php-proxy-app
 php-proxy-app copied to clipboard
php-proxy-app copied to clipboard
PHP-Proxy <= 5.1.0 - The decrypt key is flawed and cause the vulnerability of LFI
We discovered the PHP-Proxy str_rot_pass encrypt function is flawed. Despite the user change the default key, the remote attacker can easily decrypt the key and cause the vulnerability of Local File Inclusion.
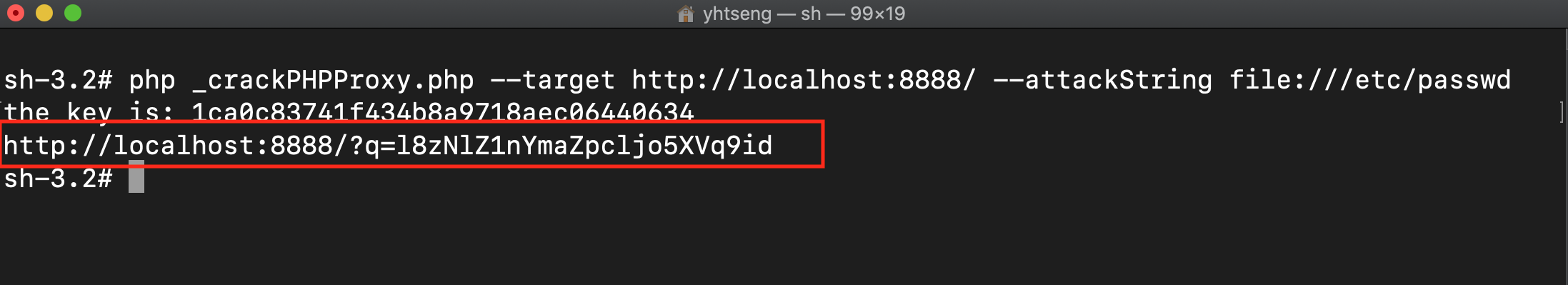
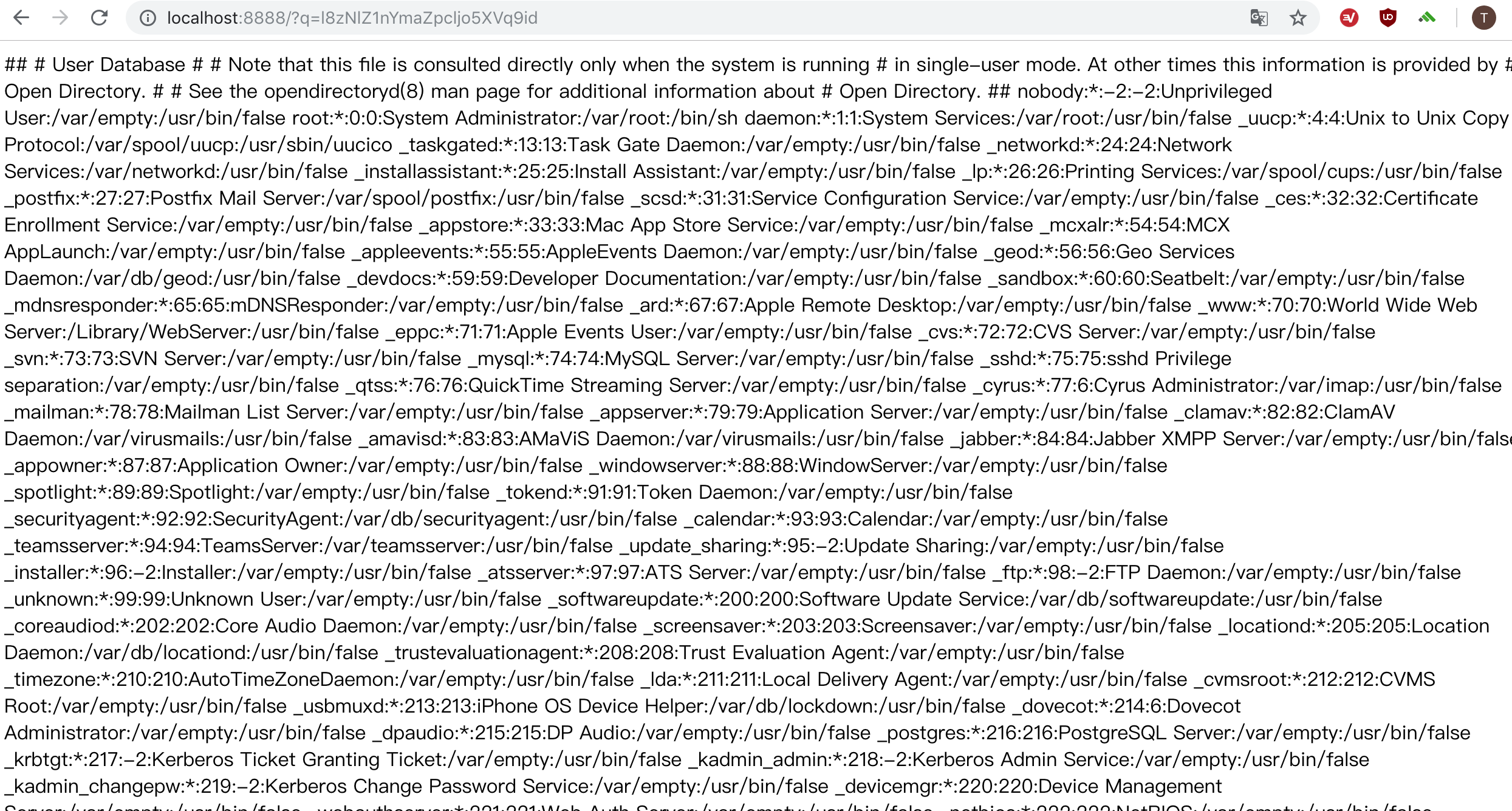
Detailed steps and sample payload: https://github.com/0xUhaw/CVE-Bins/tree/master/PHP-Proxy
We suggest that the encryption rules should be strengthened because the logic of decryption is too easy.
Is there anything that regular users can do now other than simply stop using the proxy?
Since this is the encrypt key problem, this should be fixed by the official... If it is a problem for LFI, you can disable curl file protocol.
Has this been fixed yet? Or has no comment been made?
@RubyTheRose No comment yet, but they fixed one of the other vulnerabilities (even if only a simple one).
The problem seems to be when the proxy decrypts the value from the $_GET['q']
On this file:
https://github.com/Athlon1600/php-proxy-app/blob/master/index.php
