plugins
 plugins copied to clipboard
plugins copied to clipboard
FreeRadius EAP-TLS allows successfull auth without related user
If you configure EAP-TLS with custom certificates and activate VLAN assignment a valid client certificate (with no user matching the user-name) is allowed to log-in. This is fatal as the VLAN used is the default / management VLAN.
Is there any option to "not authorize" clients that don't match an user (which would put them in the correct VLAN)?
Of course you could work with only a CRL, but this is really dangerous as you can easily forget to add an user which then means the user has access to the management net.
Am I overlooking some option here?
Isnt this intended as EAP-TLS is certificate only like with OpenVPN?
@mimugmail PFSense default behavior at least checks for the user. And also since you can assign VLANs on a per user basis, how should that work without the data which comes from the users details. The certificate can not deliver these information (VLAN-ID).
In our company they use cisco WLCs with ISE, which also checks for a profile existing besides the valid certificate.
I think an option to set "verify for existing user" is required.
Thank you for creating an issue. Since the ticket doesn't seem to be using one of our templates, we're marking this issue as low priority until further notice.
For more information about the policies for this repository, please read https://github.com/opnsense/plugins/blob/master/CONTRIBUTING.md for further details.
The easiest option to gain traction is to close this ticket and open a new one using one of our templates.
I did a quick search on the net and the first 3 hits tell me EAP-TLS doesnt require and even offer a field for username input. https://wiki.alpinelinux.org/wiki/FreeRadius_EAP-TLS_configuration https://community.arubanetworks.com/community-home/digestviewer/viewthread?MID=40904 https://community.cisco.com/t5/wireless/do-i-need-a-username-and-pasword-when-using-eaptls-802-1x/td-p/4481681
If you find out how to do this in FreeRadius on pfsense and what changes in radius config I can try to adapt it.
The username is in the CN of the certificate. When you create a certificate per user you put in the username as identifier.
Option in PFSense
PFSense has an option to toggle this behavior - They named it "Check Client Certificate CN":
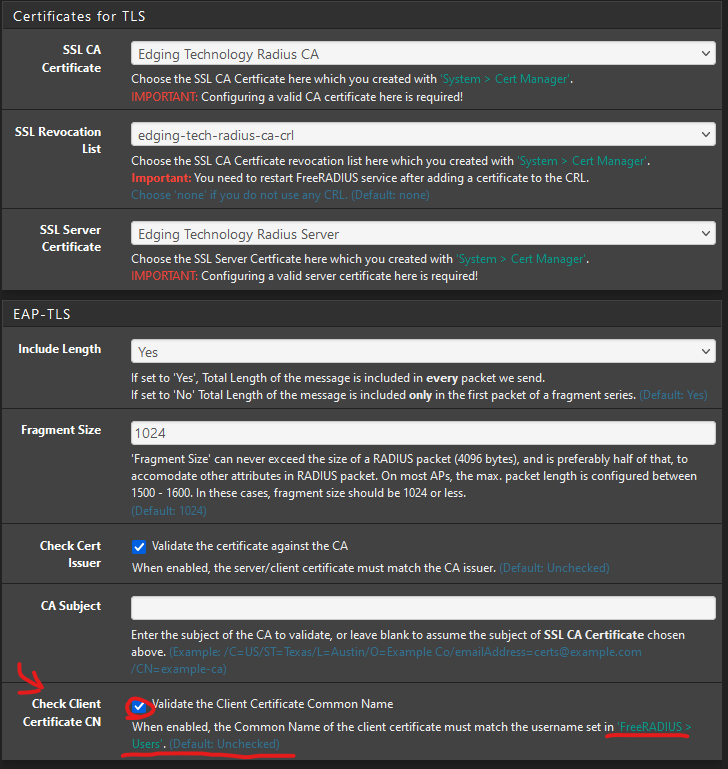
Client Certificate
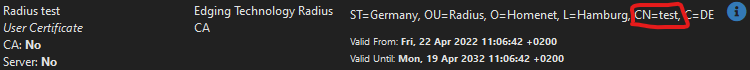
What changes when I toggle "Check Client Certificate CN"
When I toggle this in PFSense, the only thing that changes in the radius folder is:

Tho I guess the real magic happens in /usr/local/etc/raddb/sites-enabled/default:
It checks in the "users file" and if no entries were found, it rejects the auth.
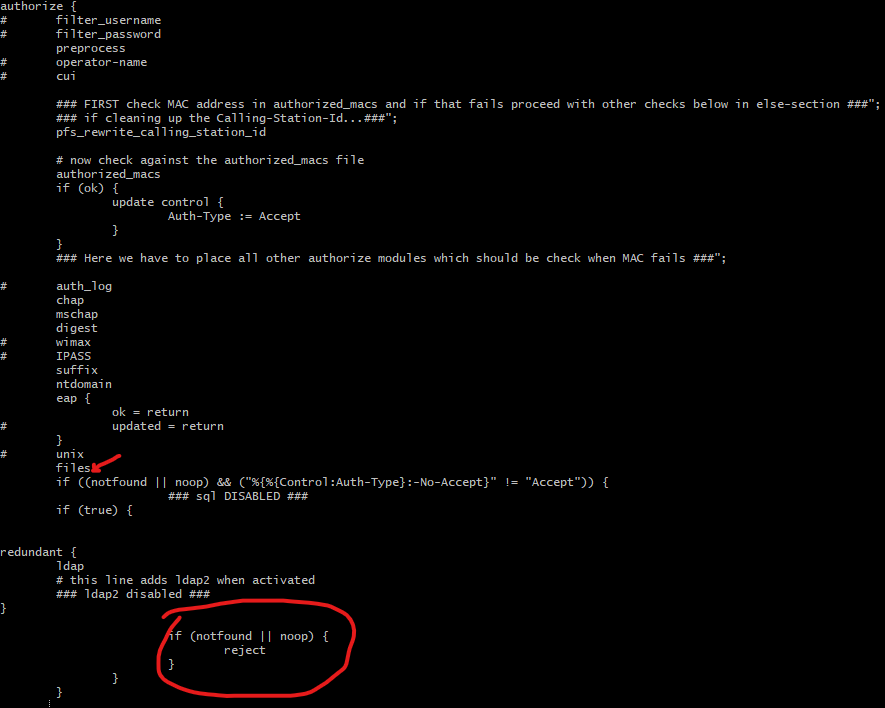
Can you run the diff against the whole folder please? :)
Exactly what I did, it hasn't changed anything else. These are the files I compared. I created a zip before and after and compared them.

This issue has been automatically timed-out (after 180 days of inactivity).
For more information about the policies for this repository, please read https://github.com/opnsense/plugins/blob/master/CONTRIBUTING.md for further details.
If someone wants to step up and work on this issue, just let us know, so we can reopen the issue and assign an owner to it.