terraform-provider-github
 terraform-provider-github copied to clipboard
terraform-provider-github copied to clipboard
Adding in support to programatically give teams access to Dependabot and security alerts
Current Terraform Version
14.5
Use-cases
We have recently migrated our repositories to GitHub and we are currently managing our repositories and user access via Terraform. We have recently enabled security scanning and Dependabot alerts on our repositories but have had to give the relevant teams membership to this resource manually (which is very time consuming).
It would be fantastic if there could be terraform that would enable us to do this.
Proposal
The solution could be in the form of a resource block e.g.:
resource "github_security_alerts_membership" "membership_for_repository_x" { repository = "" team_id/user_id = "" }
This doesn't seem possible currently, because there is no API to manage this. I've reached out to GitHub support regarding this, and there's a GitHub Community Post for the same as well: https://github.community/t/please-enable-api-based-permission-management-to-dependabot-vulnerability-alerts/174273/2
I wrote a shell script to automate this for now, but this really needs to be an org-wide setting.
Script: https://gist.github.com/captn3m0/8806a2b7943657c39cc42502560a0f9f
For code scanning Github api is available https://docs.github.com/en/rest/reference/repos#update-a-repository, security_and_analysis parameter.
It would be great to be able to control access to Dependabot Alerts at the repository level using Terraform.
+1 to this, we manage enough repositories that doing this by hand will be painful.
There is a new org-level "Security Manager" setting that works well, but grants read-only access to all repositories instead.
https://github.com/organizations/:org/settings/security_analysis
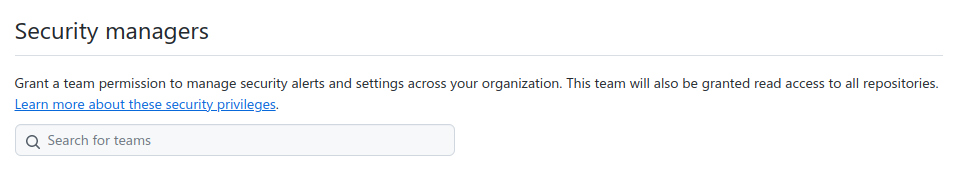
Doc: https://docs.github.com/en/organizations/managing-peoples-access-to-your-organization-with-roles/managing-security-managers-in-your-organization
There's also a big caveat around read-access:
Warning: Removing the security manager role from a team will remove the team's ability to manage security alerts and settings across the organization, but the team will retain read access to repositories that was granted when the role was assigned. You must remove any unwanted read access manually.
👋 Hey Friends, this issue has been automatically marked as stale because it has no recent activity. It will be closed if no further activity occurs. Please add the Status: Pinned label if you feel that this issue needs to remain open/active. Thank you for your contributions and help in keeping things tidy!
That's nice, wait long enough and requests for enhancement just magically disappear! :roll_eyes:
@antgel It's the AI, you f**l
👋 Hey Friends, this issue has been automatically marked as stale because it has no recent activity. It will be closed if no further activity occurs. Please add the Status: Pinned label if you feel that this issue needs to remain open/active. Thank you for your contributions and help in keeping things tidy!
Well, we have had some activity, some labels and moving around has come and gone. #badbot
On my organization we defined a custom-role and assign that to the team/repository relationship
resource "github_organization_custom_role" "fonoa_write" {
name = "write-and-alerts"
description = "Custom role that uses the write role as its base and extend with access to alerts"
base_role = "write"
permissions = [
"resolve_secret_scanning_alerts",
"view_secret_scanning_alerts"
]
}
resource "github_team_repository" "repository_owner" {
team_id = a_team.id
repository = github_repository.repository.name
permission = "write-and-alerts"
}
I hope this helps to solve the issue through terraform
👋 Hey Friends, this issue has been automatically marked as stale because it has no recent activity. It will be closed if no further activity occurs. Please add the Status: Pinned label if you feel that this issue needs to remain open/active. Thank you for your contributions and help in keeping things tidy!