We can see this on line 68:
// decode q parameter to get the real URL
$url = url_decrypt($_GET['q']);
So lets take a look at url_decrypt() function that is on this file at line 155:
https://github.com/Athlon1600/php-proxy/blob/master/src/helpers.php
As you can see, it uses str_rop_pass() to decrypt the string:
function url_decrypt($url, $key = false){
$url = Config::get('url_mode') ? base64_url_decode($url) : rawurldecode($url);
if($key){
$url = str_rot_pass($url, $key, true);
} else if(Config::get('encryption_key')){
$url = str_rot_pass($url, Config::get('encryption_key'), true);
}
return $url;
}
A quick fix should be to validate the variable $url like this:
function url_decrypt($url, $key = false){
$url = Config::get('url_mode') ? base64_url_decode($url) : rawurldecode($url);
if($key){
$url = str_rot_pass($url, $key, true);
} else if(Config::get('encryption_key')){
$url = str_rot_pass($url, Config::get('encryption_key'), true);
}
if (!filter_var($url, FILTER_VALIDATE_URL)) return "";
if (!in_array(strtolower(parse_url($url, PHP_URL_SCHEME)), array("http","https"))) return "";
return $url;
}
So we return "" if the url is not valid or if it has a non-http/https scheme (i.e file:// or ftp://).
