TheCodeAssassin
TheCodeAssassin
@aeneasr I hope all is well. Is there any chance this will be picked up soon? It's rather inconvenient for our users seeing as we rely on metadata to assign...
> Thank you very much. Yes, our solution is already in production.
@aeneasr is there a workaround? Can we somehow retrieve their OIDC login id? I need their Discord ID for example. This is our mapping file: https://storage.googleapis.com/bac-gcs-production/7db4d530162115ee985f43d49c6ad725ca92d69a714a0fe0676a878e7eb4b0f283e849675fe3caf1374fab7bdd5dc6660a3e1e8d4e08db1baaa6e1a42e6071b5.jsonnet is the claims.sub stored...
@shagamemnon thank you for the quick response. We created the logpush job via terraform: ```hcl resource "cloudflare_logpush_job" "logs" { for_each = { for dataset in local.datasets : dataset.id => dataset...
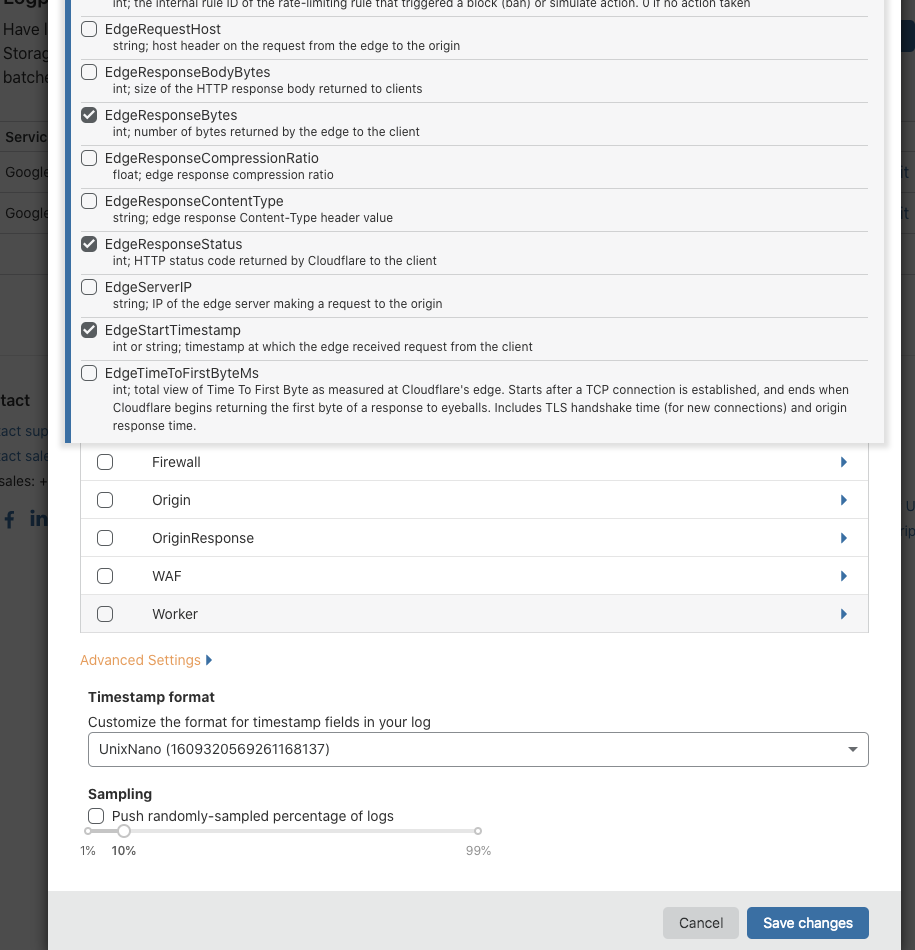 this is what terraform configured by default. This is possible: ```hcl loggpull_options = "fields=RayID,ClientIP,EdgeStartTimestamp×tamps=rfc3339" ``` But by default it seems that if you create the logpush job...
Hello, we are also having this issue. We are currently not using replication but we do want to use it in the future. We are using ioredis to connect to...
As a curiosity here, why is this even necessary? it's really intuitive as privileged: true is necessary to make exposing services work. Shouldn't this be the default? It feels like...
Little bump on this issue, it would be great if this could be supported on live streams.
> Some minor changes, something I didn't think of is that we have mandatory TLS configuration with `etcd`. > > It would be perfect if we could have a validating...
When we push this version we need to make sure people upgrade their CRDs otherwise NATS and no-tls configs won't be supported.