dex
 dex copied to clipboard
dex copied to clipboard
Multiple CVEs in the latest explicit v2.31.2
Preflight Checklist
- [X] I agree to follow the Code of Conduct that this project adheres to.
- [X] I have searched the issue tracker for an issue that matches the one I want to file, without success.
- [X] I am not looking for support or already pursued the available support channels without success.
Version
2.31.2
Storage Type
Kubernetes
Installation Type
Official Helm chart
Expected Behavior
There are critical vulnerabilities (listed down below) have been existing through multiple versions of dexidp/dex : v2.30.2, v2.31.1 and the latest v2.31.2.
- CVE-2022-24675
- CVE-2022-28327
- CVE-2022-24921
- CVE-2022-23806
- CVE-2022-23773
- CVE-2022-23772
- CVE-2021-41771
What I need is to know your current remediation plan to fix those CVEs for the next release, if possible.
Actual Behavior
- CVE-2022-24675
- CVE-2022-28327
- CVE-2022-24921
- CVE-2022-23806
- CVE-2022-23773
- CVE-2022-23772
- CVE-2021-41771
Steps To Reproduce
No response
Additional Information
No response
Configuration
No response
Logs
Scan results for: image dexidp/dex:v2.31.2 sha256:19aa8c9029c016db0c965769809ed23877be3f9f8337914e34c81617abf8efa4
[07:23:46][Step 2/2] Vulnerabilities
[07:23:46][Step 2/2] +----------------+----------+------+---------+---------+--------------------------+------------+------------+----------------------------------------------------+
[07:23:46][Step 2/2] | CVE | SEVERITY | CVSS | PACKAGE | VERSION | STATUS | PUBLISHED | DISCOVERED | DESCRIPTION |
[07:23:46][Step 2/2] +----------------+----------+------+---------+---------+--------------------------+------------+------------+----------------------------------------------------+
[07:23:46][Step 2/2] | CVE-2021-38297 | critical | 9.80 | go | 1.17.1 | fixed in 1.17.2, 1.16.9 | > 7 months | < 1 hour | Go before 1.16.9 and 1.17.x before 1.17.2 has a |
[07:23:46][Step 2/2] | | | | | | > 7 months ago | | | Buffer Overflow via large arguments in a function |
[07:23:46][Step 2/2] | | | | | | | | | invocation from a WASM module, when GOARCH=wasm |
[07:23:46][Step 2/2] | | | | | | | | | GOOS... |
[07:23:46][Step 2/2] +----------------+----------+------+---------+---------+--------------------------+------------+------------+----------------------------------------------------+
[07:23:46][Step 2/2] | CVE-2022-23806 | critical | 9.10 | go | 1.17.1 | fixed in 1.17.7, 1.16.14 | > 3 months | < 1 hour | Curve.IsOnCurve in crypto/elliptic in Go before |
[07:23:46][Step 2/2] | | | | | | > 3 months ago | | | 1.16.14 and 1.17.x before 1.17.7 can incorrectly |
[07:23:46][Step 2/2] | | | | | | | | | return true in situations with a big.Int value |
[07:23:46][Step 2/2] | | | | | | | | | that i... |
[07:23:46][Step 2/2] +----------------+----------+------+---------+---------+--------------------------+------------+------------+----------------------------------------------------+
[07:23:46][Step 2/2] | CVE-2022-28327 | high | 7.50 | go | 1.17.1 | fixed in 1.18.1, 1.17.9 | 41 days | < 1 hour | The generic P-256 feature in crypto/elliptic in |
[07:23:46][Step 2/2] | | | | | | 41 days ago | | | Go before 1.17.9 and 1.18.x before 1.18.1 allows a |
[07:23:46][Step 2/2] | | | | | | | | | panic via long scalar input. |
[07:23:46][Step 2/2] +----------------+----------+------+---------+---------+--------------------------+------------+------------+----------------------------------------------------+
[07:23:46][Step 2/2] | CVE-2022-24921 | high | 7.50 | go | 1.17.1 | fixed in 1.17.8, 1.16.15 | 87 days | < 1 hour | regexp.Compile in Go before 1.16.15 and 1.17.x |
[07:23:46][Step 2/2] | | | | | | 87 days ago | | | before 1.17.8 allows stack exhaustion via a deeply |
[07:23:46][Step 2/2] | | | | | | | | | nested expression. |
