dnsproxy produces too many logs for connection issues
https://github.com/AdguardTeam/dnsproxy/commit/f89e1bb91a3726db7c21617df60552acf2eeb0e9?notification_referrer_id=NT_kwDOAbZzjbM0Mjk5NDc0MzQ4OjI4NzM0MzQ5¬ifications_query=is%3Aunread#commitcomment-82615652
In fact, I don't understand why DOQ has such a problem. It is correct to write on the ADG client, but it will appear on the DNSProxy server, while DOT is normal
Android patch 2022.8 and above, all support DOQ (DOH3)
https://security.googleblog.com/2022/07/dns-over-http3-in-android.html
As discussed previously, please add the information about what upstream you're using and what client you're using. As well as a reproducer using dnslookup, if you can.
https://security.googleblog.com/2022/07/dns-over-http3-in-android.html
DNS-over-HTTP/3 and DNS-over-QUIC are different protocols. dnsproxy doesn't support DNS-over-HTTP/3 yet.
As discussed previously, please add the information about what upstream you're using and what client you're using. As well as a reproducer using
dnslookup, if you can.https://security.googleblog.com/2022/07/dns-over-http3-in-android.html
DNS-over-HTTP/3 and DNS-over-QUIC are different protocols.
dnsproxydoesn't support DNS-over-HTTP/3 yet.
Dnslookup is using https://github.com/ameshkov/dnslookup??
Yes. Preferably from master branch.
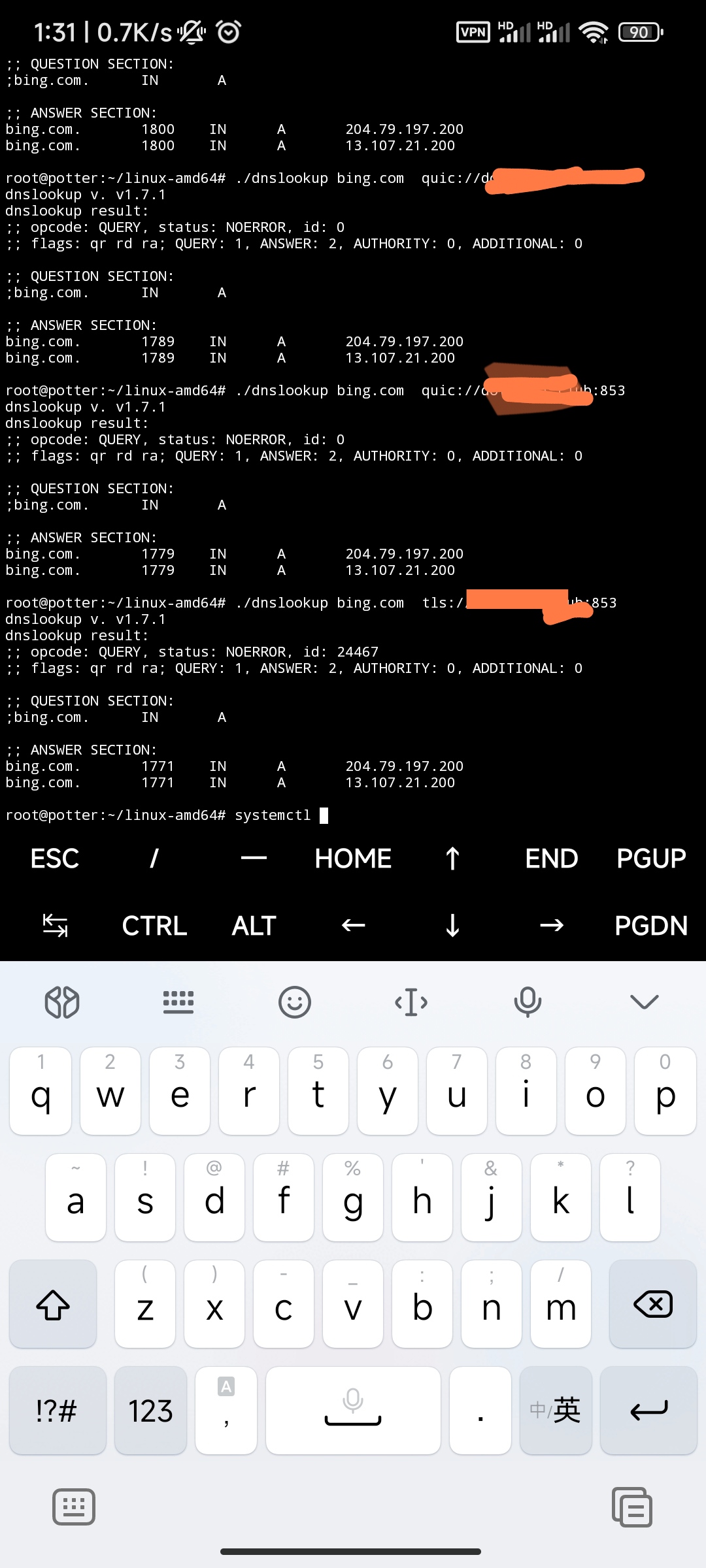 Parsing is normal
Parsing is normal
Everything seems to be normal. If your upstream and all other clients are up-to-date as well, it doesn't seem like there is an issue. DoQ is a relatively new standard, and such compatibility issues will probably not disappear for another year or so, so I would suggest either keeping all of your clients and upstreams up-to-date and following the standard or using DoT and/or DoH instead.
