Port Scan Analytic Rule not Populating Entities list in Incident
Describe the bug When the the [Port scan detected (ASIM Network Session schema)] analytic rule triggers an incident, it does not populate the SrcIPAddr columns into the Entities list with an IP address even though its configured as part of the rule. This prevents us from creating playbooks for expected behavior related to this detection.
To Reproduce Steps to reproduce the behavior:
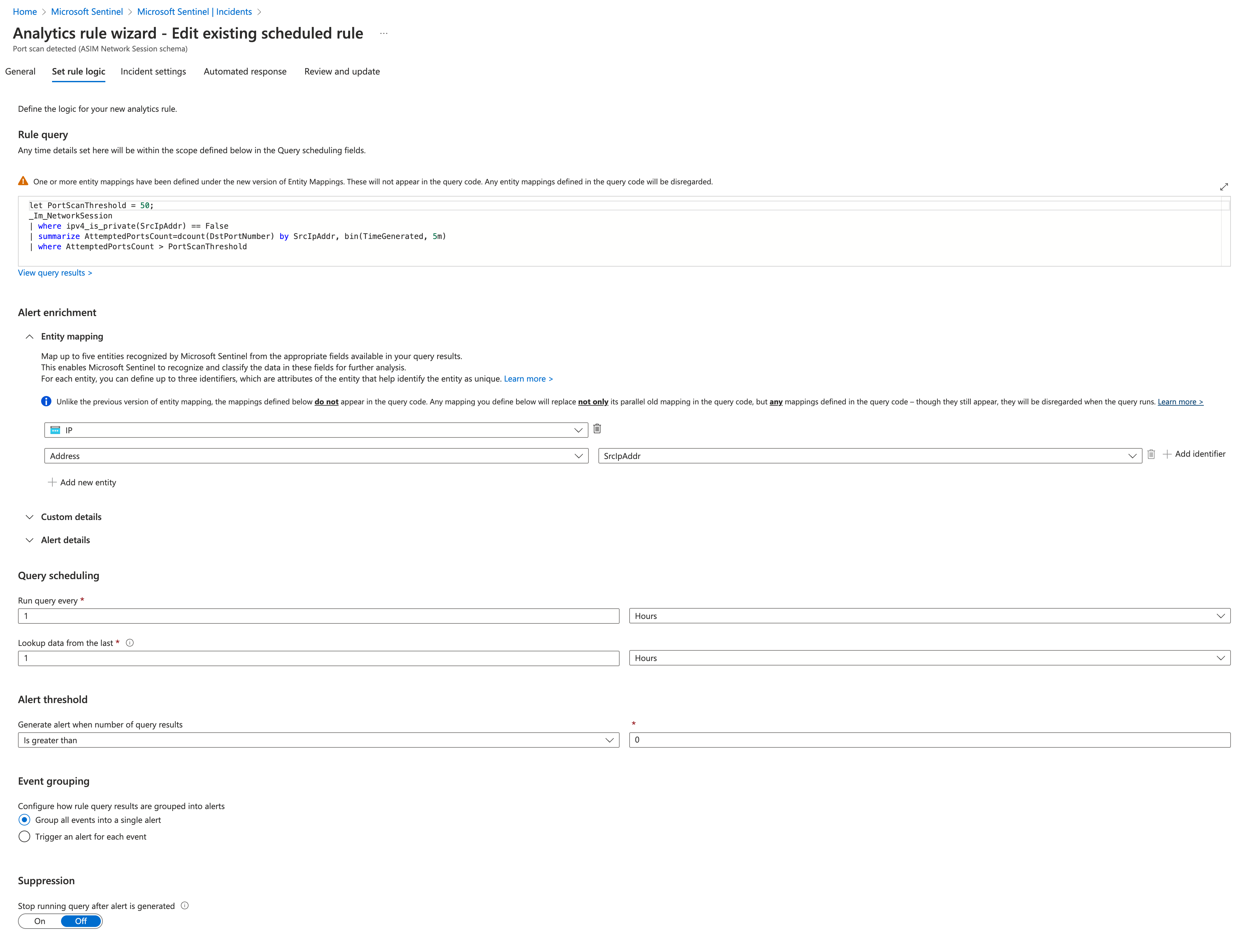
- Enable the rule
- Ensure that ScrIPAddr is mapped to "IP Address"
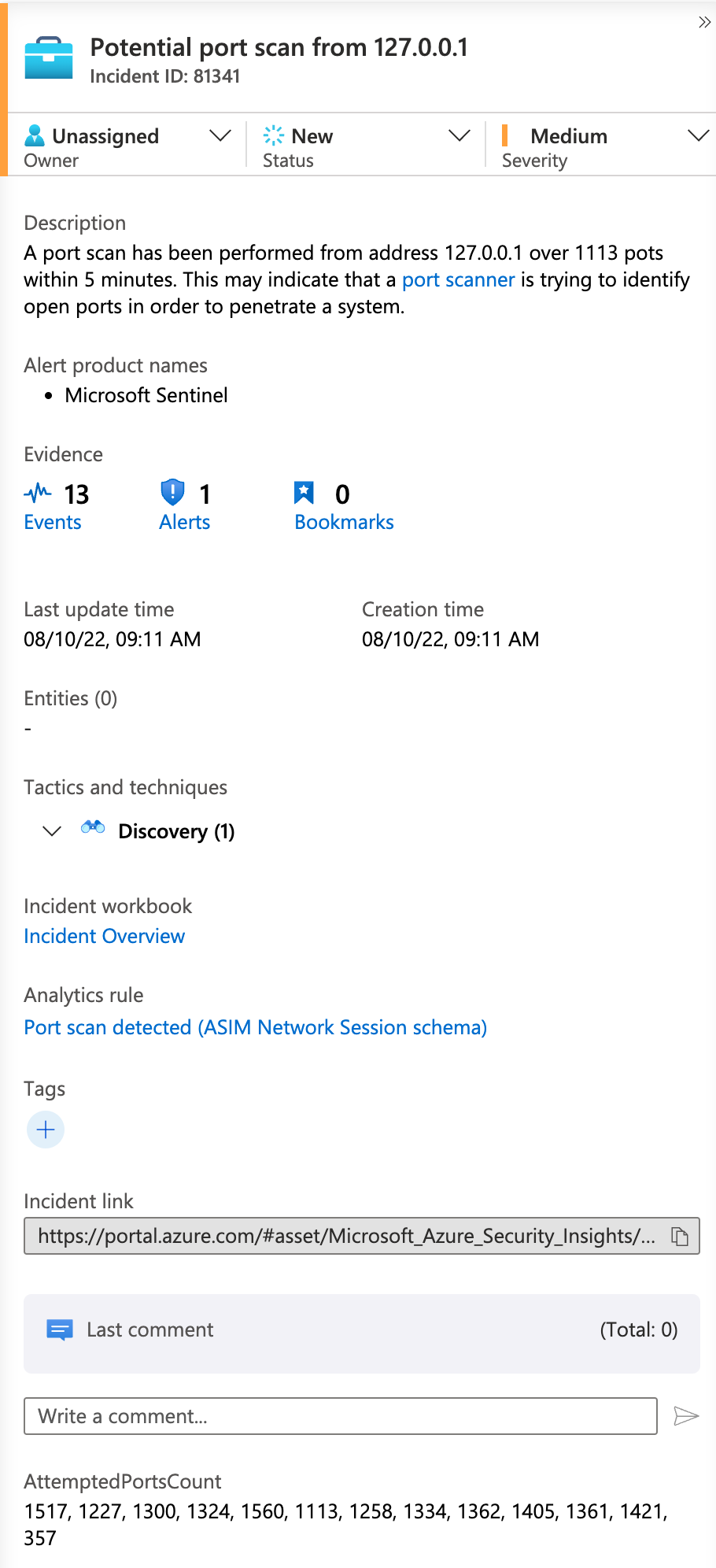
- View incident generated by rule and see that "Entities" list is empty.