[07:23:46][Step 2/2] +----------------+----------+------+---------+---------+--------------------------+------------+------------+----------------------------------------------------+
[07:23:46][Step 2/2] | CVE-2022-24675 | high | 7.50 | go | 1.17.1 | fixed in 1.18.1, 1.17.9 | 41 days | < 1 hour | encoding/pem in Go before 1.17.9 and 1.18.x before |
[07:23:46][Step 2/2] | | | | | | 41 days ago | | | 1.18.1 has a Decode stack overflow via a large |
[07:23:46][Step 2/2] | | | | | | | | | amount of PEM data. |
[07:23:46][Step 2/2] +----------------+----------+------+---------+---------+--------------------------+------------+------------+----------------------------------------------------+
[07:23:46][Step 2/2] | CVE-2022-23773 | high | 7.50 | go | 1.17.1 | fixed in 1.17.7, 1.16.14 | > 3 months | < 1 hour | cmd/go in Go before 1.16.14 and 1.17.x before |
[07:23:46][Step 2/2] | | | | | | > 3 months ago | | | 1.17.7 can misinterpret branch names that falsely |
[07:23:46][Step 2/2] | | | | | | | | | appear to be version tags. This can lead to |
[07:23:46][Step 2/2] | | | | | | | | | incorrect ... |
[07:23:46][Step 2/2] +----------------+----------+------+---------+---------+--------------------------+------------+------------+----------------------------------------------------+
[07:23:46][Step 2/2] | CVE-2022-23772 | high | 7.50 | go | 1.17.1 | fixed in 1.17.7, 1.16.14 | > 3 months | < 1 hour | Rat.SetString in math/big in Go before 1.16.14 and |
[07:23:46][Step 2/2] | | | | | | > 3 months ago | | | 1.17.x before 1.17.7 has an overflow that can lead |
[07:23:46][Step 2/2] | | | | | | | | | to Uncontrolled Memory Consumption. |
[07:23:46][Step 2/2] +----------------+----------+------+---------+---------+--------------------------+------------+------------+----------------------------------------------------+
[07:23:46][Step 2/2] | CVE-2021-44716 | high | 7.50 | go | 1.17.1 | fixed in 1.17.5, 1.16.12 | > 5 months | < 1 hour | net/http in Go before 1.16.12 and 1.17.x before |
[07:23:46][Step 2/2] | | | | | | > 5 months ago | | | 1.17.5 allows uncontrolled memory consumption |
[07:23:46][Step 2/2] | | | | | | | | | in the header canonicalization cache via HTTP/2 |
[07:23:46][Step 2/2] | | | | | | | | | requests... |
[07:23:46][Step 2/2] +----------------+----------+------+---------+---------+--------------------------+------------+------------+----------------------------------------------------+
[07:23:46][Step 2/2] | CVE-2021-41772 | high | 7.50 | go | 1.17.1 | fixed in 1.17.3, 1.16.10 | > 6 months | < 1 hour | Go before 1.16.10 and 1.17.x before 1.17.3 allows |
[07:23:46][Step 2/2] | | | | | | > 6 months ago | | | an archive/zip Reader.Open panic via a crafted |
[07:23:46][Step 2/2] | | | | | | | | | ZIP archive containing an invalid name or an empty |
[07:23:46][Step 2/2] | | | | | | | | | fi... |
[07:23:46][Step 2/2] +----------------+----------+------+---------+---------+--------------------------+------------+------------+----------------------------------------------------+
[07:23:46][Step 2/2] | CVE-2021-41771 | high | 7.50 | go | 1.17.1 | fixed in 1.17.3, 1.16.10 | > 6 months | < 1 hour | ImportedSymbols in debug/macho (for Open or |
[07:23:46][Step 2/2] | | | | | | > 6 months ago | | | OpenFat) in Go before 1.16.10 and 1.17.x before |
[07:23:46][Step 2/2] | | | | | | | | | 1.17.3 Accesses a Memory Location After the End of |
[07:23:46][Step 2/2] | | | | | | | | | a Buffe... |
[07:23:46][Step 2/2] +----------------+----------+------+---------+---------+--------------------------+------------+------------+----------------------------------------------------+
[07:23:46][Step 2/2]
[07:23:46][Step 2/2] Vulnerabilities found for image dexidp/dex:v2.31.2: total - 10, critical - 2, high - 8, medium - 0, low - 0
Checking the latest 2.31.2 image:
❯ go version -m dex
dex: go1.17.10
path github.com/dexidp/dex/cmd/dex
The above report doesn't seem to be correct in detecting the Go version used for compiling Dex.
