community.zabbix
 community.zabbix copied to clipboard
community.zabbix copied to clipboard
tls_accept and tls_conect needs to be the opposite
... at least for the backend api!
SUMMARY
When configuring encrypted communication between proxy and server, there's a mismatch of tls accept/connect params between the config file and the definition created on the Zabbix backend.
In my test I encrypt communications between proxy and server but I allow unencrypted ones between agents and proxy. This is my config:
TLSConnect=psk
TLSAccept=unencrypted

But when I configure a host with:
zabbix_proxy_name: Proxy test2021
zabbix_proxy_hostname: Proxy test2021
zabbix_proxy_tlspsk_secret: bf59807d14db9d6b8d6e44e9f199
zabbix_proxy_tlspskidentity: 1b3e346a11
this config produces the following in the backend:
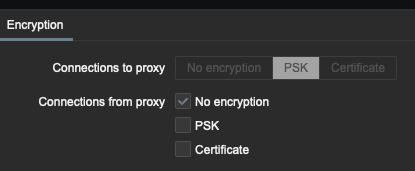
ISSUE TYPE
- Bug Report
COMPONENT NAME
- zabbix_agent
- zabbix_proxy
ANSIBLE VERSION
ansible [core 2.11.6]
config file = /Users/maxxer/work/yetopen-ansible/ansible.cfg
configured module search path = ['/Users/maxxer/.ansible/plugins/modules', '/usr/share/ansible/plugins/modules']
ansible python module location = /usr/local/Cellar/ansible/4.8.0/libexec/lib/python3.10/site-packages/ansible
ansible collection location = /Users/maxxer/.ansible/collections:/usr/share/ansible/collections
executable location = /usr/local/bin/ansible
python version = 3.10.0 (default, Oct 13 2021, 06:44:31) [Clang 12.0.0 (clang-1200.0.32.29)]
jinja version = 3.0.2
libyaml = True
CONFIGURATION
DEFAULT_HOST_LIST(/Users/maxxer/work/yetopen-ansible/ansible.cfg) = ['/Users/maxxer/work/yetopen-ansible/hosts.yaml']
DEFAULT_MANAGED_STR(/Users/maxxer/work/yetopen-ansible/ansible.cfg) = This file is managed by YetOpen with Ansible.
Any manual change will be overwritten.%n
template: {file}
date: %Y-%m-%d %H:%M:%S
user: {uid}
host: {host}
OS / ENVIRONMENT / Zabbix Version
Zabbix 4.0 OS: Ubuntu 20.04
I made a working patch by swapping the params in the plugin, but before submitting a PR I was wondering if it's correct
To be honest, I really don't know. Don't work with encryption (yet). Maybe someone from the community knows?
In agent default configuration file:
- TLSConnect: How the agent should connect to server or proxy. Used for active checks.
- TLSAccept: What incoming connections to accept.
In proxy:
- TLSConnect: How the proxy should connect to Zabbix server. Used for an active proxy, ignored on a passive proxy.
- TLSAccept: What incoming connections to accept from Zabbix server. Used for a passive proxy, ignored on an active proxy.
In host config:
- tls_connect | integer | Connections to host. Possible values are:
- 1 - (default) No encryption;
- 2 - PSK;
- 4 - certificate.
- tls_accept | integer | Connections from host. Possible bitmap values are:
- 1 - (default) No encryption;
- 2 - PSK;
- 4 - certificate.
Proxy config is literally the same.