Everything seems to be normal. If your upstream and all other clients are up-to-date as well, it doesn't seem like there is an issue. DoQ is a relatively new standard, and such compatibility issues will probably not disappear for another year or so, so I would suggest either keeping all of your clients and upstreams up-to-date and following the standard or using DoT and/or DoH instead.
Yeah, I feel like everything's fine, too. But I don't know why this code name appears in the diary. It seems to be the use of DOH3. When I searched for related questions in Bing, I said it was DOQ (DOH3). The authors of Quic-Go also have a related problem.
Yes. Preferably from
masterbranch.
Do not support 1.19😂
There is a PR waiting for @ameshkov. See ameshkov/dnslookup#32. You can try building from there.
There is a PR waiting for @ameshkov. See ameshkov/dnslookup#32. You can try building from there.
It's not a problem. Just use the precompiled ones for now
How to detect DOH3? I only found QX support for ios
https://security.googleblog.com/2022/07/dns-over-http3-in-android.html
Let me see how I can get this PR right. Feel to add https://github.com/AdguardTeam/dnsproxy/pull/214
Why is this a problem?
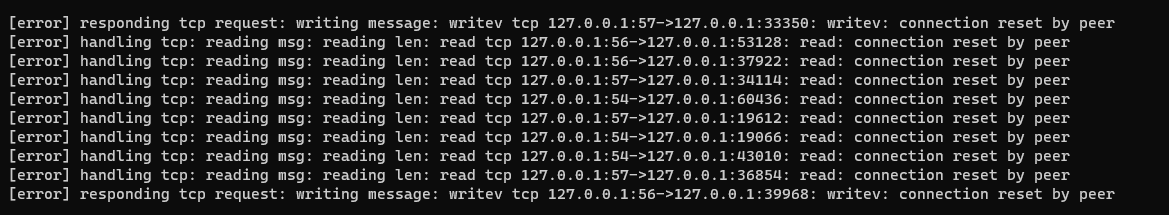
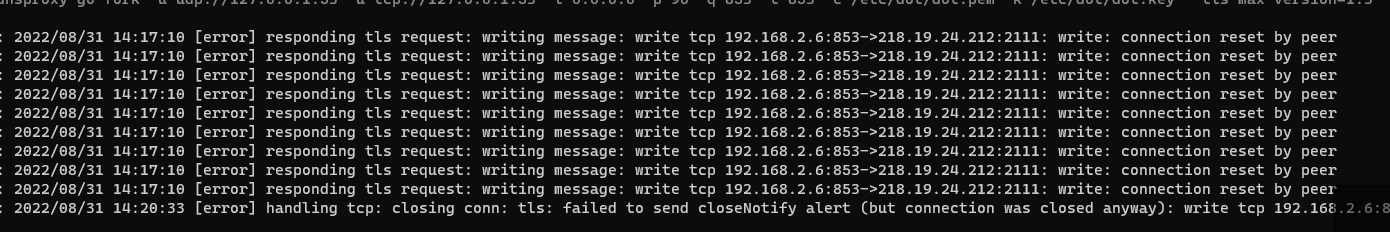
How to detect DOH3? I only found QX support for ios
I do not understand the question, sorry.