Hi @sagikazarmark , my report was generated with TwistLock. I tried to double check with aquasecurity/trivy, but it seems trivy did not found any CVEs matching to TwistLock .
I am not sure which one to trust here, tbh
As I said, Dex 2.31.2 is built with Go 1.17.10. If twistlock's report says 1.17.1, it's clearly wrong.
hi @sagikazarmark , it seems the version Go 1.17.1 in the CVE report indicates gomplate specifically. This might relates to https://github.com/hairyhenderson/gomplate/issues/1352
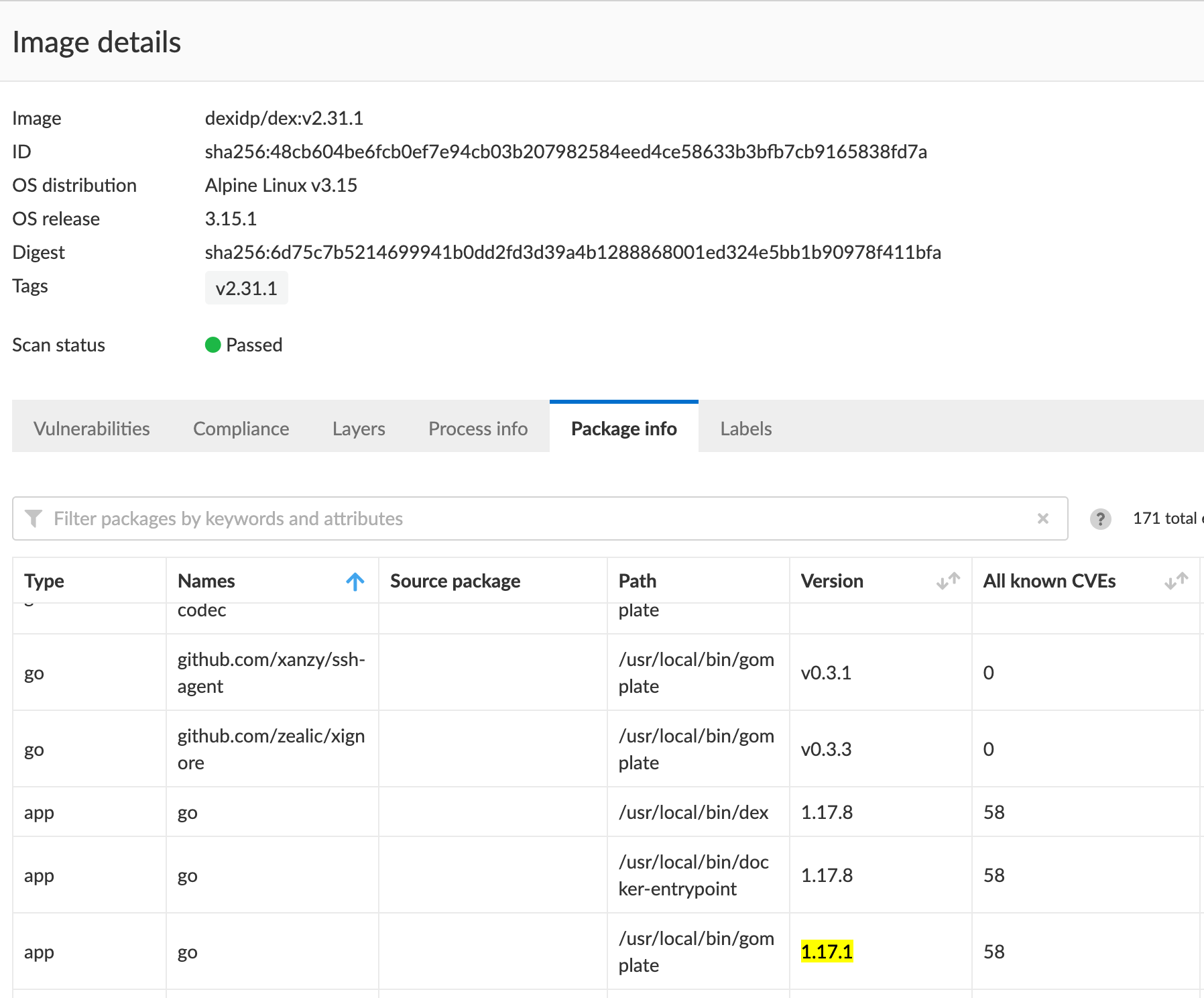
Good catch @tdungnguyen ! We will update gomplate once there is a new release.