You may also want to use my SecurityPlugin that already prevents the LFI vulnerability:
https://github.com/Athlon1600/php-proxy-plugin-bundle/pull/2
It will increase the security of PHP-Proxy by validating many important things.
Hope this helps.
That security plugin looks pretty good, I think I might use it. Thanks.
From: Web Addicto [email protected] Sent: Tuesday, January 22, 2019 7:58 pm To: Athlon1600/php-proxy-app Cc: Benji-Collins; Comment Subject: Re: [Athlon1600/php-proxy-app] PHP-Proxy <= 5.1.0 - The decrypt key is flawed and cause the vulnerability of LFI (#139)
The problem seems to be when the proxy decrypts the value from the $_GET['q']
On this file:
https://github.com/Athlon1600/php-proxy-app/blob/master/index.php
We can see this on line 68:
// decode q parameter to get the real URL $url = url_decrypt($_GET['q']);
So lets take a look at url_decrypt() function that is on this file at line 155:
https://github.com/Athlon1600/php-proxy/blob/master/src/helpers.php
As you can see, it uses str_rop_pass() to decrypt the string:
function url_decrypt($url, $key = false){ $url = Config::get('url_mode') ? base64_url_decode($url) : rawurldecode($url);
if($key){
$url = str_rot_pass($url, $key, true);
} else if(Config::get('encryption_key')){
$url = str_rot_pass($url, Config::get('encryption_key'), true);
}
return $url;
}
A quick fix should be to validate the variable $url like this:
function url_decrypt($url, $key = false){ $url = Config::get('url_mode') ? base64_url_decode($url) : rawurldecode($url);
if($key){
$url = str_rot_pass($url, $key, true);
} else if(Config::get('encryption_key')){
$url = str_rot_pass($url, Config::get('encryption_key'), true);
}
if (!filter_var($url, FILTER_VALIDATE_URL)) return "";
if (!in_array(strtolower(parse_url($url, PHP_URL_SCHEME)), array("http","https"))) return "";
return $url;
}
So we return "" if the url is not valid or if it has a non-http/https scheme (i.e file:// or ftp://).
You may also want to use my SecurityPlugin:
Athlon1600/php-proxy-plugin-bundle#2https://github.com/Athlon1600/php-proxy-plugin-bundle/pull/2
It will increase the security of PHP-Proxy by validating many important things.
Hope this helps.
— You are receiving this because you commented. Reply to this email directly, view it on GitHubhttps://github.com/Athlon1600/php-proxy-app/issues/139#issuecomment-456329887, or mute the threadhttps://github.com/notifications/unsubscribe-auth/AhYGy481KBxW4ufqqHW8x1ivOnEd1G4rks5vFtnNgaJpZM4Y67W-.
@Benji-Collins
I just made a quick test now, and my SecurityPlugin prevents the $_GET['q'] LFI vulnerability.
It validates the URL scheme and returns "Scheme is not allowed" for file://
That’s great to hear. Thank you again.
From: Web Addicto [email protected] Sent: Tuesday, January 22, 2019 8:21 pm To: Athlon1600/php-proxy-app Cc: Benji-Collins; Mention Subject: Re: [Athlon1600/php-proxy-app] PHP-Proxy <= 5.1.0 - The decrypt key is flawed and cause the vulnerability of LFI (#139)
@Benji-Collinshttps://github.com/Benji-Collins
I just made a quick test now, and my SecurityPlugin already fixes the LFI vulnerability.
It validates the URL scheme and returns "Scheme is not allowed" for file://
— You are receiving this because you were mentioned. Reply to this email directly, view it on GitHubhttps://github.com/Athlon1600/php-proxy-app/issues/139#issuecomment-456337092, or mute the threadhttps://github.com/notifications/unsubscribe-auth/AhYGy0EJaB1BbSqHthjmAaDwnSFasP7aks5vFt8IgaJpZM4Y67W-.