terraform-provider-bigip
 terraform-provider-bigip copied to clipboard
terraform-provider-bigip copied to clipboard
Define Application Security Policy for Virtual Server
Hi, I'd like to choose and apply an existing Application Security Policy to a particular Virtual Server. I couldn't find the right option in the docs of this provider. Is defining this currently supported by the provider?
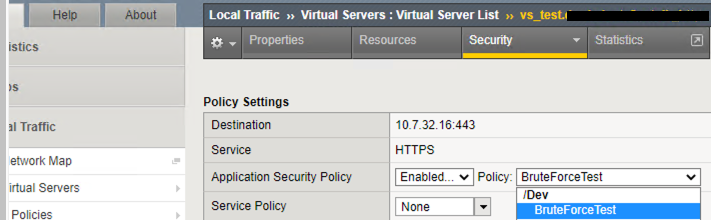
How to configure it in the GUI (see screenshot below):
- select Local Traffic -> Virtual Servers -> Select your virtual server -> Security -> Application Security Policy, choose Enabled and select a policy from the list.
Created INFRAANO-508 for internal tracking.
The functionality is already there, ASM policies are attached to virtual servers via ltm policies. When you do this in the GUI where you follow the steps in description, under the hood the system creates published LTM policy with the name (asm_auto_l7_policy__test )
In which the requested ASM policy is associated. The same can be achieved by first creating ltm policy rule using resource_bigip_ltm_policy resource and then using it to update/create desired virtual server, see below example:
resource "bigip_ltm_policy" "test-policy" {
name = "my_policy"
strategy = "first-match"
requires = ["http"]
published_copy = "Drafts/my_policy"
controls = ["asm"]
rule {
name = "default" action {
asm = true
enable = true
request = true
policy = "/Common/foo-policy"
}
}
}
resource "bigip_ltm_virtual_server" "test-vs" {
name = "my_vs"
destination = "10.255.255.254"
description = "VirtualServer-test"
port = 9999
mask = "255.255.255.255"
source_address_translation = "automap"
ip_protocol = "tcp"
profiles = ["/Common/http"]
client_profiles = ["/Common/tcp"]
server_profiles = ["/Common/tcp-lan-optimized"]
default_persistence_profile = "/Common/hash"
fallback_persistence_profile = "/Common/dest_addr"
policies = [bigip_ltm_policy.test-policy.name]
depends_on = [bigip_ltm_policy.test-policy]
}
Hi, bigip_command or FAST HTTP/HTTPS resources can be used to achieve this, thanks!
Closing this request now. Please re-open if required or send an email to [email protected]. Thanks!