vulnerability-rating-taxonomy
 vulnerability-rating-taxonomy copied to clipboard
vulnerability-rating-taxonomy copied to clipboard
Token Impersonation - Different Priority
Issue Background
Vulnerable application allows a user to login using his Google account. However, the backend does not check whether the provided code parameter (token) is generated for vulnerable app or not, so an attacker, who has a Google OAuth app which is used by a user X(victim) and the attacker will get token for the attacker controlled google oauth app for the user X(victim) and then use the token to log into victim user's account on vulnerable app. You can read more information about how to verify the integrity of the ID token here: https://developers.google.com/identity/sign-in/web/backend-auth
This issue was mostly misunderstood by most of the client and set different priorities from P1 to P4 as shown in the screen shots.
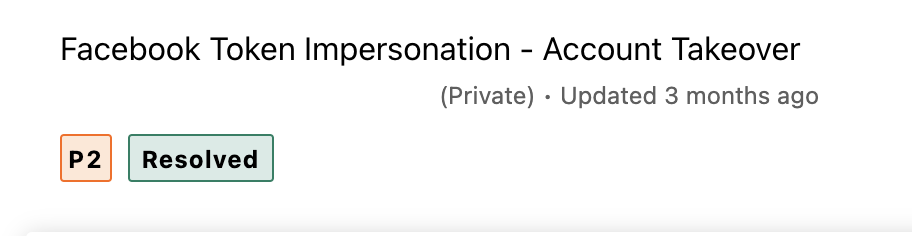
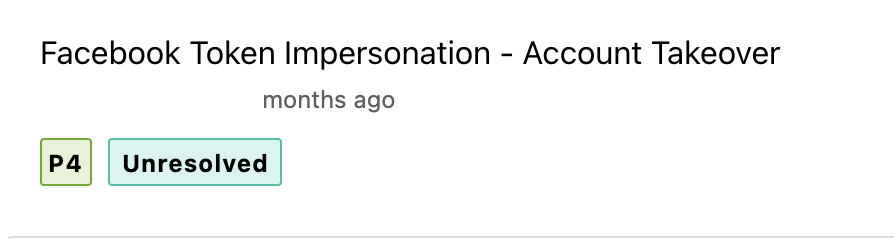
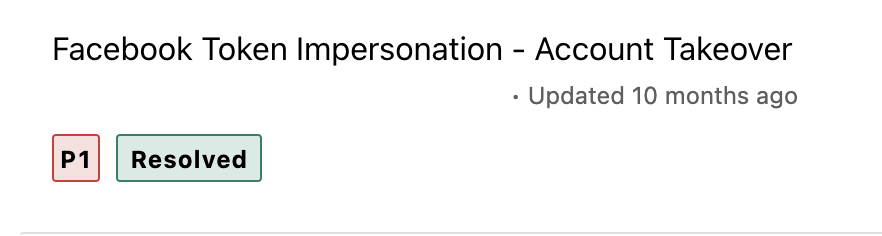
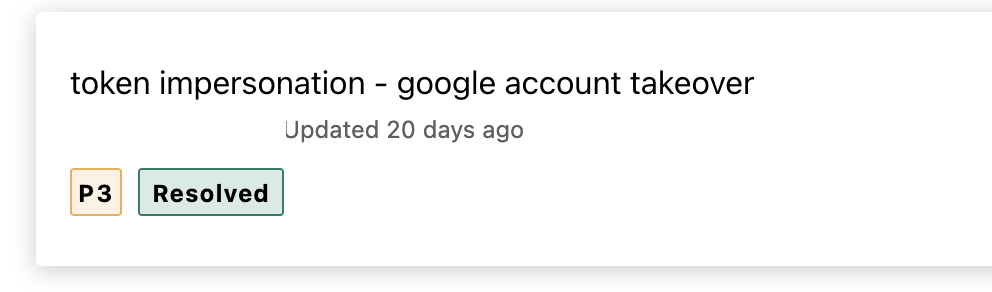
For all the above issues which i reported, the impact and severity was the same. yet, it was wrongly misunderstood by the client. it would be good, if bugcrowd set the standard severity and add it to the VRT taxonomy.
IMO it should be P1/P2. Never ever P3/P4 if account takeover is happening
@harie0x Don't you think it come under Oauth misconfiguration?
yes, it comes under oauth misconfig. but, i do consider it as either P1 or P2.
Hi Guys,
Based on the VRT this is considered P2:

Since you both agree with it being P2, I'm going to close this issue. If there are any other questions/concerns let me know or create a new issue.
-Timmy