- Review Events to confirm the SrcIPAddr column is populating:
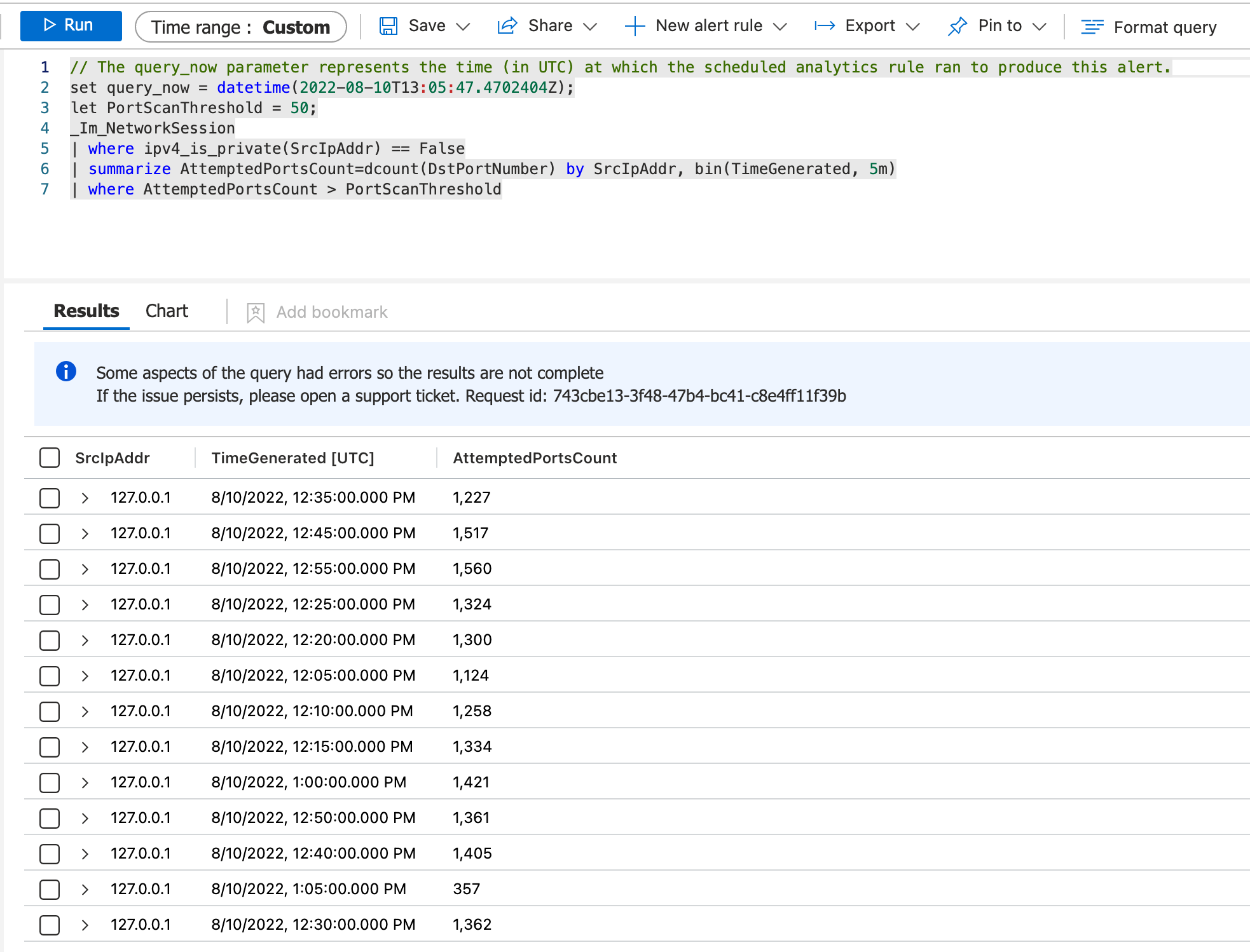
Expected behavior We should see all of the SrcIPAddr rows listed in the Entities field so that we can create playbooks to auto-close expected detections from certain IP Addresses.
Screenshots Included inline above.
Thank you for submitting an Issue to the Azure Sentinel GitHub repo! You should expect an initial response to your Issue from the team within 5 business days. Note that this response may be delayed during holiday periods. For urgent, production-affecting issues please raise a support ticket via the Azure Portal.
Any updates on this issue?
Thank you for submitting an Issue to the Azure Sentinel GitHub repo! You should expect an initial response to your Issue from the team within 5 business days. Note that this response may be delayed during holiday periods. For urgent, production-affecting issues please raise a support ticket via the Azure Portal.
Thank you for submitting an Issue to the Azure Sentinel GitHub repo! You should expect an initial response to your Issue from the team within 5 business days. Note that this response may be delayed during holiday periods. For urgent, production-affecting issues please raise a support ticket via the Azure Portal.
Hi @wingcomm, kindly open a support ticket for this.