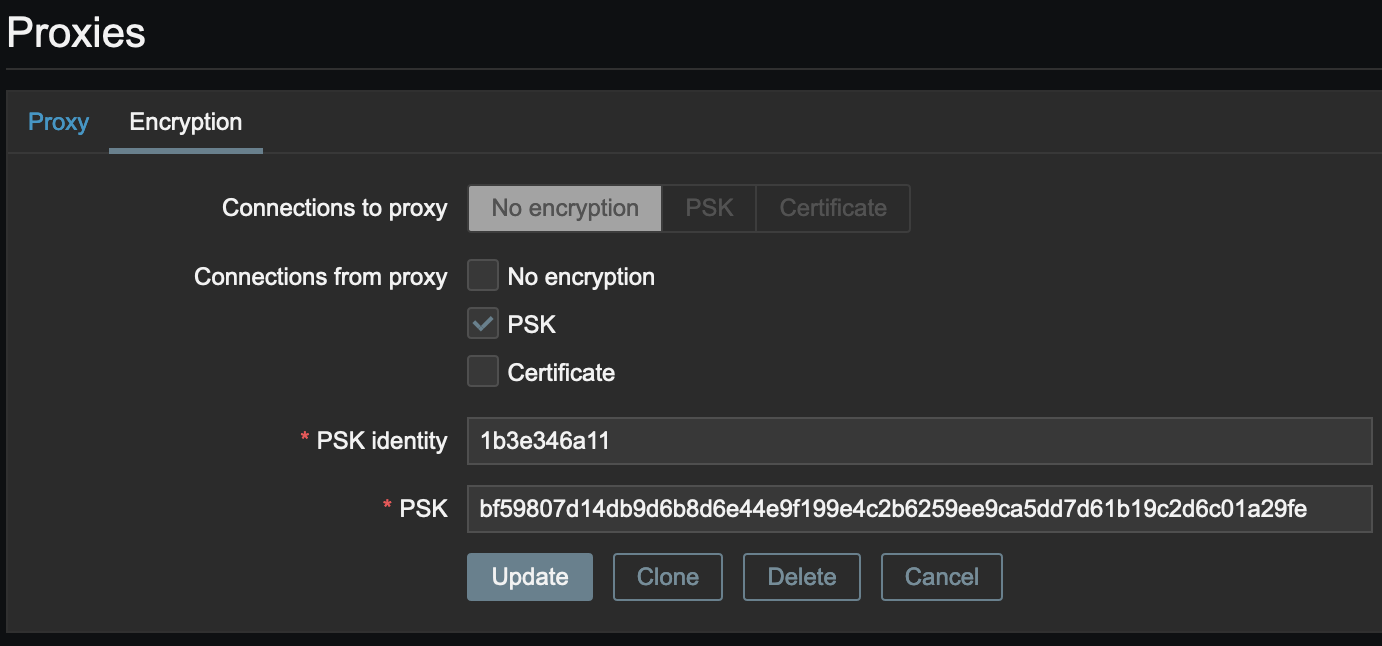
I confirm swapping tls_{accept|connect} when calling the API works. I'm currently creating a proxy with these params:
zabbix_proxy_name: dev-ufficyo
zabbix_proxy_hostname: dev-ufficyo
zabbix_proxy_tlspsk_secret: bf59807d14db9d6b8d6e44e9f199e4c2b6259ee9ca5dd7d61b19c2d6c01a29fe
zabbix_proxy_tlspskidentity: 1b3e346a11
zabbix_api_create_proxy: true
zabbix_proxy_tlsconnect: psk
zabbix_proxy_tlspskfile: /etc/zabbix/monitor.psk
zabbix_install_pip_packages: false
zabbix_proxy_externalscripts: /etc/zabbix/externalscripts
zabbix_proxy_include: /etc/zabbix/zabbix_proxy.d
zabbix_proxy_offlinebuffer: 24
and the following patch creates it correctly on the server:
diff --git a/roles/zabbix_proxy/tasks/main.yml b/roles/zabbix_proxy/tasks/main.yml
index e025617..5c9ba59 100644
--- a/roles/zabbix_proxy/tasks/main.yml
+++ b/roles/zabbix_proxy/tasks/main.yml
@@ -126,8 +126,8 @@
tls_psk: "{{ zabbix_proxy_tlspsk_secret | default(omit) }}"
tls_psk_identity: "{{ zabbix_proxy_tlspskidentity | default(omit) }}"
tls_subject: "{{ zabbix_proxy_tls_subject | default(omit) }}"
- tls_accept: "{{ zabbix_proxy_tls_config[zabbix_proxy_tlsaccept if zabbix_proxy_tlsaccept else 'no_encryption'] }}"
- tls_connect: "{{ zabbix_proxy_tls_config[zabbix_proxy_tlsconnect if zabbix_proxy_tlsconnect else 'no_encryption'] }}"
+ tls_connect: "{{ zabbix_proxy_tls_config[zabbix_proxy_tlsaccept if zabbix_proxy_tlsaccept else 'no_encryption'] }}"
+ tls_accept: "{{ zabbix_proxy_tls_config[zabbix_proxy_tlsconnect if zabbix_proxy_tlsconnect else 'no_encryption'] }}"
validate_certs: "{{ zabbix_api_validate_certs | default(omit) }}"
