unicorn
 unicorn copied to clipboard
unicorn copied to clipboard
Bad address in UC_HOOK_MEM_WRITE hook
I'm doing some tests on the latest version of the engine, through the Python's module and I encountered a weird address on the 8th call of the UC_HOOK_MEM_WRITE hook callback function call, while processing a shikata ga nai shellcode, found in VirusTotal.
On Unicorn 1.0.1, the address seem to be valid, see in the image below:
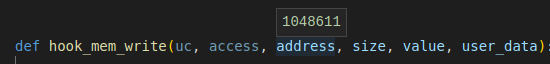
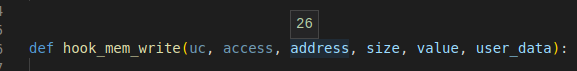
And on the latest 2.0.1.post1, this is the received address:
Attaching an encrypted zip containing the shellcode data itself, password: infected shikata.zip
Let me know if I'm interpreting the situation wrongly.
If you need more information, let me know.
Thanks
1.0.1 seems way too old. What's your expected output?
1.0.1 seems way too old. What's your expected output?
As I attached the expected result of the correct address that emulated by 1.0.1, I expect the 2,0,1 to give me the same result, and definitely not an illogical number that referring to an address, 26. The idea is to use the hook to catch self modifying code, like the shikata ga nai encoder, so to do that, the write and read hooks let me manage a state and test it later for code overwriting in-memory.
Can you provide a minimal script to reproduce the bug?
This issue is stale because it has been open 60 days with no activity. Remove stale label or comment or this will be closed in 15 days.