Why is this a problem?
connection reset by peer typically means that the client has dropped the connection.
Have you been able to reliably reproduce the original issue with the latest versions of dnsproxy and dnslookup?
How to detect DOH3? I only found QX support for ios
I do not understand the question, sorry.
Why is this a problem?
connection reset by peertypically means that the client has dropped the connection.Have you been able to reliably reproduce the original issue with the latest versions of
dnsproxyanddnslookup?
It's fine on DNSLookup, but the DNSProxy diary is pretty dysfunctional, most of the time
Are there any plans to replace the cache GO?@ainar-g
@Potterli20, I do not understand the question, sorry. Please write your questions in any language you're comfortable with.
@Potterli20, I do not understand the question, sorry. Please write your questions in any language you're comfortable with.
你们可以更新一下go的依赖缓存。我看到了官方不在更新,但其他二次开发的cache效果也不错
@Potterli20, I do not understand the question, sorry. Please write your questions in any language you're comfortable with.
你们可以更新一下go的依赖缓存。我看到了官方不在更新,但其他二次开发的cache效果也不错
如zgo.at/zcache的go cache
@Potterli20, I do not understand the question, sorry. Please write your questions in any language you're comfortable with.
Just because it seems to me that the cache is not as good as the original GO cache. Emmm watch yours.
How is cache relevant to errors in logs?
Please, keep the discussion relevant to the issue. This is an issue tracker and not a discussion forum.
How is cache relevant to errors in logs?
Please, keep the discussion relevant to the issue. This is an issue tracker and not a discussion forum.
If the request is relevant, the cache is also required.
Because he could read and write. That's probably why. After all, my program is DNSProxy and DNS shunting file (relatively large).
现在出现假运行的状态,程序是正常,但反馈数据是无效的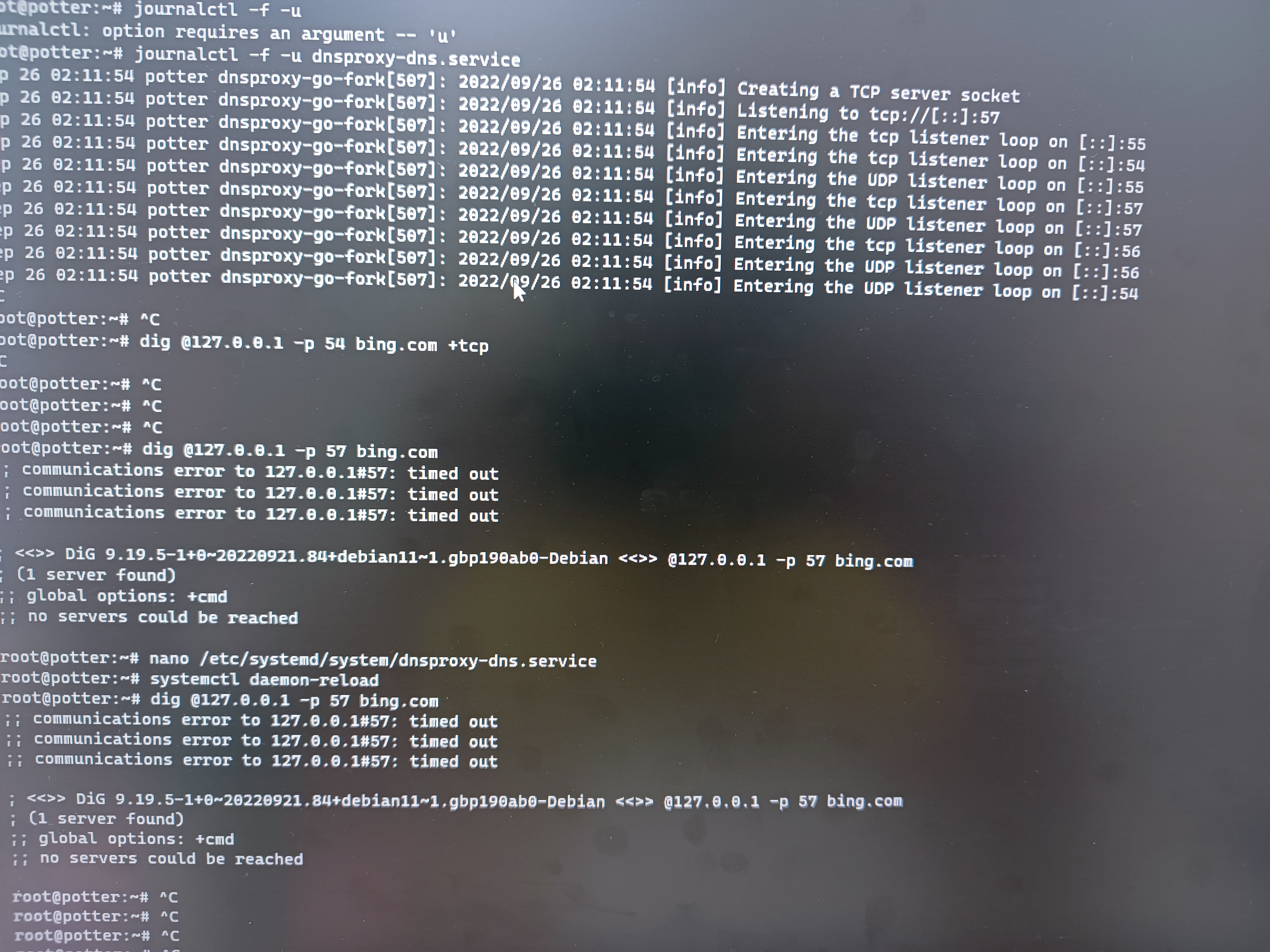
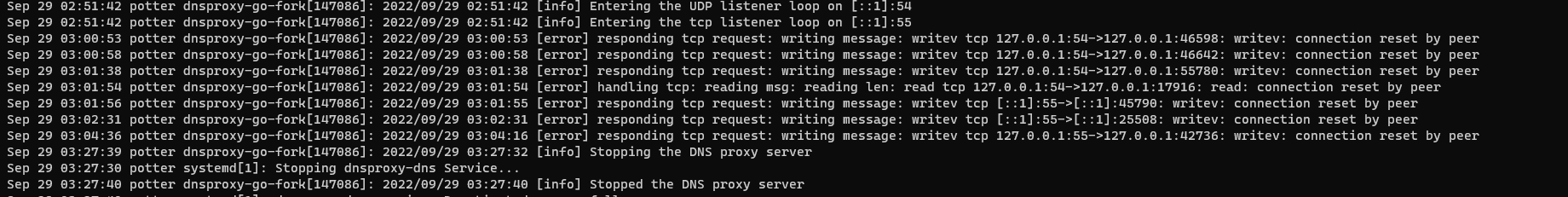