timeout: "{{ zabbix_api_timeout }}"
when:
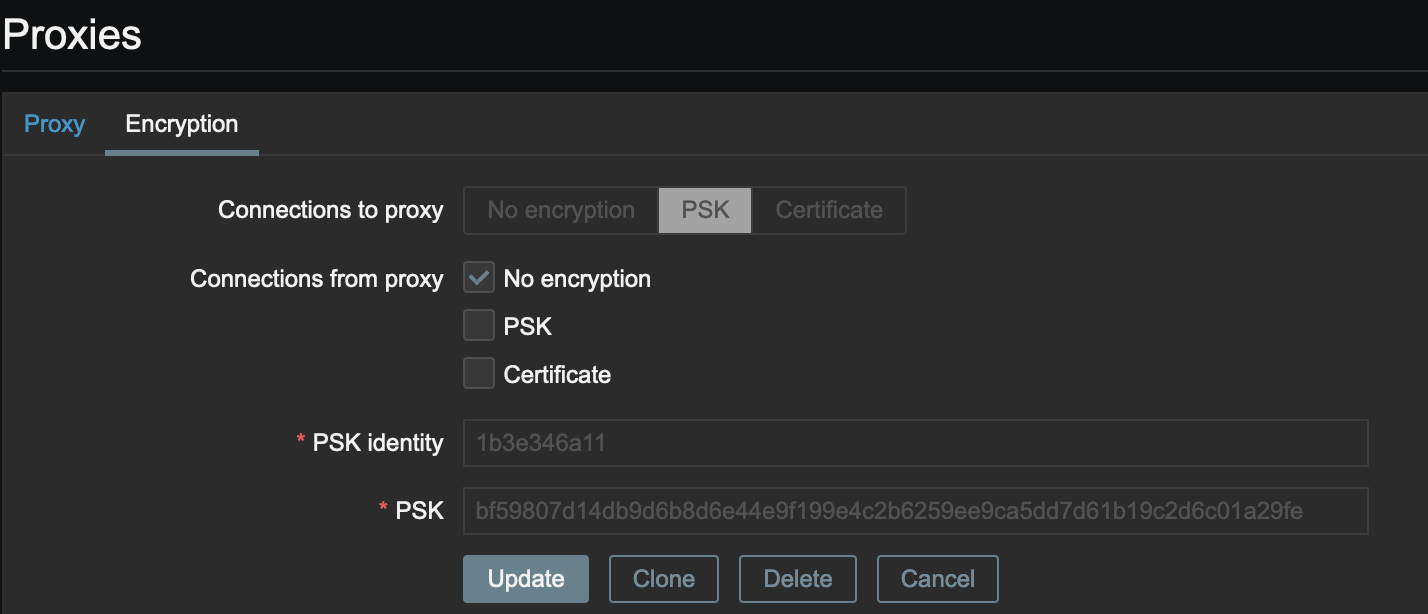
Without the patch it's created this way:
In /etc/zabbix/zabbix_proxy.conf TLS related config is this:
TLSConnect=psk
TLSPSKIdentity=1b3e346a11
TLSPSKFile=/etc/zabbix/monitor.psk
@maxxer Thanks for your great work on this! We are experiencing the exact same issue right now, where we get an API fail because we are trying to use an active proxy with PSK connections from the proxy. Are we thinking this will be in an upcoming release soon?
Can you have a try with the patch above and confirm it works fine? Then maybe we can push for merge
Can you have a try with the patch above and confirm it works fine? Then maybe we can push for merge
I will give it a shot tomorrow, thanks!
Hello, I'm sorry for the super late testing on this. This patch doesn't really help me out, we can't set PSK for both values when the proxy is set to Active, if it was a Passive proxy then we could set both...I think, I'm not an expert in Zabbix yet either.
Actually, I have to go back on what I said, I believe I DO need the patch, and it does seem to be working.
The patch definitely is required to be able to add both passive or active proxies with PSK. Please merge.
@maxxer @daftu where is PR? I can't find it. If there is none then I'll create it. The solution proposed above is correct.
I didn't issue a PR, I wasn't sure about the solution. If you want I'll create one right away
I didn't issue a PR, I wasn't sure about the solution. If you want I'll create one right away
Please do. Don't forget changelog fragment please.
Resolved by #847