workload-discovery-on-aws
 workload-discovery-on-aws copied to clipboard
workload-discovery-on-aws copied to clipboard
Additional accounts added to AWS Perspective not scanning
If your issue relates to the Discovery Process, please first follow the steps described in the implementation guide Debugging the Discovery Component
Describe the bug New Accounts that have been added to perspective are not scanning and not resources are been poplulated. I am getting the 500 error for 4 accounts. I suspect a possible SCP might be blocking this as my first account I added was under the Root OU and not in a sub OU like the additional accounts which is working correctly. However all Cloud stack operations where successful .
To Reproduce
Log into AWS Perspective
Expected behavior I should see Last scanned time. At the moment its just showing N/A for the additional accounts.
Screenshots
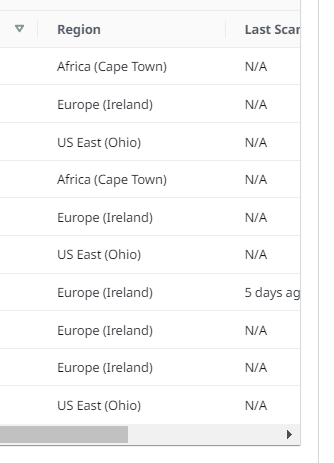
Browser (please complete the following information):
Edge Version 99.0.1150.39
Additional context The Stack Sets created successfully for the Global Settings Template and the Regions Template which was run individually on each account. The Role AWSCloudFormationStackSetExecutionRole has been added to the Target accounts successfully with Trust between Perspective account and target setup correctly. AWS-Perspective-16March2022-log-events-viewer-result.csv
Hi there. My best guess is that the config:PutConfigurationAggregator API is being denied by some policy in the affected account. Unfortunately, this API is fundamental to how Perspective works; I'm not sure how much control you have over the IAM permissions in your org but you'll need to allow it that API to be called.
Hi there. My best guess is that the
config:PutConfigurationAggregatorAPI is being denied by some policy in the affected account. Unfortunately, this API is fundamental to how Perspective works; I'm not sure how much control you have over the IAM permissions in your org but you'll need to allow it that API to be called.
then what do you think about creating the AWS perspective through the root account. I have the same issue
Hi Stefano
Thanks for the reply. I understand what you saying. Just seems rather weird that we Push out the Global and Region Templates from the Perspective Account using CF-Stack into the Target Accounts and that would be missing from the role.
If you look in the IAM Roles on the Target account the only Perspective Role I can see is the ZoomDiscorveryRole and under there is the PerspectiveConfig inline policy which did not have the config:PutConfigurationAggregator.
Below is the updated Json Statement. Would this be the correct Role to update in the Target account. I have a few minutes ago removed the Regions from AWS Perspective Front-End and re-added the the accounts and regions of which the resources where not been shown. Hope for more resources to show up.
{ "Version": "2012-10-17", "Statement": [ { "Action": [ "config:Get*", "config:Deliver*", "config:List*", "config:SelectResourceConfig", "config:PutDeliveryChannel", "config:PutConfigurationAggregator" ], "Resource": "*", "Effect": "Allow" } ] }
HI, Thanks for the reply. I am also having same issue. However, The resources were scanned initially for 20 days , after that the resources scanning were not happening. We didn't change anything in the zoomdiscoveryrole in IAM. Any inputs much appreciated.
I met the same issue after I increased the account from 3 to 5
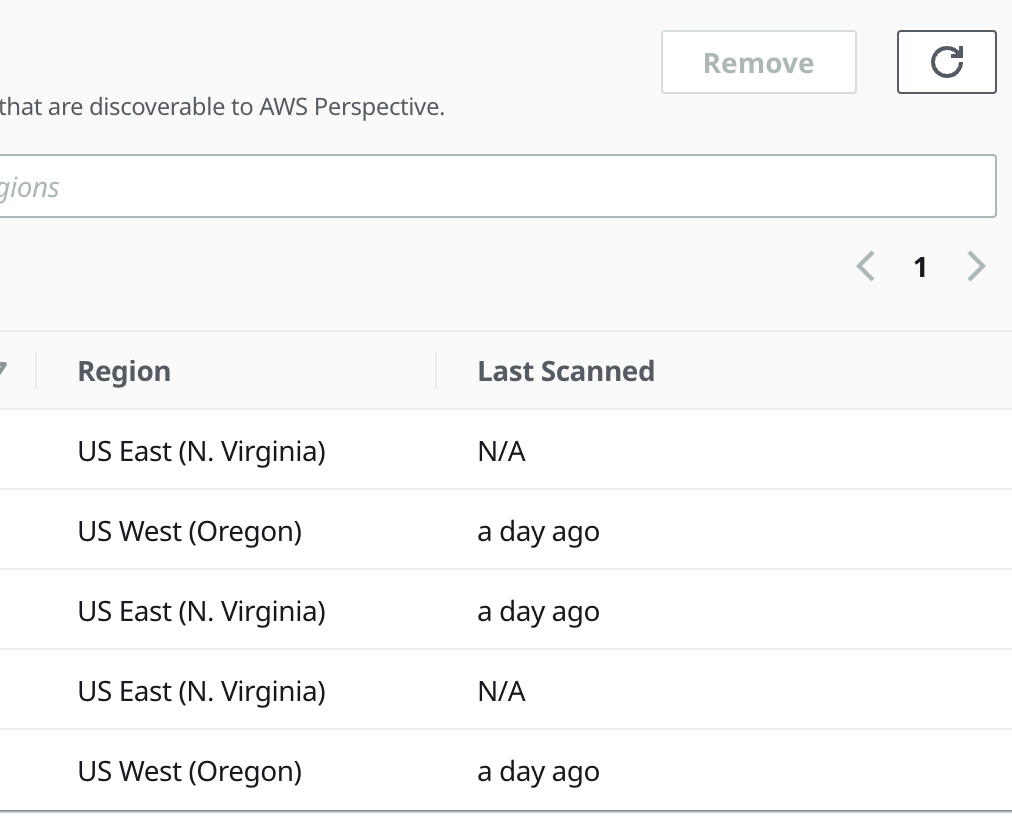
I suspect this issue is due to a scaling limitation with v1.x.x as the discovery process made an API call to AWS Config for every resource it found. For regions with ~2500 resources, this meant Config would start applying rate limiting to these calls and eventually the whole discovery process would hang and not complete. We have addressed this issue in version v2.0.0 and now make far fewer calls to Config when discovering resources. This new version was released today, and the 2500 resource limit no longer applies.
Closing due to inactivity. Please feel free to reopen.