Hi @sagikazarmark , by the time I am typing this to you, gomplate has released new version v3.11.0. I did a quick scan of its latest Docker image, and it's clean with CVEs. I think that you should be informed about this. I hope this helps
Hi @tdungnguyen meanwhile gomplate was updated in #2620 to v3.11.2
thank you @petersutter . I guess we have to wait for dexidp/dex repo owners/contributors to update gomplate in their source in the next release date
Good catch @tdungnguyen ! We will update gomplate once there is a new release.
Hello @sagikazarmark , I hope this message finds you well. Could you share with me the next release version of dexidp/dex also be updated with latest version gomplate, like I suggested? I am really looking forward for this to be patched personally :)
Gomplate has already been upgraded to the latest version, so closing.
@sagikazarmark - I am sorry but it seems I keep bringing bad news, but I did a thorough check on the latest versions (v2.33.0 and v2.33.1) but the reported CVEs are still there.
If you can pull those images again to your local, you will see that gomplate version is still be 3.10.0, not 3.11.2 as expected.
dexidp/dex:v2.33.0
△ docker pull dexidp/dex:v2.33.0
Digest: sha256:62902bd3a7ce4a73ed44e28884bffec04bcaa4a07e31e043173bdce289717e80
Status: Downloaded newer image for dexidp/dex:v2.33.0
docker.io/dexidp/dex:v2.33.0
△ docker run -it dexidp/dex:v2.33.0 /usr/local/bin/gomplate -v
gomplate version 3.10.0
dexidp/dex:v2.33.1
△ docker pull dexidp/dex:v2.33.1
v2.33.1: Pulling from dexidp/dex
Digest: sha256:0bbcbe278e007ebf9dca9f92387f9438918ba208c2b833d5660e91eed70f759f
Status: Image is up to date for dexidp/dex:v2.33.1
docker.io/dexidp/dex:v2.33.1
△ docker run -it dexidp/dex:v2.33.1 /usr/local/bin/gomplate -v
gomplate version 3.10.0
Looks like it's been upgraded more recently than I thought.
Thank you for re-opening this issue, Márk! I really look forward to v2.34.0 release. Cheers!
Should be fixed now
➜ ~ docker run -it dexidp/dex:v2.34.0 /usr/local/bin/gomplate -v
Unable to find image 'dexidp/dex:v2.34.0' locally
v2.34.0: Pulling from dexidp/dex
213ec9aee27d: Pull complete
1bc3f461a04c: Pull complete
53b9e8890868: Pull complete
9dd62e817ca2: Pull complete
17362b47fea7: Pull complete
d0b1f33d4435: Pull complete
b10e12597191: Pull complete
e9f6aabe416c: Pull complete
23ab9162d1a1: Pull complete
da42bcda9136: Pull complete
Digest: sha256:72b9cd039152ed5e8c5c745ac62a131b943bec9f9fe0b995e8821a4e35c8522e
Status: Downloaded newer image for dexidp/dex:v2.34.0
gomplate version 3.11.2