Sep 29 03:00:53 potter dnsproxy-go-fork[147086]: 2022/09/29 03:00:53 [error] responding tcp request: writing message: writev tcp 127.0.0.1:54->127.0.0.1:46598: writev: connection reset by peer
Sep 29 03:00:58 potter dnsproxy-go-fork[147086]: 2022/09/29 03:00:58 [error] responding tcp request: writing message: writev tcp 127.0.0.1:54->127.0.0.1:46642: writev: connection reset by peer
Sep 29 03:01:38 potter dnsproxy-go-fork[147086]: 2022/09/29 03:01:38 [error] responding tcp request: writing message: writev tcp 127.0.0.1:54->127.0.0.1:55780: writev: connection reset by peer
Sep 29 03:01:54 potter dnsproxy-go-fork[147086]: 2022/09/29 03:01:54 [error] handling tcp: reading msg: reading len: read tcp 127.0.0.1:54->127.0.0.1:17916: read: connection reset by peer
Sep 29 03:01:56 potter dnsproxy-go-fork[147086]: 2022/09/29 03:01:55 [error] responding tcp request: writing message: writev tcp [::1]:55->[::1]:45790: writev: connection reset by peer
Sep 29 03:02:31 potter dnsproxy-go-fork[147086]: 2022/09/29 03:02:31 [error] responding tcp request: writing message: writev tcp [::1]:55->[::1]:25508: writev: connection reset by peer
Sep 29 03:04:36 potter dnsproxy-go-fork[147086]: 2022/09/29 03:04:16 [error] responding tcp request: writing message: writev tcp 127.0.0.1:55->127.0.0.1:42736: writev: connection reset by peer
Sep 28 21:50:23 potter dnsproxy-go-fork[123878]: 2022/09/28 21:50:21 [error] handling tcp: handling tcp request: talking to dns upstream: all upstreams failed to respond: 15 errors: "requesting https://1.12.12.12:443/dns-query: Get "https://1.12.12.12:443/dns-query?dns=AAABAAABAAAAAAABBkt1a09ORwloSVNtQXJ0VFYDQ29tAAABAAEAACkFwAAAgAAACwAIAAcAARgAwKgC": all dialers failed: dial tcp 1.12.12.12:443: i/o timeout", "getting connection to tls://223.6.6.6:853: connecting to 223.6.6.6: EOF", "getting connection to tls://dns.alidns.com:853: connecting to dns.alidns.com: EOF", "getting connection to tls://223.5.5.5:853: connecting to 223.5.5.5: EOF", "getting connection to tls://1.12.12.12:853: connecting to 1.12.12.12: all dialers failed: dial tcp 1.12.12.12:853: i/o timeout", "requesting https://doh.pub:443/dns-query: