samples
 samples copied to clipboard
samples copied to clipboard
How to grant Azure AD Graph API permissions to an Azure AD B2C app registration?
The README in this repo:
https://github.com/azure-ad-b2c/samples/tree/master/policies/B2C-Token-Includes-AzureAD-BearerToken
Instructs users to create an App Registration in an Azure AD B2C tenant.
It then instructs to go to:
App Registrations > [ select your app ] > API permissions > Add a permission
The images in the README are too small to view properly, but they seem to show ALL Graph API permissions are available to be selected.
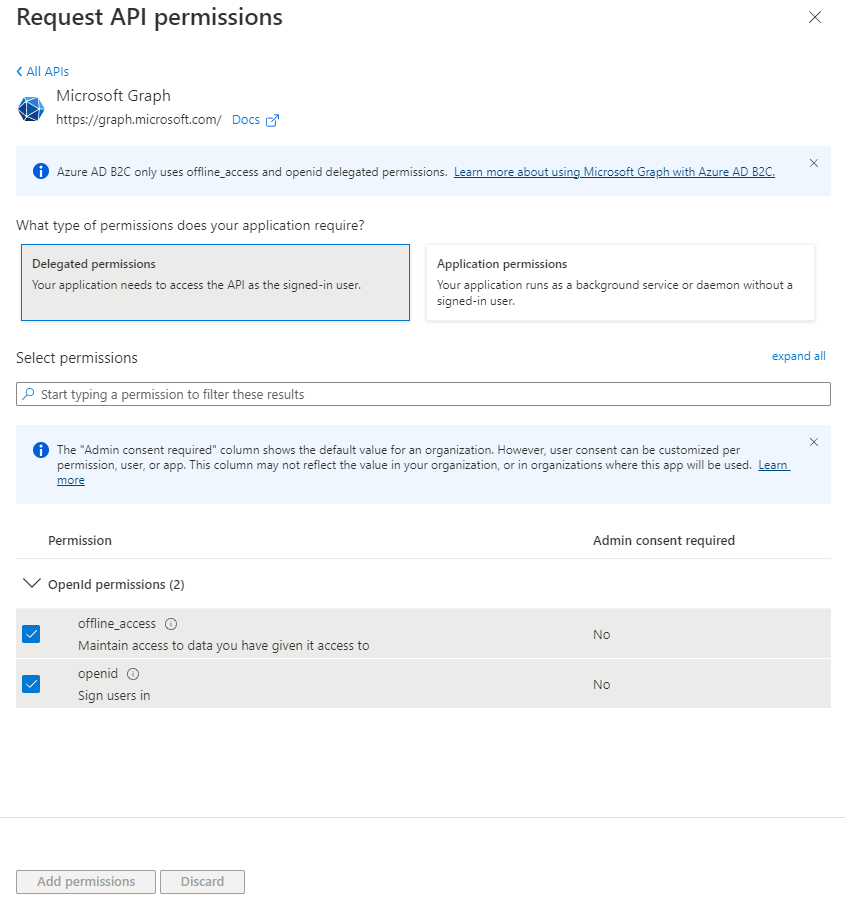
This is confusing because in my Azure AD B2C app registration, I can only choose 2 permissions in Microsoft Graph:
- offline_acess
- openid
As shown in the screenshot below:
I am also confused how this is meant to work, because the overall goal, as stated in the repo, is:
... how to call the Graph API of the users’ home Azure AD tenant using the issued Azure AD Bearer token
So I'm not sure how the Graph API permissions for the Azure AD tenant are meant to be present in the GUI of an Azure AD B2C app registration.
I also tried the call specified at the end of the README and am getting a 403 error:
// the 'response' value is from
// confidentialClientApplication.acquireTokenByCode(tokenRequest).then((response)=>{ ...
req.session.IDPaccessToken = response.idTokenClaims.idp_access_token;
let IDPaccessToken = req.session.IDPaccessToken;
const options = {
headers: {
Authorization: `Bearer ${IDPaccessToken}`
}
};
const response = await axios.get(`https://graph.microsoft.com/v1.0/users/info@<my-tenant-name>.onmicrosoft.com`, options);
The application is a Node.js/Express application.
In Azure AD B2C > App Registrations > [ My App ] > API permissions, Graph API Delegated permissions are only available for offline_access and openid.
When I add Application permissions for User.ReadWrite.All and Directory.ReadWrite.All (with Admin Consent granted), and use the idp_access_token as the Bearer token in the headers of a request to the Graph API, eg:
axios.get('https://graph.microsoft.com/v1.0/users/info@<my-tenant-name>.onmicrosoft.com', options),
I get a 403 error, ERR_BAD_REQUEST.
Additionally, when I decode the idp_access_token at https://jwt.ms, the scopes value (scp) has the value openid profile email - so it doesn't look like the required scopes are being passed through to the idp_access_token.
I then went to Azure AD B2C > Identity Providers > OpenID Connect , and in the Scope field, I changed the value from this:
openid profile
to this:
openid profile User.ReadWrite.All Directory.ReadWrite.All
So now my call to the Graph API gets a response, but I don't know how its doing what its doing.
My instinct tells me whatever I've given it access to do is too powerful.
You created the app reg incorrectly:
From the Azure AD B2C portal, select App registration, create a friendly name for the app, and select the "Accounts in any organizational directory…" under the Supported Account Types.
This type should give access to graph api properly.
I have two App Registrations:
- myWebApp
- myWebAppAPI
Below are the Authentication settings for myWebApp - it seems that it does have the settings you specifiied.
If you look at the screenshot in my original post, there is a notice at the top of the page that says:
Azure AD B2C only uses offline_access and openid delegated permissions.
Learn more about using Microsoft Graph with Azure AD B2C.
So it seems to be saying that only offline_access and openid can be selected when choosing Delegated permissions.
If this is the case, then the README in the sample is not correct.
At step 4, the README specifically says to select Delegated permissions:
- Next select, select API Permission, and select Add Permission. Select Microsoft Graph and select Delegated Permissions.
It would be good if the screenshots in the README were at their actual size.
The images from Step 4 downwards are too small to be able to determine if the tenant they are using is B2C or not.