build
 build copied to clipboard
build copied to clipboard
Cloudflare captchas break automated tooling, like nvm
Captchas under https://nodejs.org/dist break things like nvm (https://github.com/nvm-sh/nvm/issues/2694)
Since that content is highly CDN-able, is there a reason there's captchas enabled on that URL segment at all?
Think you meant https://github.com/nvm-sh/nvm/issues/2694
@rvagg @jbergstroem Do you know if this is something we turned on deliberately?
@rvagg @jbergstroem Do you know if this is something we turned on deliberately?
Its usually related to the security level chosen for the account. Based on the level you can also choose how to deal with said traffic; drop, captcha, etc.
We can review security settings but as far as I know there hasn't been any changes to this recently. Lets check the audit logs.
Finally, there might be a way to lower it per route; will look shortly.
It definitely could be an old change; it’s just that a user newly encountered it and reported it.
So, the best we can do in our current level (business) is "essentially off"; whereas enterprise accounts would get "off" as an option. I can check in with our account exec's and see if that is possible. They have been very helpful in enabling other (enterprise-only) features in the past on request.
It'd also be fine to have most of nodejs.org on "essentially off" and "/dist" on "off", since only nodejs.org/dist is really something programmatic tools are expected to use, if that's an option.
@ljharb yes, agreed. I'm checking with our contacts at cloudflare if we can get the "off" setting made available.
@jbergstroem happy new year! any chance we've heard back?
It's possible to configure Cloudflare page rules to set custom security levels, and other security settings, which can lead to the CAPTCHA appearing.
Given the URL that needs to be "unblocked" is on a single path /dist, it looks like this would be an approach that works.
It's possible to configure Cloudflare page rules to set custom security levels, and other security settings, which can lead to the CAPTCHA appearing.
Unfortunately not "off" unless you're using an enterprise account:
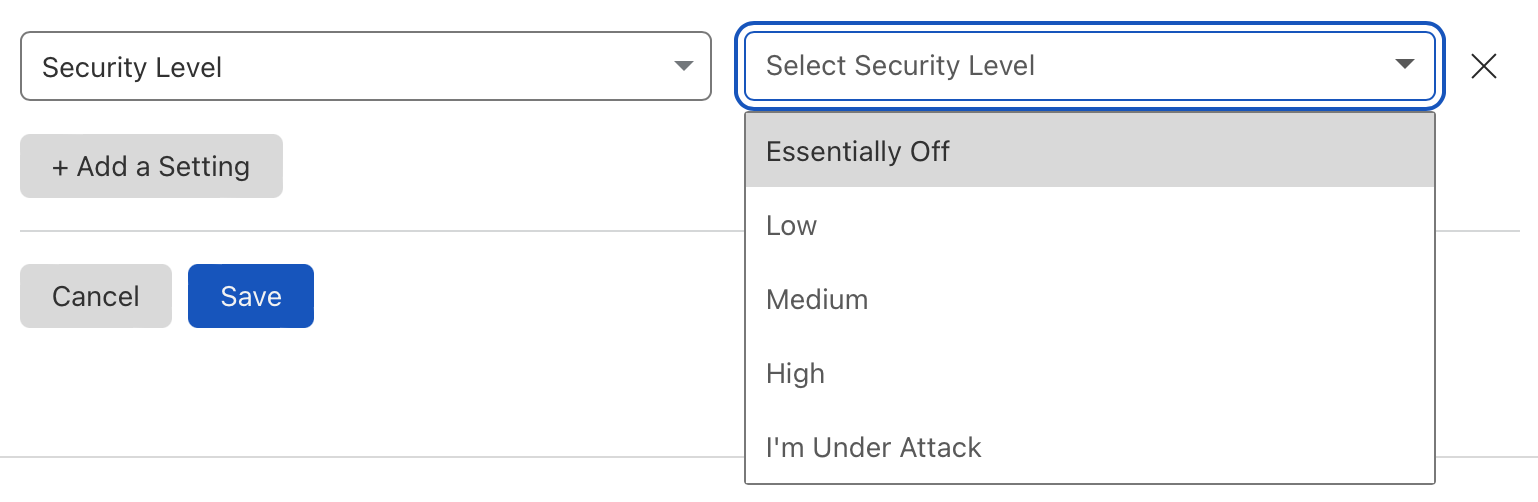
More info here: https://support.cloudflare.com/hc/en-us/articles/200170056-Understanding-the-Cloudflare-Security-Level
I will revisit now.