Get "https://doh.pub:443/dns-query?dns=AAABAAABAAAAAAABBkt1a09ORwloSVNtQXJ0VFYDQ29tAAABAAEAACkFwAAAgAAACwAIAAcAARgAwKgC": net/http: request canceled while waiting for connection (Client.Timeout exceeded while awaiting headers)", "getting connection to tls://dns.pub:853: connecting to dns.pub: all dialers failed: dial tcp 106.55.127.112:853: i/o timeout", "getting connection to tls://dot.360.cn:853: connecting to dot.360.cn: EOF", "requesting https://dns.alidns.com:443/dns-query: Get "https://dns.alidns.com:443/dns-query?dns=AAABAAABAAAAAAABBkt1a09ORwloSVNtQXJ0VFYDQ29tAAABAAEAACkFwAAAgAAACwAIAAcAARgAwKgC": EOF", "requesting https://doh.360.cn:443/dns-query: Get "https://doh.360.cn:443/dns-query?dns=AAABAAABAAAAAAABBkt1a09ORwloSVNtQXJ0VFYDQ29tAAABAAEAACkFwAAAgAAACwAIAAcAARgAwKgC": net/http: request canceled while waiting for connection (Client.Timeout exceeded while awaiting headers)", "getting connection to tls://120.53.53.53:853: connecting to 120.53.53.53: write tcp 192.168.2.4:3612->120.53.53.53:853: i/o timeout", "requesting https://223.5.5.5:443/dns-query: Get "https://223.5.5.5:443/dns-query?dns=AAABAAABAAAAAAABBkt1a09ORwloSVNtQXJ0VFYDQ29tAAABAAEAACkFwAAAgAAACwAIAAcAARgAwKgC": EOF", "requesting https://120.53.53.53:443/dns-query: Get "https://120.53.53.53:443/dns-query?dns=AAABAAABAAAAAAABBkt1a09ORwloSVNtQXJ0VFYDQ29tAAABAAEAACkFwAAAgAAACwAIAAcAARgAwKgC": net/http: request canceled while waiting for connection (Client.Timeout exceeded while awaiting headers)", "requesting https://sm2.doh.pub:443/dns-query: Get "https://sm2.doh.pub:443/dns-query?dns=AAABAAABAAAAAAABBkt1a09ORwloSVNtQXJ0VFYDQ29tAAABAAEAACkFwAAAgAAACwAIAAcAARgAwKgC": net/http: request canceled while waiting for connection (Client.Timeout exceeded while awaiting headers)", "requesting https://223.6.6.6:443/dns-query: Get "https://223.6.6.6:443/dns-query?dns=AAABAAABAAAAAAABBkt1a09ORwloSVNtQXJ0VFYDQ29tAAABAAEAACkFwAAAgAAACwAIAAcAARgAwKgC": net/http: request canceled while waiting for connection (Client.Timeout exceeded while awaiting headers)"
