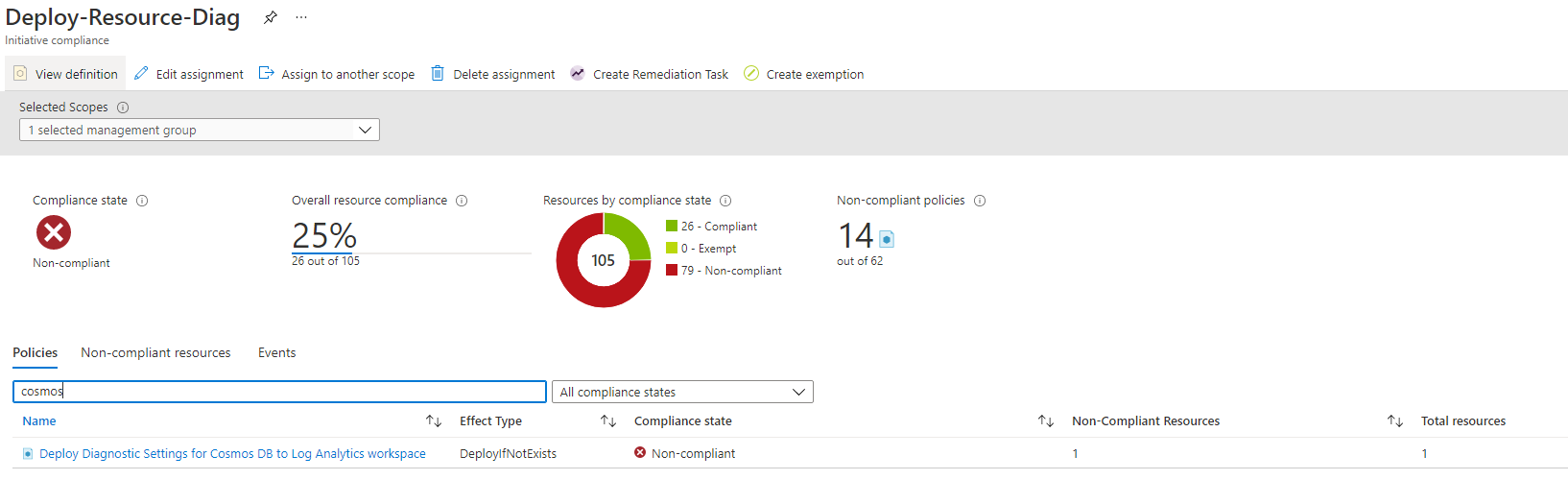
Proof still not compliant.
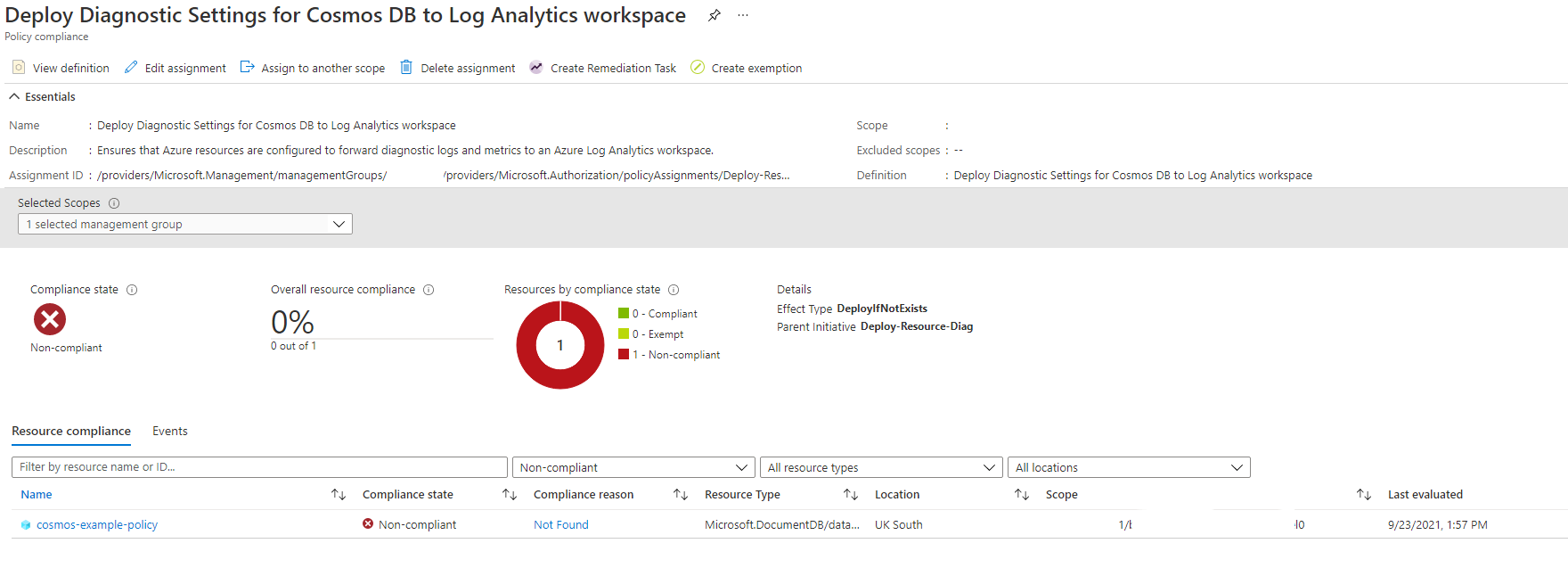
Proof it has been re-evaluated since deployment. Last evaluated at 23/Aug/2021 @1.57PM.
This looks like a great spot, thank you.
I will log this in our upstream Azure/Enterprise-Scale repository so we can look into options for applying a consistent fix across these.
Please note that the strategic intent is for these all to move to built-in policies though so that may be the preferred path if time frames are reasonable.
@krowlandson although the strategic intent is for these all to move to built-in policies, I've noticed not all of them have built-in alternatives. Does this mean you are working closely with the Microsoft internal team?
@krowlandson Kevin Rowlandson FTE although the strategic intent is for these all to move to built-in policies, I've noticed not all of them have built-in alternatives. Does this mean you are working closely with the Microsoft internal team?
Yes, this is the current process and intent.
Requires further investigation before we can set a milestone for release
Related to #860
Trigger ADO Sync 1
Trigger ADO Sync 2
Closing as this is in upstream repo and is a duplicate of #478. PR for fix is in the works here #1059