plugins
 plugins copied to clipboard
plugins copied to clipboard
Wireguard breaking routing table (insert route incorrectly)
Important notices Before you add a new report, we ask you kindly to acknowledge the following:
- [X] I have read the contributing guide lines at https://github.com/opnsense/plugins/blob/master/CONTRIBUTING.md
- [X] I have searched the existing issues, open and closed, and I'm convinced that mine is new.
- [X] The title contains the plugin to which this issue belongs
Describe the bug
Followed instructions https://docs.opnsense.org/manual/how-tos/wireguard-client-mullvad.html WireGuard MullvadVPN Road Warrior Setup.
Wireguard is inserting a route 0.0.0.0/1 above the default route, causing a break in firewall connectivity.
Note: An existing wireguard local connection has been established utilizing wg0 (working correctly). Testing was conducted creating either wg1 or wg2.
To Reproduce Wrote down the following steps and have been able to reproduce using steps. Started from VPN: WireGuard.
Select local Select plus
Settings filled in for "edit local configuration" Name testingroutingerror Listening Port 1514 Tunnel Address 10.0.0.1/24 Save
Skip ssh inputs for modifying dns (Downloaded configuration from Provider)
Clicked on edit for "testingroutingerror" and modified following. Tunnel Address 10.65.66.154/32 Save
Select endpoints Select plus
Settings filled in for "edit endpoint" Name RemotePeerTest Public Key dnmvpTXpcFy4SQdrqnHODhD3j0kZ0fijSGtwxvLd0R8= Allowed IPs 0.0.0.0/0 Endpoint Add 138.199.60.28 Endpoint Port 3500 Save
Clicked on edit for "testingroutingerror" and modified following. Peers RemotePeerTest Save
Clicked on Apply
Expected behavior As shown below, the routing table should have the default route as the first entry. #####System: Routes##### Proto Destination Gateway Flags Use MTU Netif Netif (name) Expire Action ipv4 default 142.129.32.1 UGS NaN 1500 re0 WANInterface ipv4 192.168.1.0/24 link#7 U NaN 9000 re0V1
Screenshots
#####VPN: WireGuard: List configurations##### interface: wg2 public key: NUXrsPL26zNg/8fnaSicOiHQZOoEZ14ivedgWxzSKT0= private key: (hidden) listening port: 1514
peer: dnmvpTXpcFy4SQdrqnHODhD3j0kZ0fijSGtwxvLd0R8= endpoint: 138.199.60.28:3500 allowed ips: 0.0.0.0/0
This displays the routing table with an incorrect entry of 0.0.0.0/1 (link 16) being above the default. #####System: Routes: Status##### Proto Destination Gateway Flags Use MTU Netif Netif (name) Expire Action ipv4 0.0.0.0/1 link#16 US NaN 1420 wg2 ipv4 default #.#.#.#. UGS NaN 1500 re0 WANInterface ipv4 192.168.1.0/24 link#7 U NaN 9000 re0V1
Relevant log files If applicable, information from log files supporting your claim.
Additional context Add any other context about the problem here.
Environment OPNsense 22.1.10 (amd64, OpenSSL).
When you set 0.0.0.0/0 in AllowedIPs in Endpoint, you tell wireguard to route all traffic through it (which creates 2 routes to force it 0.0.0.0/1 and 128.0.0.0/1). If this is a central server just leave this field empty.
That is understood. What I am stating is, before configuring Wireguard the default route is highlighted in blue using interface re0. Once creating the VPN connection, 0.0.0.0/1 is inserted (above the original default route) as the first entry for the routing table using wg1.
All internal firewall, LAN / VLAN, attempting to access the Internet fails because the traffic uses the erroneous 0.0.0.0/1 default route on interface wg1.
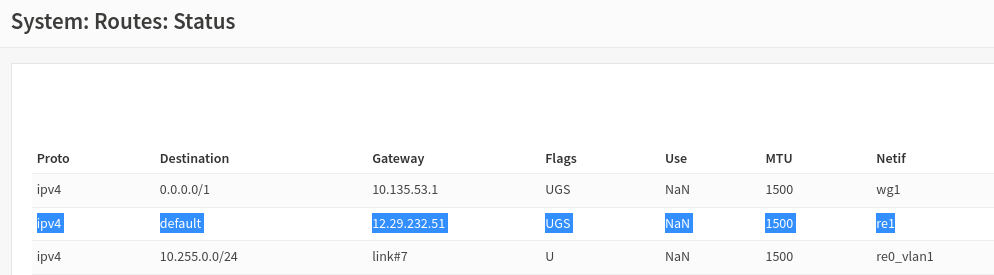
But this is what you tell Wireguard to do. You tell Wireguard route everything through the tunnel. If you dont want this, tick "Disable Routes"
This issue has been automatically timed-out (after 180 days of inactivity).
For more information about the policies for this repository, please read https://github.com/opnsense/plugins/blob/master/CONTRIBUTING.md for further details.
If someone wants to step up and work on this issue, just let us know, so we can reopen the issue and assign an owner to it.