split-vpn
 split-vpn copied to clipboard
split-vpn copied to clipboard
Troubleshooting Openconnect
I am in the process of trying to get an Openconnect connection running with AnyConnect. I'm not exactly sure where to start. Here is my config without any comments:
DNS_IPV4_PORT=53
DNS_IPV4_INTERFACE=""
DNS_IPV6_IP="REJECT"
DNS_IPV6_PORT=53
DNS_IPV6_INTERFACE=""
KILLSWITCH=0
REMOVE_KILLSWITCH_ON_EXIT=1
REMOVE_STARTUP_BLACKHOLES=1
VPN_PROVIDER="openconnect"
GATEWAY_TABLE="auto"
ROUTE_TABLE=101
MARK=0x9
PREFIX="VPN_"
PREF=99
DEV=tun0
Right now I am able to use Openconnect on a fresh linux install with no issue; DNS works, etc.. The server I am connecting to has routes preconfigured so not all traffic will be routed. Starting the VPN from split-vpn shows logs as if it's working, but nothing actually happens/works on any of my clients. I'm sure this may just be a config thing but I'm not sure.
I do notice this one line in the openconnect log:
[Wed Jun 1 21:39:25 EDT 2022] split-vpn: Using IPv4 gateway from table 201: via 10.5.3.254 dev eth8.
My lan is on 10.15.0.0/24 and the openconnect client address is on a 10.195.x.x network. I don't recognize the 10.5.3.254. Are there conflicting subnets?
Hi @13mralex,
Sorry for the late reply.
By default the script routes all traffic. You can change that behavior in the settings. But first, can you check the route table for the VPN to see if the routes got added? What routes are you expecting?
ip route show table 101
Also, it is better if you use something other than 0x9 for the fwmark because that's going to conflict with some UDM services as I recently found out. Please try to use 0x169 instead.
My lan is on 10.15.0.0/24 and the openconnect client address is on a 10.195.x.x network. I don't recognize the 10.5.3.254. Are there conflicting subnets?
via 10.5.3.254 dev eth8 is your default WAN gateway that the system assigned (the script just looks it up from table 201 - a Unifi OS controlled route table). So 10.5.3.254 must be a subnet on your WAN.
Yes, I can see that routes were added. Although would some of these be conflicting too? Looking at 10.0.0.0/8.
# ip route show table 101
0.0.0.0/1 dev tun0 scope link
blackhole default
10.0.0.0/8 dev tun0 scope link
10.195.21.195 dev tun0 scope link
128.0.0.0/1 dev tun0 scope link
128.10.0.0/16 dev tun0 scope link
128.46.0.0/16 dev tun0 scope link
128.210.0.0/16 dev tun0 scope link
128.210.0.150 via 10.5.3.254 dev eth8
128.210.11.5 dev tun0 scope link
128.210.11.57 dev tun0 scope link
128.211.0.0/16 dev tun0 scope link
163.245.0.0/16 dev tun0 scope link
172.16.0.0/12 dev tun0 scope link
192.5.40.0/24 dev tun0 scope link
192.31.0.0/24 dev tun0 scope link
204.52.32.0/20 dev tun0 scope link
205.132.168.0/23 dev tun0 scope link
205.132.170.0/24 dev tun0 scope link
Cisco AnyConnect:
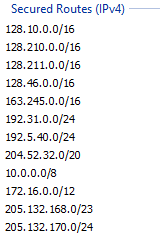
I don't think I absolutely need the 10.0.0.0/8 network if it does conflict. What setting(s) do I change to only route the above networks?
To disable the default routes, you just need to add this option in your vpn.conf (you can add it anywhere, it's not in the sample config).
DISABLE_DEFAULT_ROUTE=1
As for 10.0.0.0/8, you should disable that from the OpenConnect server side.
Also, have you tested if the connection is working? Can you ping an IP on the OpenConnect routes?
Hi @13mralex,
This issue has become stale so I'm closing it, but if you ever wan to continue debugging, feel free to re-open!