is it possible to disable security entirely?
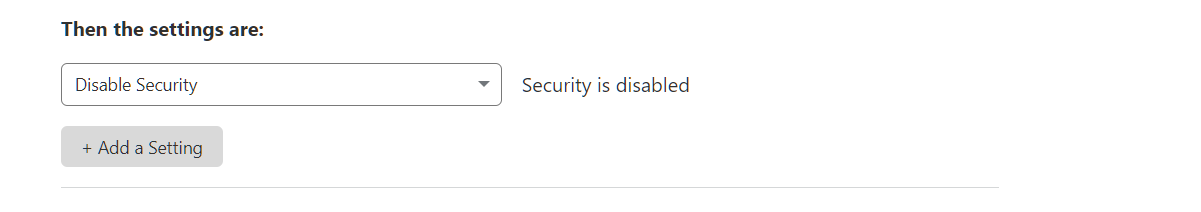
I don't feel like this is going to help contribute to a solution (because after reading it I don't see anything that can address this issue), but it's Cloudflare guide on how to deal with CAPTCHA, so, I feel like it's a least related enough so that I post it. Community Tip - Best Practices For Captcha Challenges
Hello! Did anything change today? We've started getting cloudflare captchas on a few of our projects. They are hosted on platform.sh, so i fear a lot more projects will start getting impacted soon..
Did anything change today?
No changes as far as I am aware of. Let me check the audit log.
Edit: other than automated purge events, I see nothing of interest. This applies to at least the last 10 days.
Hello! Did anything change today? We've started getting cloudflare captchas on a few of our projects. They are hosted on platform.sh, so i fear a lot more projects will start getting impacted soon..
Indeed. This problem effected some projects hosted on Platform.sh. Our public incident report => https://status.platform.sh/incidents/bp6khw4pm490
Cloudflare was returning 403 to build containers on some project using nodejs.org domain.
It's now working properly. An RCA will be published as soon as it's available. Usually it takes 2 weeks to publish.
It's now working properly. An RCA will be published as soon as it's available. Usually it takes 2 weeks to publish.
Does this mean the issue is resolve? I'm not 100% sure having read through the issue.
It's now working properly. An RCA will be published as soon as it's available. Usually it takes 2 weeks to publish.
Does this mean the issue is resolve? I'm not 100% sure having read through the issue.
Calls to nodejs.org might still get CAPTCHA, from any server, if Cloudflare decide to block the host, for whatever reasons. Which can include Platform.sh servers, but isn't happening at the moment. So, it resolve for us and our customers.
This issue is stale because it has been open many days with no activity. It will be closed soon unless the stale label is removed or a comment is made.
This is still an occasional, albeit rare, issue.
This issue is stale because it has been open many days with no activity. It will be closed soon unless the stale label is removed or a comment is made.
Bump, until captchas are completely disabled on endpoints that are expected to be used programmatically.
Now that we have an enterprise account, here's what I suggest we enable:
/cc @nodejs/build @nodejs/web-infra
That rule sounds good to me. Is that a Security Rule?
It's a Configuration Rule: https://dash.cloudflare.com/07be8d2fbc940503ca1be344714cb0d1/nodejs.org/rules/configuration-rules
Looks good to me.
Awesome, that seems perfect!
+1 to the proposed rule change.
+1 on the proposed rule addition
The new rule is enabled.