zrlog
 zrlog copied to clipboard
zrlog copied to clipboard
ZrLog是使用 Java 开发的博客/CMS程序,具有简约,易用,组件化,内存占用低等特点。自带 Markdown 编辑器,让更多的精力放在写作上,而不是花费大量时间在学习程序的使用上。
Bumps [terser](https://github.com/terser/terser) from 5.14.1 to 5.14.2. Changelog Sourced from terser's changelog. v5.14.2 Security fix for RegExps that should not be evaluated (regexp DDOS) Source maps improvements (#1211) Performance improvements in...
Bumps [terser](https://github.com/terser/terser) from 4.8.0 to 4.8.1. Changelog Sourced from terser's changelog. v4.8.1 (backport) Security fix for RegExps that should not be evaluated (regexp DDOS) Commits See full diff in compare...
Bumps [moment](https://github.com/moment/moment) from 2.29.1 to 2.29.4. Changelog Sourced from moment's changelog. 2.29.4 Release Jul 6, 2022 #6015 [bugfix] Fix ReDoS in preprocessRFC2822 regex 2.29.3 Full changelog Release Apr 17, 2022...
Just download a plugin and intercept your data package. data package like this modify the JAR just downloaded, join the malicious code in the startup class. then modify the parameter...
there is a remote command execution vulnerability at the upload avatar function on the background. upload pictures, then intercept data package, like this 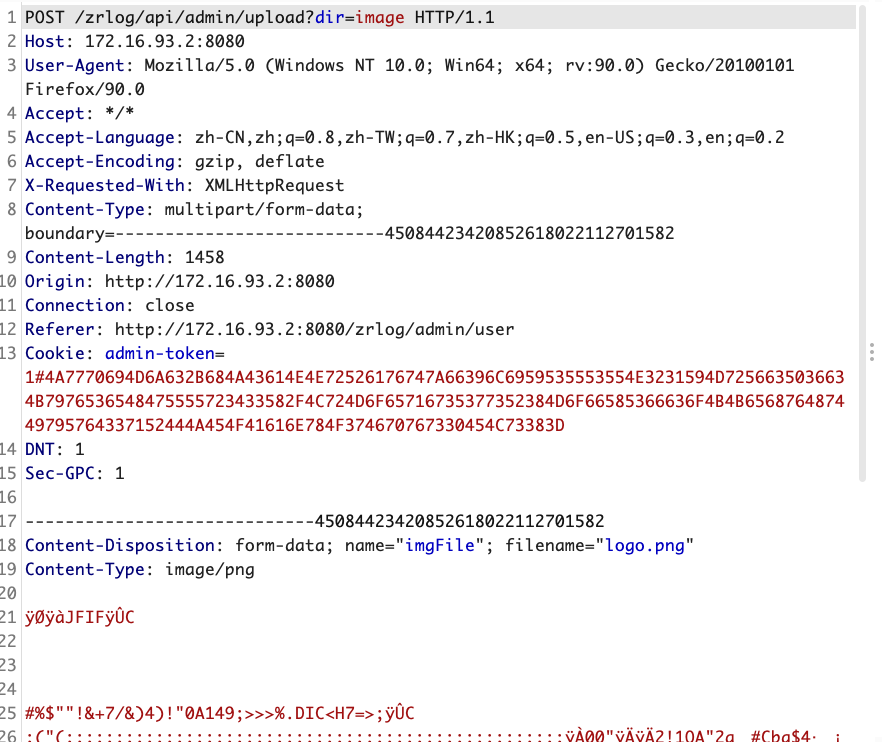 then modify the file name to...
After the file is uploaded correctly, "`[abc](/zrlog/attached/file/20180918/20180918000718_50.jpg "abc")`" will be displayed in the edit box.Combined with the page display, the XSS purpose is achieved by modifying the display content. Poc...
第5个漏洞,漏洞类型:java/path-injection;漏洞描述:;漏洞文件位置:web/src/main/java/com/zrlog/web/controller/BaseController.java;漏洞行数:37, 数据流:代码流:web/src/main/java/com/zrlog/web/interceptor/TemplateHelper.java:第230行|第39列|至第56列|参数名或方法名:getValue(...) : String==>web/src/main/java/com/zrlog/web/interceptor/TemplateHelper.java:第235行|第16列|至第31列|参数名或方法名:previewTemplate : String==>web/src/main/java/com/zrlog/web/controller/BaseController.java:第33行|第31列|至第96列|参数名或方法名:getTemplatePathByCookie(...) : String==>web/src/main/java/com/zrlog/web/controller/BaseController.java:第37行|第23列|至第62列|参数名或方法名:... + ... 第6个漏洞,漏洞类型:java/path-injection;漏洞描述:;漏洞文件位置:web/src/main/java/com/zrlog/web/controller/admin/page/AdminArticlePageController.java;漏洞行数:32, 数据流:代码流:web/src/main/java/com/zrlog/web/interceptor/TemplateHelper.java:第230行|第39列|至第56列|参数名或方法名:getValue(...) : String==>web/src/main/java/com/zrlog/web/interceptor/TemplateHelper.java:第235行|第16列|至第31列|参数名或方法名:previewTemplate : String==>web/src/main/java/com/zrlog/web/controller/BaseController.java:第33行|第31列|至第96列|参数名或方法名:getTemplatePathByCookie(...) : String==>web/src/main/java/com/zrlog/web/controller/BaseController.java:第40行|第16列|至第28列|参数名或方法名:templatePath : String==>web/src/main/java/com/zrlog/web/controller/admin/page/AdminArticlePageController.java:第32行|第57列|至第74列|参数名或方法名:getTemplatePath(...) : String==>web/src/main/java/com/zrlog/web/controller/admin/page/AdminArticlePageController.java:第32行|第30列|至第74列|参数名或方法名:... + ... 第7个漏洞,漏洞类型:java/path-injection;漏洞描述:;漏洞文件位置:web/src/main/java/com/zrlog/web/controller/admin/page/AdminTemplatePageController.java;漏洞行数:69, 数据流:代码流:web/src/main/java/com/zrlog/web/controller/admin/page/AdminTemplatePageController.java:第67行|第31列|至第72列|参数名或方法名:getParameter(...) : String==>web/src/main/java/com/zrlog/web/controller/admin/page/AdminTemplatePageController.java:第69行|第34列|至第121列|参数名或方法名:... + ......
This newest version of the zrlog has a storage XSS in article comments.The attacker can insert the malicious XSS code into the comments and submit it. When the background blogger...
This version of the zrlog backstage management has CSRF vulnerability.The attacker can induce the user to visit the CSRF attack page, and then use the user's credentials for malicious operations...
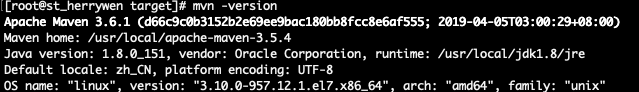 mvn版本3.6.1,jdk版本1.8,克隆代码后,在项目主目录下执行"mvn clean install -Dmaven.test.skip=true",在target中生成对应war包  放在tomcat的webapps下,访问无法跳出安装界面,这是mvn版本太新导致的么?