AdGuardHome
 AdGuardHome copied to clipboard
AdGuardHome copied to clipboard
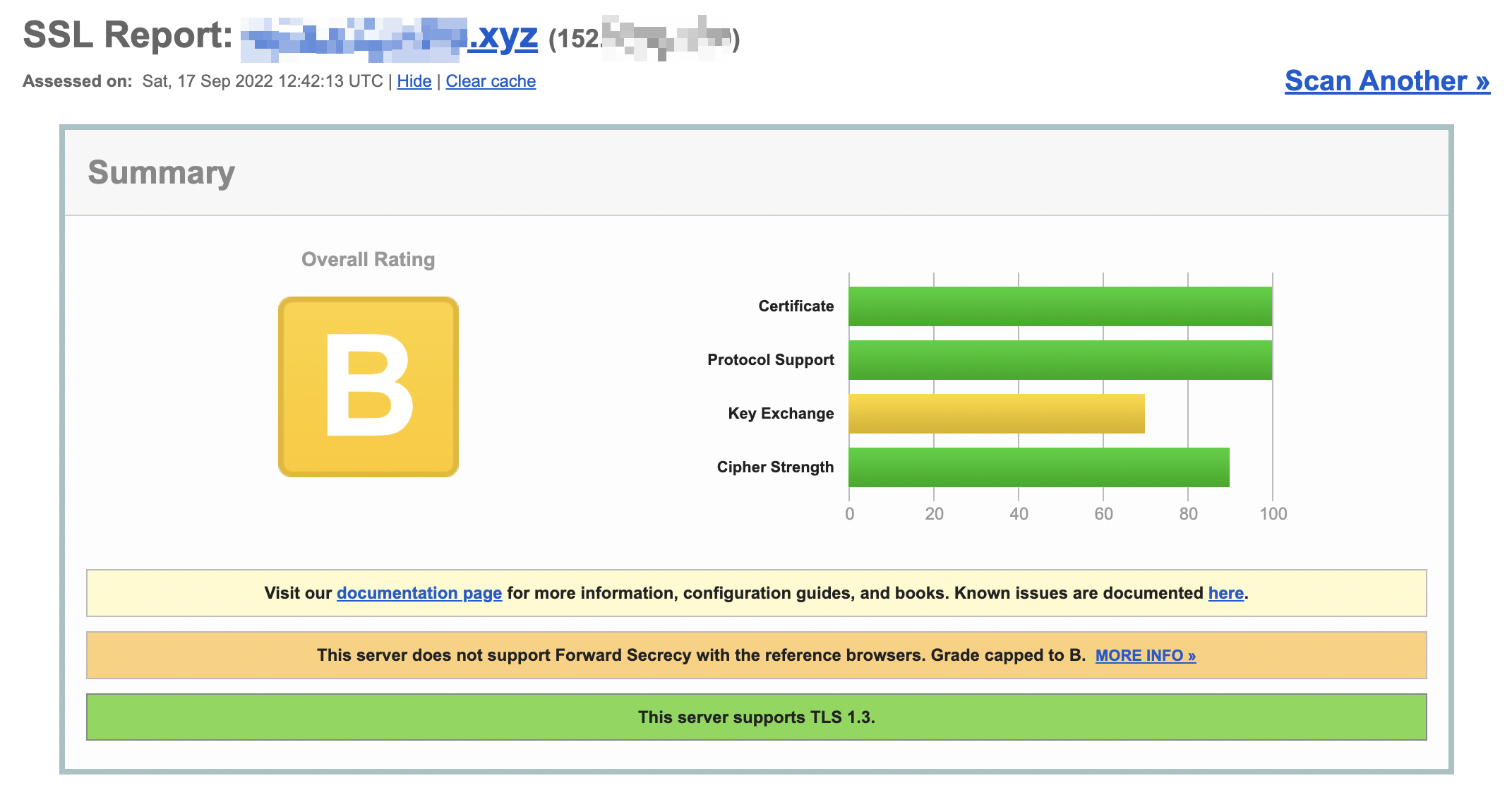
ssllab result capped to B
Prerequisites
-
[X] I have checked the Wiki and Discussions and found no answer
-
[X] I have searched other issues and found no duplicates
-
[X] I want to report a bug and not ask a question
Operating system type
Linux, OpenWrt
CPU architecture
AMD64
Installation
Docker
Setup
On one machine
AdGuard Home version
v0.108.0-b.15
Description
What did you do?
SSL Lab test result is B
ref : https://blog.qualys.com/product-tech/2018/02/02/forward-secrecy-authenticated-encryption-and-robot-grading-update
Seems like additional config changes at go http listener
Expected result
Actual result
Screenshots (if applicable)
Additional information
Reference Article to check : https://www.namecheap.com/support/knowledgebase/article.aspx/9653/38/how-to-check-whether-the-server-supports-forward-secrecy/
tried openssl s_client -connect example.com:443 -cipher "DHE, EDH" , the request was failing,
I dont ve idea about these ciphers. I tried for few sites with ssl lab report A+ the above command was passing
The SSL Labs report is rather weird, as we do provide cipher suites with FS by default, such as TLS_AES_256_GCM_SHA384, TLS_CHACHA20_POLY1305_SHA256, and others.
Regarding your PR, I'd rather not merge it, because we specifically removed CBC cipher suites to avoid Zombie Poodle and other issues with CBC. In fact, there are even proposals to completely disable CBC ciphers by default in Go, so enabling them back doesn't sound like a good idea.
Also, regarding the test, we test AdGuard Home with https://github.com/drwetter/testssl.sh/, which currently shows the A grade. Considering that it's based on SSL Labs' SSL Server Rating Guide, the discrepancy between the results is weird.
Perhaps, we should add a setting to the configuration file to let users explicitly define, which ciphers they'd like to use.
@ainar-g , https://github.com/AdguardTeam/AdGuardHome/pull/4990
updated PR https://github.com/AdguardTeam/AdGuardHome/pull/4990
If I recall correctly, both the ciphers and the HSTS issues are now resolved?
Yes, we are good,
For SSL Cipher, Users Can choose what they needs, HSTS is enabled by default when we enable https